
Vishing
What is vishing?
Vishing or “voice phishing” is a type of social engineering attack in which criminals attempt to trick users into divulging sensitive information via a telephone call. In these attacks, hackers try to manipulate their victims by spying on their environment, faking identities, or collecting internal information in order to appear as credible as possible.
After gaining enough information, the fraudsters usually use and manipulate voice-over-IP services, or VoIP for short, which allows them to make many calls at once, cover their tracks, and change the phone number displayed.
The target of the attacks ranges from sensitive data to passwords and credit card information. Nowadays, they also try to obtain personal data such as gender, first name, and age to create profiles of their victims and use them for fraudulent activities.
The concerning news is that these attacks are on the rise: A study conducted by Agari and PhishLabs found a fivefold increase in attempted vishing attacks from the beginning of 2021 to Q1 of 2022. However, vishing is not the only method attackers use to try to trick their victims. Other popular types of attacks are phishing and smishing.
Phishing, vishing, and smishing: What are the differences?
Phishing, vishing, and smishing differ primarily in the way cybercriminals contact their victims. While phishing refers to fraud via email, vishing attacks are carried out by telephone and smishing attacks via text messages. However, the medium is not the only difference between these attacks: Fraudsters are continually innovating their schemes and trying to reach the maximum potential of each technology. In some cases, it’s also possible for them to use a combination of phishing, vishing, and smishing to appear even more trustworthy to the victim.
In order to protect ourselves from such attacks, it is important to understand how they are currently being used:

Phishing: Conventional phishing via email
Phishing scams reach their victims both in their private and professional inboxes on a regular basis. The purpose of these fraudulent emails can differ greatly from one another, as there are many different scenarios in which hackers choose this type of scam, but the most common goals are luring recipients into clicking on a link, opening an attachment, or providing sensitive data such as credit card numbers or login credentials. Phishing emails are very popular with cybercriminals because they are easy to obtain, costless, and very effective – in fact, more than three billion phishing emails are sent every day.
In addition to conventional phishing attacks, in which the target person falls into the attacker’s pattern by chance, there are also spear phishing attempts. In this case, the victim is specifically targeted in order to find out about their habits and preferences. Based on carefully collected data, customized and personal emails are sent with the objective of gaining unauthorized access to confidential data.

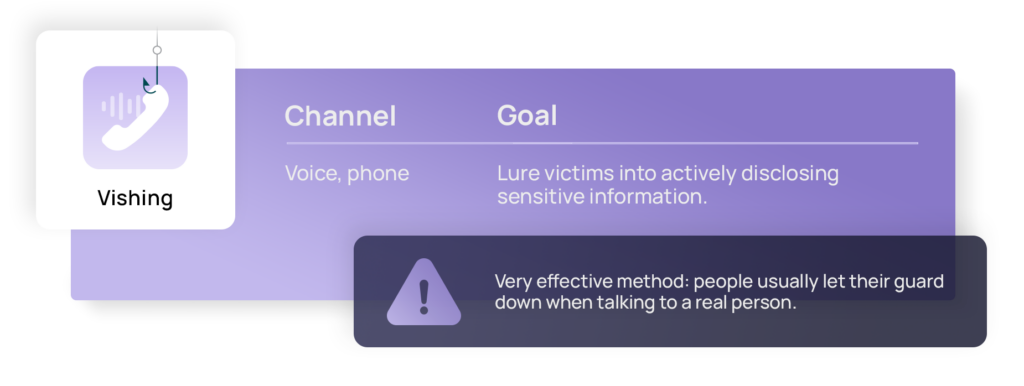
Vishing: Voice phishing over the phone
In contrast to phishing, the victim of vishing attacks needs to actively disclose information instead of just clicking a fraudulent link. The attackers must also attack manually and call the victims individually. Since there is less technology involved, there is not much hacking knowledge needed from the scammers’ side. Additionally, voice phishing can be more effective than other methods because people tend to let their guard down when they’re talking to someone instead of only receiving a message.
Here, too, there’s a special form of vishing called spear vishing, in which individual victims are specifically targeted so that the most credible information possible can be obtained. For example, in this case, the attacker might call already knowing a target’s name, address, and other personal information, making it much easier to believe they are someone who should have access to an account number or other sensitive data.
