Explore the intersection of information security and behavioural science - and the benefits of measuring behavioural change.

Behavioral Science
What real-world data reveals about the effectiveness of phishing simulations
Anna Müller knew better. She had completed her security training, recognised phishing tactics, and understood the consequences. Yet when an email arrived about her salary, with a new mortgage weighing on her mind, she clicked. Her story, shared by one of SoSafe’s customers, shows how easily real-world pressures can override even the best intentions.
“I remembered the training,” Anna later said. “But the subject was my salary, and with a new mortgage hanging over me, I clicked. At that moment, I just needed to be sure.” Anna’s decision reflects a wider reality: the very qualities that help people succeed at work — responsiveness, efficiency, curiosity — can also make them vulnerable.
The latest Verizon Data Breach Investigations Report examined more than 22,000 incidents and 12,000 confirmed breaches. Human error played a part in 60 percent of them. Nearly a quarter began with stolen credentials, and Business Email Compromise (BEC) alone caused 6.3 billion US dollars in losses.
And Anna is far from alone. Gartner research shows that 70 percent of employees admit to bypassing security controls, and three-quarters say they would do so if it helped them meet business goals.
The uncomfortable truth about traditional cybersecurity training
These statistics force us to confront an uncomfortable question: after decades of security awareness programmes and millions spent on phishing simulations, why does someone like Anna, trained and aware, still click?
The answer is not that phishing simulations fail. It is that most organisations have not been running the right kind.
Traditional awareness initiatives were built to satisfy auditors, not to understand how people think and act. They often treat security training like a vaccination, one annual dose and you are protected. But human behaviour does not work that way. Anna’s security training was twelve months old when that salary email appeared. In a moment of financial stress, with real money on the line, that single session might as well have been ancient history.
This gap, between knowing the correct response in a training room and making the right decision under pressure, is exactly where attackers strike. They do not wait for convenient training windows. They exploit stress, urgency and distraction when rational defences are weakest.
So, do phishing simulations work? The research says yes, but with an important caveat.
What studies reveal about phishing simulations
A 2024 meta-analysis of 42 studies reveals what truly changes the game: timing and context matter more than content.
When security training happens at the moment of risk, immediately after someone clicks a simulated phishing email, susceptibility drops by an average of 40 percent. Researchers at Carnegie Mellon University confirmed this: point-of-error training significantly outperforms every other delivery method, including follow-up emails, videos or gamification.
In another study, overall improvement was modest, but participants who fully completed interactive modules showed a 19 percent lower failure rate. This clear gap shows why keeping people engaged and delivering quality training matters.
Other research findings worth noting:
- Embedded training works: Zurich University found that built-in email training reduced phishing failures to 24.5%, down from 47.5% without it.
- Large-scale impact: A study with 31,000 participants found that after 12 weeks of phishing simulations, 66% of users resisted credential-based attacks.
- Better detection skills: After high-quality training, the share of users able to spot phishing emails jumped from 11% to 64%.
Why most security training still falls short
What does effective security training look like in practice? Think about Anna. If her company’s training had stopped at a single slide deck a year earlier, or relied on the same basic simulations every month, it is no surprise she clicked.
Many organisations run phishing simulations, but most rely on static templates and one-size-fits-all approaches. They often measure success only by click rates, missing the deeper behavioural patterns that predict real-world resilience. It is like teaching someone to recognise a single car model when what they really need is an understanding of traffic patterns.
Science tells us something different is needed. Research from behavioural psychology shows that lasting change depends on three elements that most security training programmes still lack:
1. Contextual relevance
Generic “Nigerian prince” simulations rarely prepare people for the attacks they will actually face. Modern attackers research their targets carefully. They send HR managers emails about policy changes, finance teams messages about invoice disputes, and legal departments notices about compliance updates. To build real resilience, phishing simulations need to mirror this sophistication.
