See how NIS2 raises the bar for training and awareness and how your organisation can stay compliant with country-level updates and a practical 90-day plan to get ready.

Compliance
8 steps to build a NIS2-aligned security awareness programme
Nearly 90% of organisations expect more cyberattacks in the year ahead, but NIS Investments 2024 shows many are still unprepared for NIS2. New sectors lag in collaboration and preparedness, while even experienced ones admit they lack the staff to meet new obligations.
The NIS2 Directive stands as a landmark in European legislation, setting new standards for strengthening cybersecurity across the EU’s critical sectors. With the implementation deadline now behind us, the focus is shifting firmly from passing laws to putting them into practice.
To support this transition, the European Union Agency for Cybersecurity (ENISA) published its Technical Implementation Guidance. It translates the directive’s dense requirements into actionable advice that organisations can embed into daily operations.
The guidance is formally aimed at digital infrastructure and ICT service management entities. Yet its value extends well beyond that circle. For each of the thirteen cybersecurity requirements it covers — including areas like incident handling and supply chain security — ENISA covers three things:
- actionable guidance,
- examples of evidence to prove a measure is in place, and
- practical tips for implementation.
This format makes it a working tool for organisations to raise its security standards, demonstrate compliance, and strengthen resilience.
The guidance maps NIS2 requirements to well-established frameworks such as ISO/IEC 27001 and the NIST Cybersecurity Framework. This alignment means that organisations already working with these best practices are not starting from scratch. The guidance simply helps connect the dots, streamlining the compliance process and preparing for audits.
The audit of daily routines
ENISA’s focus on outcomes rather than paperwork becomes especially clear in Chapter 8. Here, ENISA zeroes in on a foundational area of security: cyber hygiene and staff training. By treating awareness as a measurable control, complete with evidence and impact tests, the guidance underlines a wider regulatory shift: Security culture is now as critical as technical defences.
The term “cyber hygiene” borrows from the familiar concept of personal hygiene, small, consistent routines that stop minor problems from becoming major ones. Translated into cybersecurity, it means embedding regular, measurable practices that reduce the likelihood of human error leading to serious incidents.
Under the NIS2 directive, training and awareness programmes need to be carefully designed, delivered in the right way, and most importantly, shown to work. For a long time, success was measured by surface-level numbers: how many hours of training were held, or how many employees showed up. Now the focus has shifted. Regulators want proof that behaviour is changing and that people actually know what to do when an incident happens.
That means looking at new kinds of measures. Audits can ask: how many staff reported a suspicious email? How fast did they raise the alarm? Are phishing simulation results improving over time? Records of who completed training or acknowledged a policy still matter, but they now sit in the background as supporting evidence rather than the main proof point.
The shift might sound demanding, but it’s also reassuring. It reflects something security teams have known for years: awareness only counts if it sticks. Training should leave people not just informed, but give people the confidence to spot threats and act quickly when it matters most.In this article, we show you how to align with NIS2 while building a security culture that lasts.
8 practical steps to put ENISA’s advice into practice
ENISA’s guidance on the NIS2 directive covers a wide range of requirements, but much of it comes down to one question: how do you turn NIS2 requirements into daily practice? To make that easier, we’ve organised their advice into eight steps. This structure brings all the recommendations together in a way that’s easier to follow and apply, without losing the detail regulators expect. The result is a practical roadmap for building a cybersecurity awareness programme that works not just on paper, but in daily operations.
Step 1: Start with a clear and structured awareness plan
Begin by setting out a structured plan that defines your objectives, the topics you’ll cover, and a clear schedule for delivery. Use a mix of formats to keep people engaged, from online modules and interactive workshops to webinars, newsletters, and internal campaigns. Make sure the programme ties directly into your organisation’s wider security policies, so it feels part of the bigger picture rather than a standalone exercise.Above all, document everything. Programme outlines, schedules, training materials, and communications should all be recorded. This evidence is what regulators and auditors will expect to see, and it demonstrates that your approach is not just well-intentioned, but well-governed.
