
Social Engineering
What is social engineering?
In the context of information security, social engineering is a broad term used to describe the practice of a person or group attempting to deceive or manipulate individuals into supplying personal information or performing certain actions, such as downloading malware.
To manipulate their victim, cybercriminals engage in certain behaviors to help them get to know their targets better: They usually spy on their victims, gather information about them, and then try and create a false sense of security. They may do this by making their victim feel upset that something is wrong with one of their accounts. Or they may try to get to know the victim through a carefully staged introduction where they claim they were trying to contact someone else and made a mistake. Once a false sense of trust is established, it’s easier for them to persuade their target to do things like clicking on links or providing personal information. Examples of common social engineering attacks include phishing, whaling, vishing, and scareware.
Social engineering attacks like these are important to the hackers that use them. While they have many different styles for approaching their targets using various technological methods, they all have one thing in common: They rely on the fact that their victims are people and, therefore, vulnerable to manipulation. In fact, more than 82 percent of cyberattacks leverage the human element to be successful.

How to recognize a social engineering attack: Main characteristics
Social engineering attacks take many forms, making them difficult to recognize if you aren’t aware of what you’re looking at. The attackers use a set of principles and characteristics that influence human behavior. They do this to increase the likelihood of their victim following their plan. However, it’s possible to stay ahead of them by being on the lookout for the characteristics they are attempting to exploit.
Most social engineering attacks contain several traits that help make the attack recognizable. ENISA, the European Union Agency for Cyber Security, identifies six basic principles:

- Authority: The attacker tries to get their target to view them as someone who understands the situation and can convey that understanding. For example, they may pose as a representative from a trusted source like a bank.
- Commitment and consistency: The attacker takes advantage of past behavior to capitalize on future actions. If you act in a similar way, the attacker can use this to target their next push. For example, if the attacker knows their victim always arrives for work at a certain time and uses the same entrance and method of entry, they can use this information to try and gain entry to the building themselves by following their target, showing knowledge of the building and method of entry, and then entering along with the target, rather than using their own credentials.
- Similarity: The attacker attempts to emulate a person the target will think of as being like themselves. They may attempt to find common ground, building a false sense of trust. An example is the “pig butchering scam”, where scammers cold-contact people via text messages or social media, dating, and communication platforms. They start with a simple salutation, and if their recipient responds, scammers make the victim believe they found a potential friend. Then, they boast about the considerable amount of money they earned through cryptocurrency investments and manipulate their victim into investing in their scams.
- Reciprocation is often used by giving something to the target so that they feel the need to give something in return. People like to feel as though they have been given something extra. For example, they may tip higher at a restaurant if the server offers them something small like a free cookie with their check. The same is true in cyberattacks: The hacker may give their victim information or act as if they are doing the victim a favor. This makes the victim want to respond in kind.
- Scarcity: The attacker makes the target feel they need to act quickly because of a time limit. For example, they try to make their victims believe that something they desire is in short supply or only available for a limited time.
- Social validation: Cybercriminals suggest that others have already completed the task successfully so that the target feels more comfortable in undertaking it themselves.
In the IT domain, these traits may also include specific characteristics like:
- Semantic deception: The attacker uses language that deceives the target into taking the wrong meaning from an email or requested action.
- Heightened emotions: The attacker attempts to manipulate the target with potential losses. An example of this is to make you believe you have been locked out of an account unless you provide the necessary information.
- Spoofed sender address: Attackers often register an email address similar to an official one and hope the victims don’t notice the misspelling.
- Phishing link: Once the email has deceived the target into thinking something is wrong and they need to act quickly to avoid negative consequences, the goal is to have the targeted person click on a fraudulent link and enter the sensitive information the attacker wants to collect. By using a sense of authority and replicating what may be a trusted source, the attacker hopes to produce a response from the target before they stop and think.
Why is social engineering so dangerous?
Of all the scams that defraud people and companies of money and sensitive information, social engineering is one of the most dangerous because it relies on tenets of human behavior, including the possibility of user error.