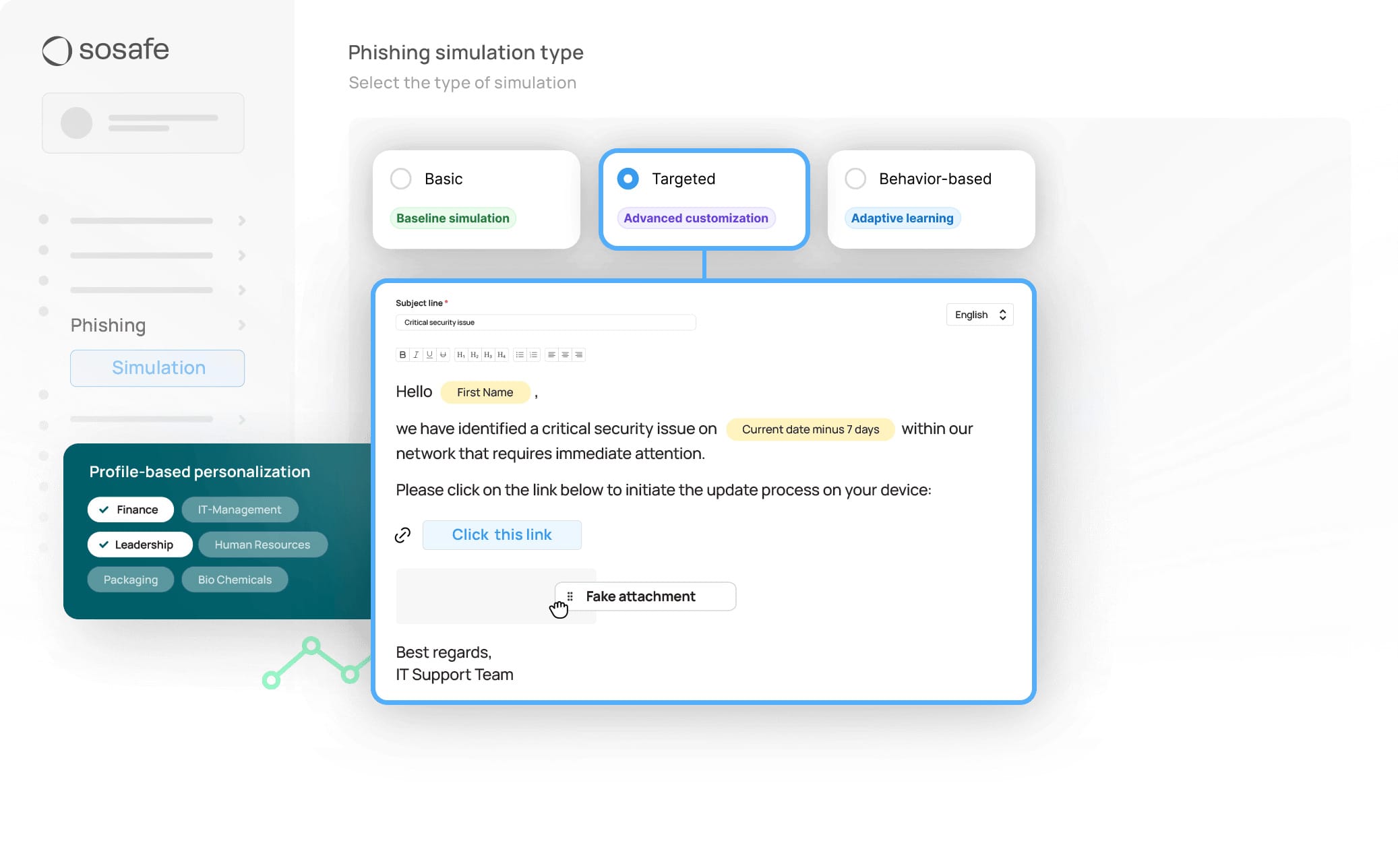
2. Adaptive difficulty
Sending the same level of challenge to everyone wastes time and breeds complacency. A developer who has never clicked a phishing link needs different scenarios than someone in sales who falls for one every month. Without personalised progression, experienced users get bored, while those who struggle become discouraged. Both groups eventually disengage.
3. Psychological insight
Traditional programmes often teach what to look for, such as a suspicious link, but overlook why people click in the first place. When Anna opened that salary email, she was not being careless. She was responding to a carefully crafted mix of authority, urgency and personal relevance that bypassed her rational defences.
How behavioural science transforms security training
Behavioural science turns security training from a compliance checkbox into actual risk reduction. Instead of simply showing employees phishing examples, it helps them recognise their own psychological vulnerabilities and build practical defences against them.
Imagine if Anna’s training had worked differently. Over the year, she would receive simulations tailored to her HR role. These would not be generic templates but scenarios that evolve in response to real attacks seen against HR teams worldwide.
