Discover how our phishing simulations turn your employees into active defenders of your organisation.

Cyberthreats, Human Risk Management
Story of a ransomware attack
No time to read? Listen instead:
It sounds straight out of a movie: the humble protagonist, a straightforward plot, a villain demanding money in exchange for something you hold valuable.
But this is what a ransomware attack looks like.
Where the movie may have a happy ending, the story of a ransomware attack is no fairytale.
What is a ransomware attack?
Ransomware is a form of malware that sneaks into systems and prevents access to data. Spreading through the network and encrypting every piece of data across servers, the attack renders everything inaccessible.
Typically, the ransom note is installed on the system at the same time the data is encrypted. It lists out demands such as the amount, transaction information, and any other details hackers deem necessary. To coerce victims to pay faster, attackers use a plethora of pressure tactics such as threatening to leak data or adding a countdown timer to the ransom note that increases amount if time runs out.
Cybercriminals carefully orchestrate ransomware attacks under hooded identities. They make informed, calculated assessments and employ varied attack patterns, being knowledgeable of the target’s security operations centre (SOC) response capabilities. After due diligence on mapping out company’s financial prowess, the more well-performing companies form the better bait.
This low-risk and high-reward nature of ransomware is the primary reason why attacks have doubled in 2021.
66% of businesses targeted by ransomware in the last year
90% of attacks impacted business operations
Source: Security Magazine
Types of ransomware
There are two main categories ransomware falls into, automated and human-operated, with their variety and veracity having quickly broadened.
Automated ransomware attacks follow a familiar pattern of user clicking on a link or attachment and triggering the ransomware. Attacks like WannaCry and NotPetya are a few examples. More recently, the ALPHV/Black Cat group carried out an attack on June 14, 2022, on a luxury spa in the United States where personal information of more than 4,000 individuals was published on a website in a searchable format! This form of victim shaming is the latest pressure tactic used by these hackers.
The other mounting threat is human-operated ransomware, more complex yet considered to be the most impactful. With deeper knowledge of system administration and network security configurations, adversaries launch these sophisticated attacks using spear phishing. They can also directly attack systems via known vulnerabilities to install the ransomware. Some popular examples are from gangs such as REvil, Samas and Bitpayer.
When talking about the types of ransomwares, some of the common ones include:
- Locker: Locking you out of your system, this renders all files and data inaccessible until the ransom is paid.
- Crypto: More widespread than Locker, this encrypts all files on the system and demands ransom in exchange for the decryption key.
- Scareware: Fake software that seems to have ‘detected a virus’ that can be resolved if the target pays ransom.
- Leakware or multiple extortion: Threatening to distribute confidential, encrypted data or sell it on the dark web, ransom is demanded to relinquish data control.
It is important to note, that attackers can also use a combination of all the above methods, making the attack so much more dangerous and demanding.
When it comes to the actual ransom, prices vary from attack to attack. It is important to note that paying the ransom does not guarantee a faster recovery or data restoration despite the claims from attackers. But it is not just money they are after. Access to sensitive data, exploiting vulnerabilities, and espionage are some other reasons that motivate attackers. Nevertheless, money is by far the greatest motivation.
76% of victims paid ransom to recover data
one third of those who paid did not get back data
Source: ENISA Threat Landscape 2021
Ransomware’s darker side comes with a double strategy to target victims. Data tells us that repeat offenders usually attack within 12 months, emphasizing the criticality of having a robust security defence in place.
80% of organisations that paid ransom fell victim to a second attack
Source: Cybereason 2022 Ransomware Report
Becoming a business model
Today, sophisticated attacks are known to be executed by a team of tech experts conducting ransomware-as-a-service (RaaS). These groups go on to deploy high-profile attacks for higher return on investment.
Nothing short of a legitimate business, RaaS models are replete with their own human resources, customer service, and even a sprawling network of partners with an array of options such as decryption negotiation and cryptocurrency transactions. Affiliates behind the attack are even known to maintain a social media presence and lend support via chatbots to accelerate the ransom process.