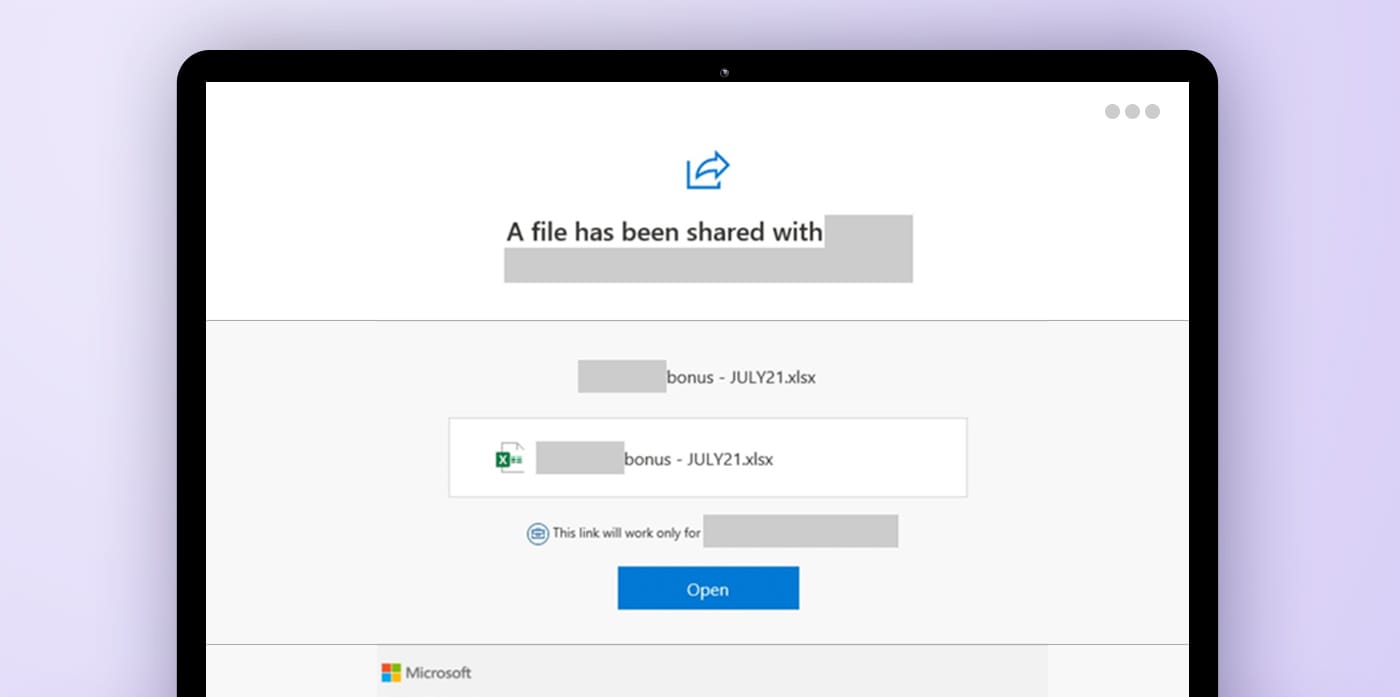
These attacks are becoming increasingly sophisticated and were responsible for up to $6.9 billion in losses in 2021. One example of an extremely successful innovative attack was the Microsoft 365 phishing scam. In this attack, targets received an email with what appeared to be a link to an Excel file and a comment on a cost revision. When clicking on the link, it took the victims to an HTML site that used remote JavaScript code to create a pop-up that told the victim they had been logged out of their account and prompted them to log in. Because the attack had so many layers and steps before the actual request for information, many people fell for it through simple human error, believing it would have been revealed earlier if it were a scam.
Because hackers take the time to understand their targets and their anticipated behavior, social engineering can be extremely dangerous by using this knowledge against potential victims. This technique is known as spear phishing, where hackers personalize their attacks toward a single victim rather than casting a wide net. The attackers may spend months gathering information about their victims before carrying out these attacks. They gather personal information from many different avenues – including physical ones like trash – to better know their target before attacking. The more influential and important the victim is, such as the CEO of a company, the higher the chances of hackers applying spear phishing techniques to manipulate them.