Step 2: Don’t just train IT, train everyone
The NIS2 directive makes it clear: training and awareness activities must include everyone, from employees and management bodies to contractors and service providers where relevant.
These activities need to be repeated regularly, both to onboard new joiners and to refresh the knowledge of existing staff. Leadership involvement is especially important. When management participates in the same training as their teams, it signals commitment and sets the tone from the top. Under NIS2 compliance, management bodies carry personal accountability and can be held liable for infringements.Yet many organisations still fall short. A recent study found that only 51% of leadership receives dedicated cybersecurity training, with some newly regulated sectors reporting non-participation rates of over 70%. That gap is exactly what a modern, organisation-wide programme must close.
Step 3: Cover essential cyber hygiene practices
To be effective, security training must focus on everyday actions people can put into practice straight away. That means covering a broad set of hygiene basics that apply across roles and contexts, such as:
- Clear desk and clear screen policies.
- Using multi-factor authentication, strong passwords, and password managers.
- How and when to report security incidents.
- Safe email and web browsing practices.
- Recognising and avoiding phishing and other social engineering attacks.
- Secure use of mobile devices and working from home.
- Applying software updates, secure configurations, and network segmentation.
- Fundamentals of backups, recovery, and business continuity.
- Core principles of Zero Trust.
- Secure use of connected vehicles, where relevant.

By making these areas part of regular security training, organisations turn broad security goals into tangible habits that support both compliance and resilience.
Step 4: Reduce risks from mistakes and targeted cyber attacks
People play a central role in security, which is why attackers often focus their efforts on them. A report found that 68% of breaches involved a non-malicious human element, while in EMEA, social engineering remains one of the most common incident patterns.
Awareness programmes need to cover the types of mistakes and manipulations that cause the most harm. That means teaching staff how to spot phishing attempts, pretexting, and even physical tactics such as tailgating.Employees also need guidance on avoiding accidental data exposure, for example, sending information to the wrong person or misplacing a device. Training should cover everyday risks too, like using public Wi-Fi or downloading unverified software and more.
Step 5: Provide resources, and contact points
Staff are far more likely to apply what they learn if they know where to turn for help. Offer clear instructions and name specific contacts for cybersecurity questions so support feels personal and accessible.
Back this up with practical resources — such as ENISA’s Awareness Raising in a Box — and consider external initiatives like the Cybersecurity Skills Academy to expand learning opportunities. Framed this way, security becomes a support system people can trust, not just a list of rules to follow.
Step 6: Provide role-specific and incident-specific security training
Not every role carries the same level of risk. Some employees — such as IT administrators, developers, or staff in sensitive areas like finance and HR — need deeper skills than general awareness training can provide. What won’t work is relying on a single, annual course for everyone.
Identify these roles and deliver targeted modules that fit their responsibilities, whether that’s secure system administration, application security, or handling sensitive data.
SoSafe’s Cybersecurity Awareness Training is designed to make complex risks easy to grasp. Instead of overwhelming staff with information, it delivers focused lessons in clear language, supported by relatable scenarios. This approach helps people retain knowledge and apply it under pressure — a key requirement when every minute counts in an incident.
Adding recognised certifications and aligning training with frameworks like ENISA’s European Cybersecurity Skills Framework (ECSF) can also help strengthen credibility and show regulators you take these NIS2 requirements seriously.
Customise training not just by role, but also by how staff may need to respond in a crisis. Employees should understand the threats most relevant to their work, the behaviours expected of them during an incident, and the basics of crisis communication and business continuity. Simulation scenarios and incident drills give people the chance to practise under realistic conditions.
Under NIS2’s multi-stage reporting process, organisations must issue an early warning within 24 hours of an incident, making readiness a compliance requirement as well as an operational necessity.
Tools like SoSafe’s Phishing Report Button make that readiness practical by giving employees a direct way to escalate suspicious emails. Reports go straight into triage, cutting response times and ensuring incidents are captured while they still matter.