The difficulty would adapt to her progress. As she became better at spotting fake salary notifications, the system would introduce more advanced social engineering tactics that closely reflect real business email compromise campaigns.
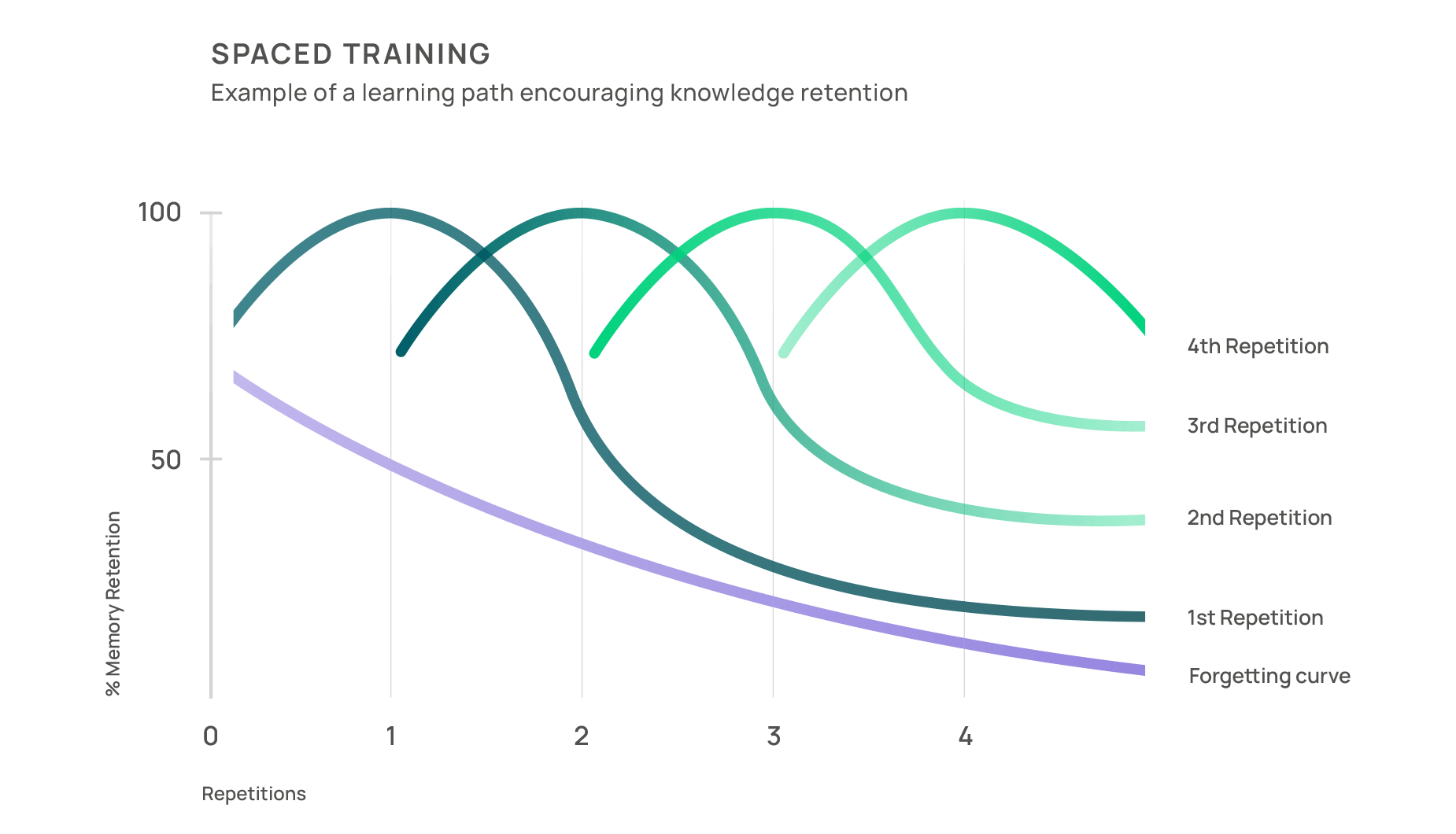
Most importantly, when she clicks, she does not just see a message saying she has failed. Instead, she receives immediate, private coaching that explains the psychological trigger behind her decision.