While attacks used to be confined to email, hackers now use other platforms and social media sites. Cybercriminals may contact their victims through apps like Discord or WhatsApp. In fact, phishing can now hide almost anywhere, even in seemingly harmless browser notifications. As the attacks come in so many forms, it can be harder to identify and avoid them. On the other hand, artificial intelligence (AI) is gradually permeating into our everyday lives, and cybercriminals quickly realized that it can be used for social engineering attacks as a prime opportunity to maximize their profits. Using voice cloning, deepfakes, AI-powered password-guessing, and generative AI tools like ChatGPT is boosting the scale of cyberattacks by the minute, and individuals and organizations are far from being prepared against them.
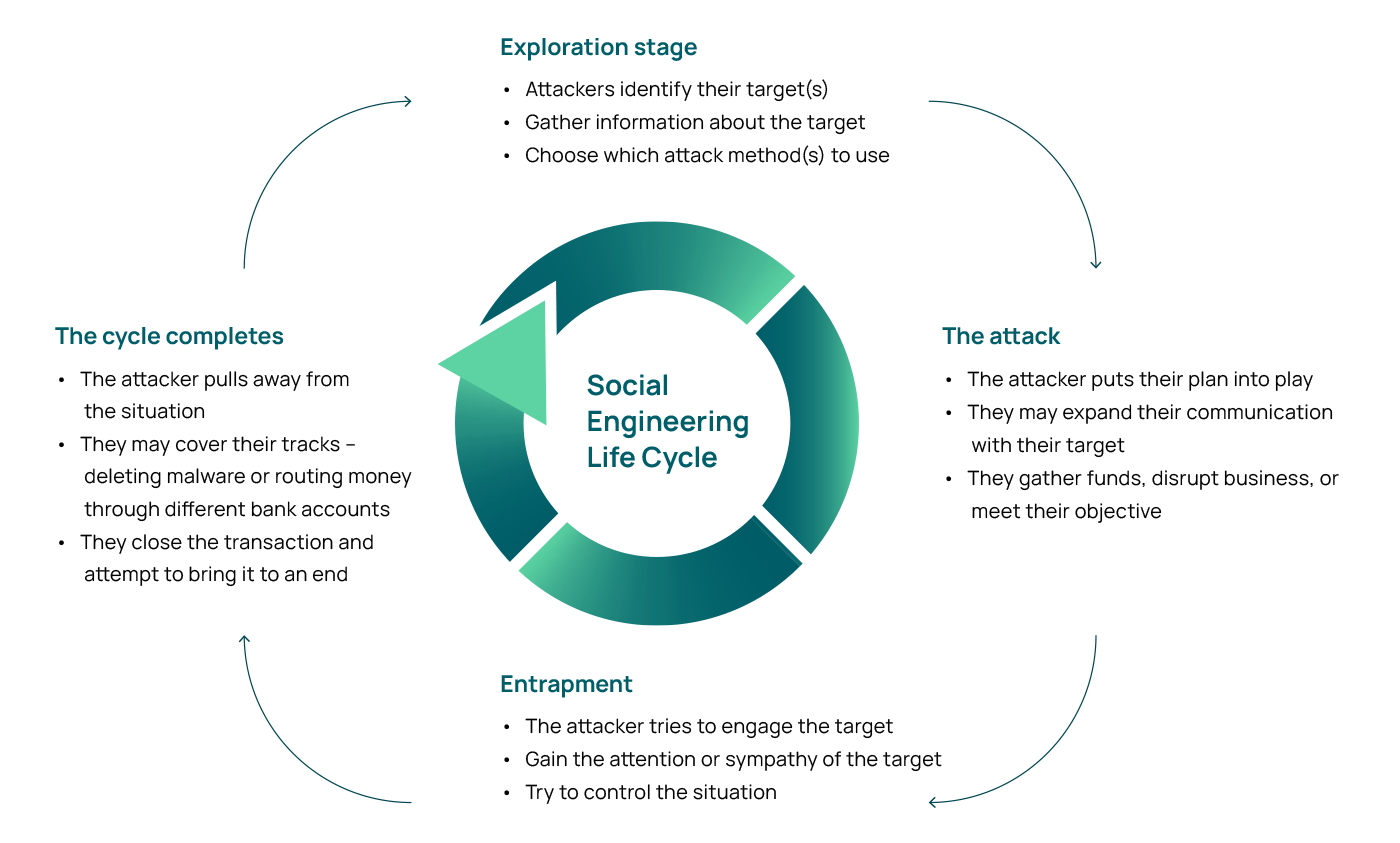
The life cycle of a social engineering attack
Social engineering attacks often follow a pattern. They begin with the investigation of their proposed target in the exploration stage. When spear phishing, they may identify a single person as their victim and begin gathering information. Or, if they are targeting a company or group, they may gather information about a group of employees who work at the company. The information gathered may include things like daily habits and behaviors and frequently used social media sites, passwords, and apps, which help them choose the correct attack method for the target.
Once this stage is complete, the attacker will attempt to ensnare their intended victim. During this entrapment stage, they reach out to the target, try to gain their sympathies or attention, and attempt to control the situation. They may pose as an authority, attempt to find common ground with their target, or try to provoke an emotional response. Once the target is hooked, the scam moves to the next stage.