Step 7: Test effectiveness and collect evidence
This is where awareness moves from good intentions to measurable impact. It’s not enough to deliver training, you need to know if it’s working. Quizzes, realistic scenarios, phishing simulations, and tabletop drills are all effective ways to see whether the lessons are sticking.
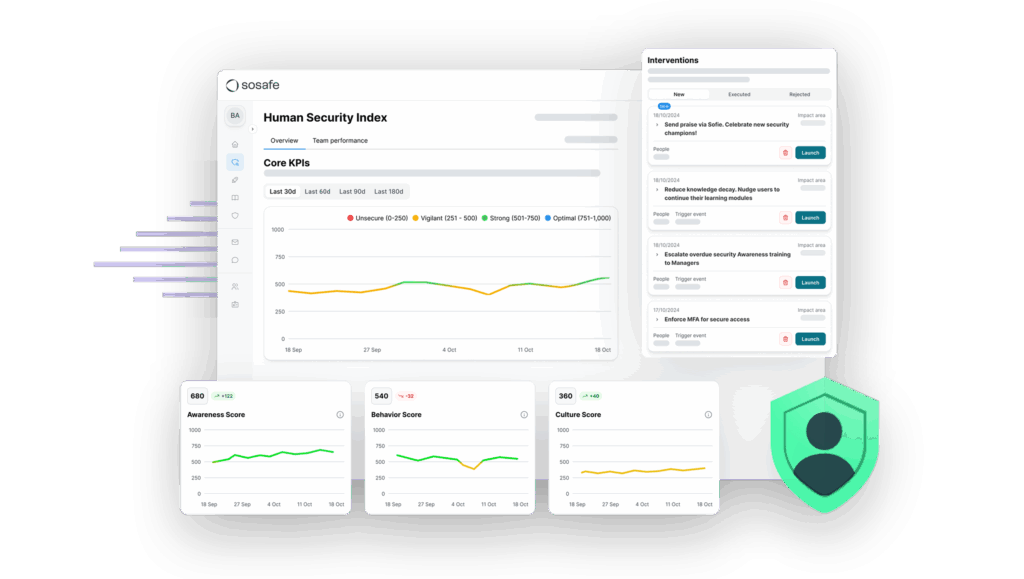
For NIS2 compliance, hard evidence is essential. Keep records such as attendance lists, certificates, test results, and feedback forms. Document annual updates to your training programme too, as this demonstrates continuous improvement. SoSafe’s Human Risk OS strengthens this process by bringing all evidence together in one place. Training results, phishing data, and policy attestations feed into a single dashboard, making it easier to demonstrate compliance and spot areas of weakness early. This turns evidence collection from an administrative task into a continuous improvement loop.
Step 8: Keep awareness training continuous and adaptive
Update cybersecurity training programmes at least once a year — more often if new risks or policies emerge — so content always reflects the current threat landscape. Build lessons learned from past incidents into future sessions to keep training relevant and practical.
Maintain clear records of updates, training logs, and certificates. This evidence shows regulators that your programme is a living part of your security strategy.
Turning NIS2 compliance pressure into resilience with SoSafe
Under the NIS2 directive, organisations need to show that people can recognise threats, report incidents quickly, and avoid common mistakes. For many, this is the hardest part of compliance. Survey suggests that around a third of IT leaders see basic cyber hygiene and cybersecurity training as the biggest challenge.
SoSafe is designed to make training practical. Training modules are short and role-specific, ensuring both staff and management cover what they need without losing time. Phishing simulations test real behaviour, while micro-lessons provide feedback that sticks.
The Human Risk OS dashboard brings these results together with clear evidence, so organisations can demonstrate progress to auditors. And with one-click reporting tied into automated triage, teams can meet the 24-hour incident reporting requirement without building new processes from scratch.
The benefits are concrete. Organisations using this model typically see fewer successful phishing attempts, faster reporting from staff, and easier preparation for audits. The same evidence also supports other frameworks like ISO 27001 or DORA, reducing duplicated effort.
NIS2 Guide:
Roadmap to meeting security training obligations