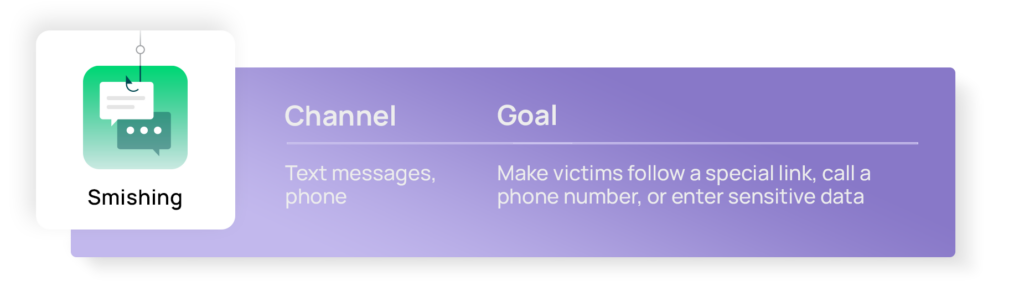
Smishing: Data theft via fraudulent text messages
Smishing attacks rely on text messages asking their victims to follow a special link, call a phone number, or enter sensitive data. The strategy behind the scam comes in many different shapes and forms behind which a criminal is hiding, pretending to be somebody else. Since people are more aware of fraudulent emails, this type of scam is often more successful.
One of the cybercriminals’ favorite smishing scams is to inform their unsuspecting victims about an alleged package shipment in order to lure them into a malicious website. But this is not the only one: Mobile users should also be alert and skeptical of unexpected or unrequested holiday-based awards, prices, and offers, among other scams.
Social Engineering: the manipulation behind the scam
Whether phishing, smishing, or vishing – all these attacks are primarily about human manipulation, also known as social engineering.

To induce certain behaviours in people, fraudsters try to manipulate their victims by taking advantage of their emotions – one of these being trust. In order to gain the greatest possible control over the scam, they spy on their victims to gather private information that makes them appear more credible and trustworthy.
That’s why cybercriminals often fake identities and pose as journalists, bank consultants, or officials to exploit their interlocutor’s insecurity. Additionally, they often put their victims under time pressure so that the situation cannot be adequately reflected upon, and action is taken out of fear.
With AI on the rise, there are now several technologies to make scams seem even more real. One of them is voice cloning, the next level of vishing attacks. Voice cloning lets cybercriminals simulate the voices of co-workers, authorities, and other people of influence, including their CEO. Cybercriminals were able to steal 35 million USD from a bank in Hong Kong in this way in 2021.
What are common targets of vishing attacks?
Vishing victims can be employees or executives of a company as well as private individuals. In fact, elderly people often become the target of vishing, as the scammers rely on the gullibility and low technology affinity of their conversation partners.
The best-known example of vishing is the so-called “grandparent scam“, in which scammers call elderly seniors to pretend to be their grandchild in a crisis, asking for immediate financial assistance. They then send an “acquaintance” over to collect the money loaned.
When attacking businesses, perpetrators are usually extremely well prepared. For example, they research the names and direct dial numbers of specific individuals and contact them with what at first glance appears to be a genuine request. For example, in the summer of 2020, Twitter became the target of a coordinated vishing attack where attackers made vishing calls to Twitter’s tech support and consumer services employees. The attackers’ instructions were simple: “We need you to reset your password”. A few employees were duped and followed the instructions, and, as a result, attackers gained valuable credentials such as usernames, passwords, and multi-factor authentication codes.
Most common vishing examples
With voice phishing, attackers are becoming increasingly creative and are coming up with new ways to deceive their victims. These are some of the most common vishing attacks to watch out for:

Bank impersonation
In the first six months of 2020, UK banks alone reported over 15,000 cases of bank scams, with total damage of over 58 million pounds. In this scam, the caller pretends to be an employee of the victim’s bank, frequently using a spoofed phone number and caller ID. Then, they claim that the victim’s account is at risk and that, because of this, they need a secure payment or the account details in order to transfer the funds to another seemingly “safe account”.