At this point, the scam is active. The attacker expands their control over the target, executes the attack, and achieves their final goal, which may be to siphon funds from the victim or disrupt their business. When the attack is complete, the cycle concludes. The attacker will attempt to close the connection, ideally without the target being aware of what’s going on. They may remove any trace of used malware and attempt to cover their tracks so that you won’t be able to trace them.
One example of how this life cycle can play out is the attack on Cabarrus County in North Carolina, where hackers managed to appropriate more than $2.5 million in government funds. The county was in the process of funding the construction of a new high school – information the hackers obtained. They determined how the project was being paid for and the contact information of those in charge. The hackers sent a series of emails requesting that the bank information be changed for the next payment. Once payment was made to the false account, the hackers transferred it through a series of other accounts to hide their trail. The scam was only caught once the real contractors contacted the office about a missing payment.
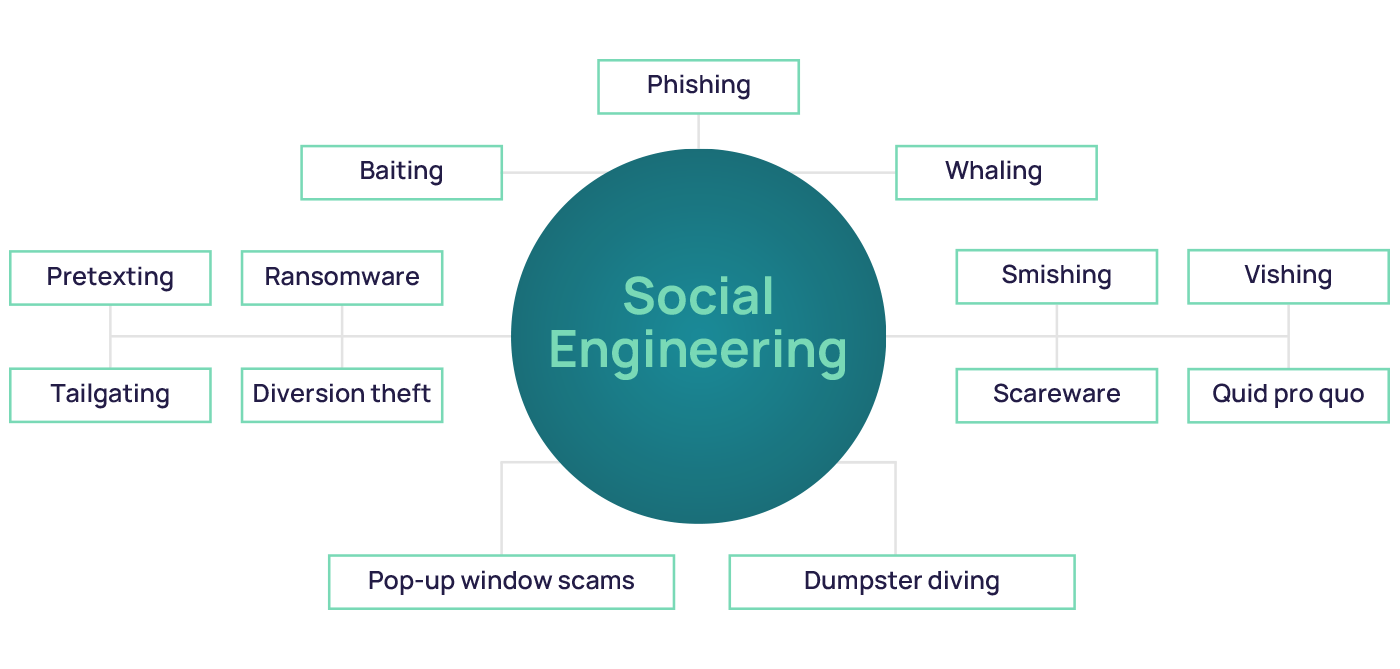
Social engineering techniques
Social engineering is a broad term encompassing many different techniques, and some of them break down into further categories or have similar and related names. Each has specific characteristics to be aware of and varies in their demographics and how and when they are carried out. The most common attacks include:
- Phishing: A scam where cybercriminals try to steal access credentials, bank information, or other sensitive data – usually via email, although more channels are leveraged daily.
- Whaling: An even more targeted phishing attack, usually aimed at a senior executive who may be authorized to release more funds or more sensitive information.
- Vishing: An attack carried out by phone – voice phishing. Vishing seeks to manipulate victims by using personal information gained through the calls to make their targets divulge the desired information.
- Smishing: A phishing attack carried out by text messaging. The text may try to persuade the victim to call a number or follow a link within the text message.