This message exploited loss aversion, the fear of losing something you already have. Notice how it implied your salary might be reduced if you did not confirm? Here is how to recognise this tactic.”
This kind of timely, empathetic feedback helps employees understand why they reacted the way they did and equips them to make stronger choices in the future.
The feedback is delivered in her native German. This matters because security lessons are absorbed more effectively when taught in someone’s primary language. It is a detail that many global programmes still overlook.
This behavioural approach is what sets modern security culture programmes apart from traditional awareness training. Most platforms provide phishing templates and basic reporting. Advanced solutions, such as SoSafe, go further by applying principles from cognitive psychology, learning science and behavioural economics. They recognise that every employee has unique risk patterns shaped by their role, experience and psychological profile.
Global manufacturer WAGO introduced SoSafe’s behavioural phishing simulations and personalised micro-learning across more than 30 countries and 21 languages. Within a year, phishing click rates dropped sharply, reporting rates rose, and employees’ Behaviour Score (metric that quantifies phishing resilience) climbed from 65 to 91.
“It is unrealistic to expect users to know what is behind a link,” said David Kreft, CISO at WAGO. With simulations and feedback, people gain the confidence to pause and make the right call. Staff at WAGO even began discussing phishing with their families, proving that effective awareness training strengthens security culture both inside and outside the organisation.
The most significant impact of effective simulations goes beyond reducing clicks. Quality programmes turn employees into active defenders within their organisations.
Analysis of SoSafe’s behavioural security programmes shows:
- Two thirds of users become active threat reporters.
- After 12 months, organisations see 80 percent drop in risky actions.
- Within six months of rollout, overall phishing risk drops to one fifth of its original level.
The true value of phishing simulations is a cultural shift where employees move from passive learners to active defenders who help protect the organisation every day.
Why leaders hesitate
1. Changing perceptions
Despite proven results, some leaders remain hesitant. A common worry is that phishing simulations could make employees feel uncomfortable. In practice, the opposite happens when programmes are framed positively. Employees who click are not punished; they are supported with constructive feedback.
At organisations using SoSafe, staff who once feared “gotcha” tests now see simulations as safe opportunities to sharpen their skills and grow more confident in recognising threats.
2. Time as a concern
With full calendars, CISOs often question whether regular simulations and micro-learning will add extra burden. In practice, simulations take only seconds to complete, and short learning units fit easily into a coffee break.
The return on that small investment can be significant. Global services company, Fellowmind, saw phishing interactions fall by 74 percent and training completion rise to 97 percent after deploying SoSafe’s integrated platform. Employees described the experience as engaging rather than disruptive.
3. Keeping pace with evolving attacks
Another common concern is whether simulations can keep up with attackers’ constant innovation. The answer is yes, but only if the programme is adaptive. Off-the-shelf templates quickly lose effectiveness once employees begin to recognise them.
That is why SoSafe continuously refreshes scenarios and adjusts difficulty to each employee’s progress. At Scheuch, an industrial technology company, a phishing campaign that once took 20 hours to design and manage now takes just 30 minutes using SoSafe’s template library.
I don’t want to create each and every phish from scratch. The SoSafe database lets us customise templates for teams or functions with very little time commitment. Instead of 20 hours designing a singular simulation, it now takes 30 minutes. And with behavioural data, we have the ability to control the level and frequency of training directed at each person in that team, based on their past responses and risk-level.”
— Gordon Shepherd, Team Leader Service & Infrastructure at Scheuch
The bigger picture: From awareness to active defence
Phishing simulations are not a silver bullet. Technical controls such as firewalls and endpoint protection remain essential. Yet when a malicious message slips past those defences, the person behind the keyboard becomes the final safeguard. Building a strong security culture means preparing people to act decisively in those critical moments.
The journey of WAGO, along with the experiences of organisations such as Fellowmind and Scheuch, shows what works. By embedding behavioural phishing simulations and personalised micro-learning into daily workflows, these companies have moved beyond tick-box training and built lasting resilience.
The results speak for themselves: fewer clicks, lower risk and a workforce that is genuinely more prepared to stop real attacks. To learn more about how behavioural data can shape stronger security cultures, read our report on Behavioural Metrics: The Future of Security Awareness.
Behavioural Security