In many cases, fraudsters use a combination of emailing and contacting their victim by phone. In case of an unexpected call from “your bank”, please be aware that financial institutions will never ask you to share sensitive information such as your login credentials.
Romance scam
Another common example of vishing is the romance scam. This tactic has recently become known through the Netflix series “Tinder Swindler”. In this case, the scammer uses fake profiles on dating websites to manipulate their victims.
In order to entice their victims to make payments or disclose sensitive data, the perpetrators build up a relationship with the victim over days and weeks. To gain the trust of their targets, the perpetrators usually make big promises or profess their supposed love.
Loan or investment offers
Sometimes, scammers will call their victims with loan and investment offers, quick fixes to pay off debts, or get-rich-quick schemes that sound too good to be true. Here, too, they push their interlocutor for urgent action so that this deal can be secured.
Medicare scam
Due to lower technology affinity, older adults are often the targets of vishing attacks. In the US, attackers frequently request Medicare numbers or bank account details – especially during Medicare enrolment season. Once the scammers get those sensitive data in their hands, they will either fraudulently redirect the victim’s Medicare benefits or steal their money.
Why is vishing so dangerous?
The reason why vishing is so dangerous is that it is a combination of technical manipulation and emotional influence. Voice-over-IP services and social networks make it easy for criminals to pretend to be someone else or to gain the trust of the person they are talking to. With little effort, the scammer’s phone number can be manipulated to disguise the true origin of the call, so the victim’s phone indicates a legitimate source.
Unfortunately, vishing is difficult for authorities to detect, especially when it occurs over VoIP. And because vishing attacks are often outsourced to other countries, the country’s own law enforcement agencies are powerless in many cases.
The consequences of vishing attacks are far-reaching and can also cause psychological damage. While compromises to your credit or debit card are easier to manage, fighting back control of your email account can be a slightly tougher task. A bitter pill to swallow since, with access to your email, hackers can begin to send password resets to themselves and seriously compromise your digital footprint.
How to spot vishing attacks
Vishing attacks can come in many shapes and forms. In most vishing calls, however, the perpetrators try to catch people off guard or build up subliminal pressure to obtain sensitive data. We have already seen how these psychological games are designed to manipulate the recipient of the call into disclosing personal or sensitive data. That’s why victims are often told that suspicious activity has taken place in one of their accounts or that they are entitled to a tax payment or a special offer. They are then asked to call a specific phone number to provide information, deposit a security payment, or verify their identity.
Learning how to spot a vishing scam becomes therefore vital. The good news is that there are a few tips you can remember whenever you are approached by an unknown caller:
- If the caller claims to be a representative of authority or administration: Keep in mind that no federal agency or trustworthy company will ever contact you to ask for private data unless you requested it.
- If the caller is pushy: No reputable caller will ever pressure you into revealing sensitive information. Scammers will try to tap into your sense of fear, using threats of arrest warrants and other consequences. Be aware that every process takes time, even with authorities and agencies.
- If the caller asks for your information: Phone calls are not the safest way to synchronize sensitive data or get in touch with each other, and authorities know that too. Important matters are therefore rarely clarified over the phone.
We have also prepared an infographic with the most important things to consider, especially from the social engineering side. Better safe than sorry, so we encourage you to download it and share it with your team – and also loved ones.
How to protect against vishing?