- Baiting: An attack that promises something free to persuade the target to respond. For example, a hacker will promise a free song or movie download in return for setting up an account or clicking a link.
- Pretexting: The hacker comes up with a story or scenario before the attack that will sound believable or plausible to their victim. They use this scenario to manipulate their victim, creating a false sense of trust.
- Tailgating: An attack that takes place in a physical, usually secure or password-protected, location. Once the victim has been identified as part of a large organization, attackers attempt to follow the unsuspecting person inside.
- Ransomware: Malware that renders a victim’s files or systems unusable, usually by encrypting them. Cybercriminals demand a ransom with the promise of releasing the data or system.
- Dumpster diving: A method used to gather sensitive information, such as passwords, access codes, and phone lists, by looking through physical trash.
- Quid pro quo: A means of obtaining something in exchange for something else. An attacker may offer something like “tech support” in exchange for getting access to sensitive systems.
- Pop-up window scams: Attackers create fake pop ups, sometimes informing the victim that their system has been infected with ransomware. Sometimes, the pop up results from malware, while at other times, it may come from a website. They often include a link to a spoofed website.
- Diversion theft: In these attacks, the victim is tricked into sending information to what they thought was a trusted source. They may do this by spoofing an email or creating a false sense of trust and familiarity.
- Scareware: This attack tries to convince the victim to download or purchase malware by claiming it has detected viruses or malware on the victim’s computer to solve the issue.
Real-life examples of social engineering attacks
Social engineering attacks can target anyone, and they can be disguised in various ways to make people give them the information they are after. Sometimes, the target is a CEO or important person within a company. Other times, the victims may simply get caught in a wider net.