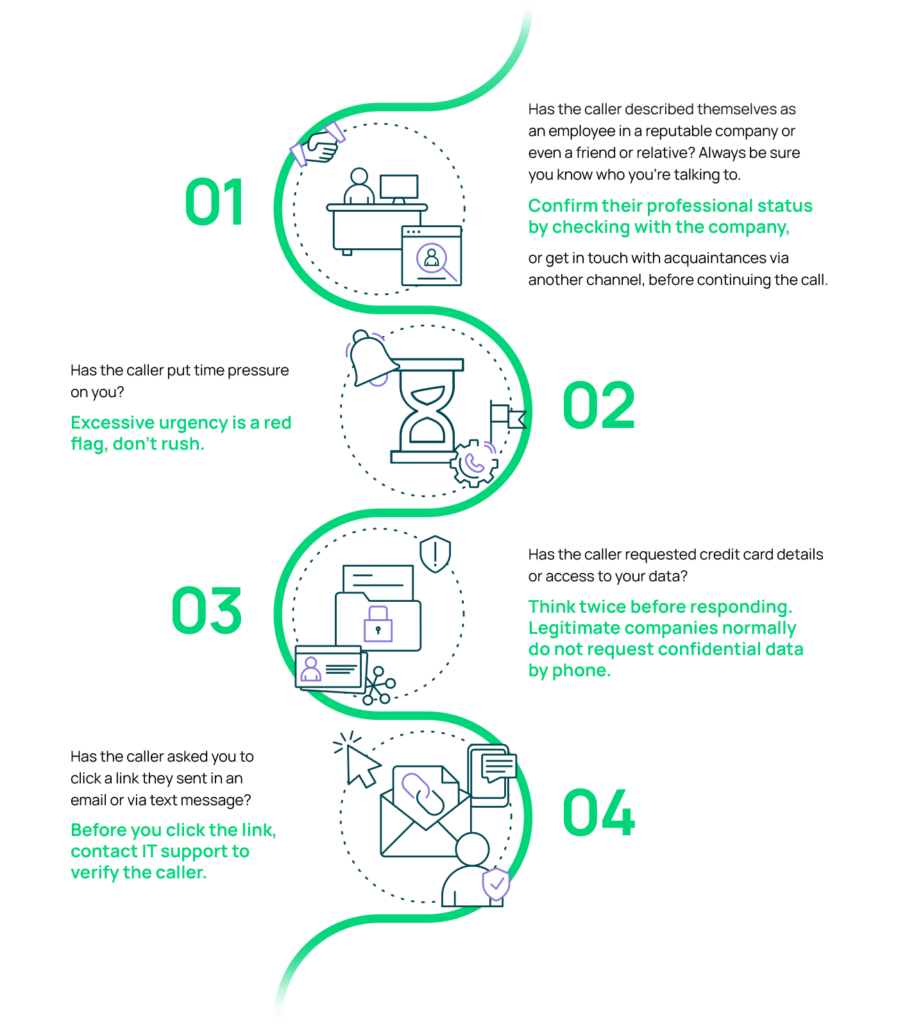
To be protected against vishing calls, they need to be recognised as such. If you critically question suspicious calls, you have taken a first and important step. These guidelines will help you to further reduce the risk of a vishing attack:
- Be skeptical and have a healthy distrust of unexpected phone calls. No authority will contact you unannounced. So, if a stranger asks for sensitive data over the phone, alarm bells should ring immediately. If in doubt, research the website of the company in question and find out whether a request has been made.
- Don’t pick up the phone. Answering every phone call can be tempting but since caller IDs can be faked, simply let them go to voicemail. Listen to your messages and decide whether to call the person back. If it is really an urgent issue, the caller will contact you via another, safer way.
- Hang up if you distrust the caller. The moment you suspect it’s a vishing phone call, don’t feel obliged to carry on a polite conversation. Any information, even the simple sound of your voice, can be used against you by scammers. Simply hang up and block the number.
Vishing on the rise: How can companies protect themselves?
The number of cyberattacks is increasing day by day, and due to new AI-enhanced technologies, they are causing even more and more damage. One-third of security executives surveyed in the Human Risk Review 2022 said their company or network had been affected by a cyberattack. And although more than 90 percent say that awareness is important, not all of them are prepared for such cyber threats.
Therefore, it becomes essential for companies to increase their overall security awareness. Employees need to be aware of the psychological vulnerabilities an attacker would target and avoid engaging in such conversations. Education and awareness are the best ways to achieve this and to protect companies and their people against social engineering-related cybersecurity attacks like vishing.
While the tips listed above can help recognise vishing, they unfortunately are not enough to offer 100% protection. SoSafe cyber security e-learning modules can be tailored to fit the requirements of your company while making your team more aware of potentially dangerous voice phishing scams and training them to better respond to them. Take a look at SoSafe’s product to learn how to strengthen your digital self-defence.


