Political spear phishing attacks
Political parties are not excluded from being targeted by cybercriminals, especially when an election is about to occur. Having access to sensitive information may allow attackers to either manipulate electoral results or sell the information they gathered at an extremely high price. For example, they may try and obtain data about a political candidate or event that can be used against that candidate by their opponent. An example of this serious social engineering attack was undertaken during the 2016 US elections. Hackers used spear phishing attacks to target people in the Democratic party. Using fake emails, they attempted to have their targets change their email information, giving the hackers access. They could then gather sensitive information about the Clinton campaign that would not have been otherwise available.
Social media scams
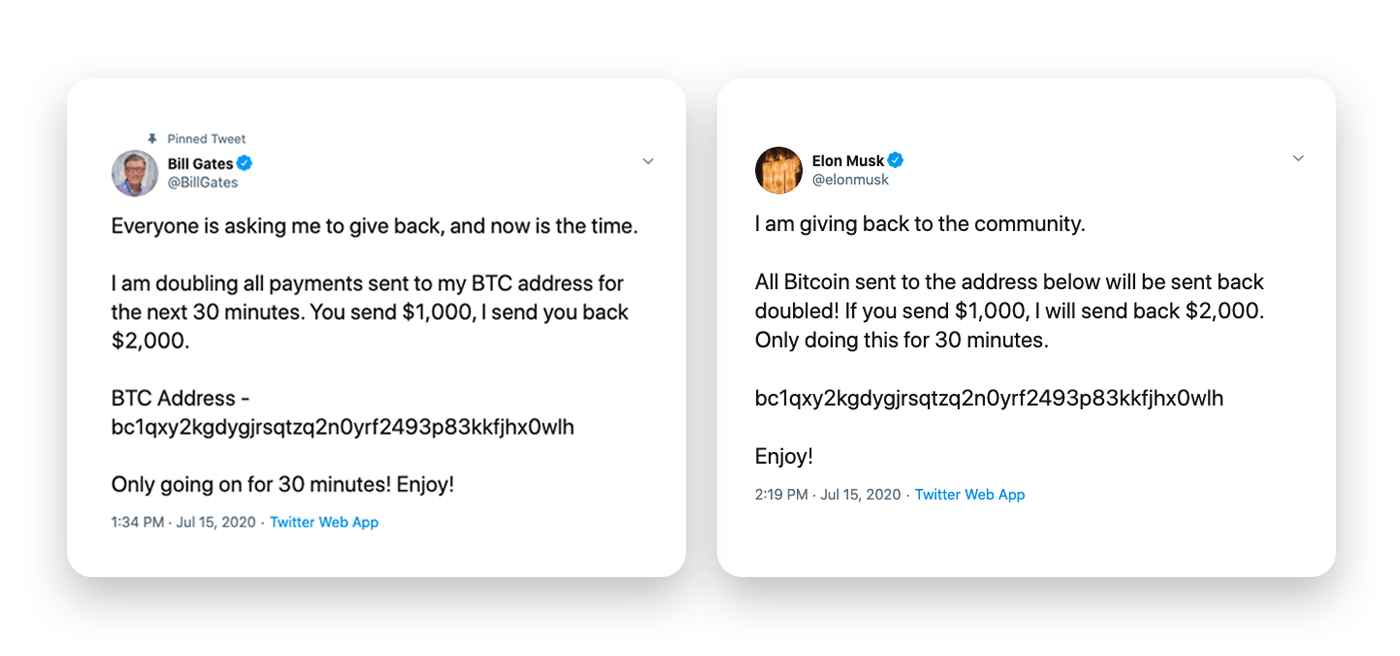
Social media is one avenue that hackers use to reach large numbers of people simultaneously. This is particularly easy to do if the hacker can take over or impersonate an account that already has trust among users, such as a politician or celebrity. One example of this attack was the Twitter bitcoin scam in 2020. Hackers gained information from within Twitter that allowed them to impersonate more than 100 accounts, including those of celebrities and politicians. While one aim was to access direct messages and gain information, the scam also collected more than $121,000 in bitcoin by having trusted accounts, such as Bill Gates and Elon Musk, claiming that a modest investment would get increased returns.
Healthcare scams
The sale of healthcare information is very profitable for hackers because it often contains sensitive information like social security numbers, health insurance, and patients’ health conditions. If a hacker can obtain large amounts of information from a healthcare site, they can sell it to a third party who can use it. Hackers may also use ransomware, knowing the target may be willing to pay to get that information back due to their countries’ privacy acts. Ransomware attacks on healthcare are so prevalent they are estimated to have more than doubled in five years. For example, hackers stole health information from more than 147,000 patients through Scripps Health in 2021, costing the organization nearly $113 million.
How to spot social engineering attacks
To avoid becoming a victim, people must be suspicious of unsolicited encounters with potential scammers. Any time you open an email, read a strange text, or accept a phone call from someone you don’t know, ask yourself the following questions to see if you can spot a scam.
- Are you feeling anxious, emotionally invested in a situation or story, or do you feel your emotions are heightened in any way?
Social engineers try to prey on the emotions of their victims to manipulate them into doing what they want. - Did the message come from a legitimate sender or someone you know?
This can be hard to spot because many attackers create emails and fake webpages that are very convincing. To avoid falling for a scam, call the person or institution yourself or type the website address into your browser rather than relying on links. - Does the website have odd details, or does it look different from how you remember it?
If you clicked on a link or were sent to a website, try to see if anything about it seems off. You can always type the address in directly to compare if something seems wrong. - Does the offer or claim they are making seem too good to be true?
Maybe they promise a return on an investment, or it looks like a way to refinance or get a better deal on an existing account. If it seems too good to be true, it likely is. If these deals were unsolicited, contact the organization they claim to be from directly to follow up. - Can the person prove their identity?
If the person contacting you claims to be someone vulnerable in need of help or from an organization you do business with, have them confirm their identity. Having a third party verify the person’s identity or contacting the organization yourself are methods to do this.
How can you protect yourself from social engineering?
Social engineering relies on a human connection to be successful. They either need the victim to feel personally connected to them or to trust the sense of authority the hacker is attempting to create. And because social engineers can continuously change their game and layer in additional factors that make it harder for their victims to recognize, it can seem difficult to protect yourself. However, there are ways you can do so that go a long way toward thwarting social engineers from making you one of their targets.
In addition to staying vigilant of the signs of a social engineering attack, you can take several other steps to help protect yourself. These include:
- Using social media responsibly. Make your settings private whenever possible, and don’t discuss identifying information, including the name of your workplace or employer. Be careful when sharing information that could be used in creating a password, such as pet names, childhood street names, and school names and locations.
- Never share your passwords, account numbers, or other sensitive information in emails or over the phone. A bank or other institution contacting you will not request this information. When in doubt, hang up or close the email and call the institution directly.
- Be careful with communications from people you don’t know. If you aren’t sure about the person contacting you, it’s better to wait than act immediately. Try reaching out yourself through different – and more trustworthy – channels. If something seems suspicious, it’s best to be safe and not respond.
- Use multi-factor verification for all accounts. This should include your email and any other account that offers this option. Never share your passwords to these accounts with anyone, and do not write them down in a place where they can be found, even physically.
- Use strong passwords every time and vary them. Don’t use the same password across multiple sites or ones that are easy to guess.
- Set your WiFi network to private and password protect it. Don’t let strangers or neighbors onto your network. If your internet provider has monitoring, stay vigilant, and block any users you don’t know who may have gained access.
Social engineering has become mainstream: What does it mean for your organization?
Social engineering has been around for centuries, and attackers continuously find new and creative ways to reach their targets. When one trick no longer works, they shift to stay ahead. And these attacks are on the rise. Employees need to know how to avoid falling for the manipulative techniques of social engineers. Education in social engineering techniques and awareness help people be on the lookout to stop these attacks.
While the above information is a good starting point to protect yourself and identify these attacks, it may not always be enough. SoSafe’s gamified Micro-Learning and Smart Attack Simulation can lower threat response time by transforming employees into active defenders of your organization. Look at our product and be another step closer to managing your human risk.