How is ransomware delivered and what is at stake?
There are diverse entry points for ransomware to creep in. It can be unintentionally downloaded, come as a payload, or be part of malvertisements. However, the most popular and effective method is via spear phishing emails. Designed to impersonate an organisation, a manager, a colleague, or anyone else, these emails can use typo-squatted domains with highly personalized content conveying a sense of urgency and the secret sauce: a malicious link. Once clicked, the malware finds an open door to make an entrance. This form of social engineering attack delivers targeted communication that is almost impossible to spot.
There are both long-term and short-term damages involved with every ransomware attack. The inability to access critical business information is the immediate effect. Response plan failure, hampered productivity and evident costs are other apparent consequences. Apart from significant and unexpected downtime, business continuity is also severely impacted. Long-term repercussions include loss of customer trust, impact on business viability, diminished revenue, and reputational damage, all of which are difficult to recover from.
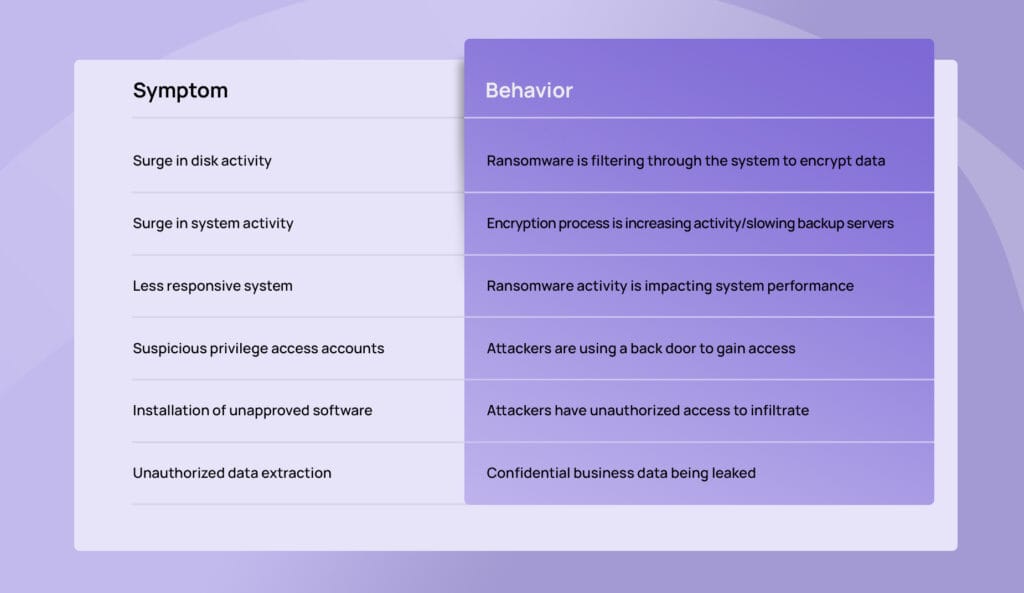
How to spot a ransomware attack?
The slow and silent nature of ransomware means that more organisations are on the receiving end of a crippling attack before security defences begin to roll out. However, there are several early indicators that we can use to catch them early:
Make phishing attacks miss the mark
Can I avoid ransomware attacks?
The golden question of the security world is also the most grueling one. Are we prepared? 61% of CISOs seem to think so. But their judgement may be misguided. The year-over-year increase in attacks shows why. To avoid contributing to their rampant rise, there are several actions companies can proactively take.
- Provide cyber security e-learning to employees that trains them to discern the authentic from the malicious with emails and threats.
- Ensure regular backups that employ different solutions and storage locations such as offline sites and cloud options.
- Run software and operating system updates as well as patches to keep machines secure from potential threats.
- Segment your network into subnets with their own security controls and implement identity and access management (IAM) with zero trust architecture that regulates system rights.
- Manage settings for ports that ransomware attacks target such as remote desktop protocol (rdp) port that enables remote access.
- Scan all emails that are sent and received to analyse potential threats in content, links, attachments.
- Initiate regular security audits of your company to rectify any loopholes such as unauthorized data access or misconfigured databases.
- Develop a recovery plan tailored to your organisation with defined roles to minimize the impact of an attack and get systems up and running again.
How should you handle a ransomware attack?

If you do find yourself under attack, speed is of the essence. Here are a few steps to immediately put into action:
- Disconnect infected devices
Immediately isolate infected devices from all network connections. Unplug the ethernet cable, disable WIFI connection, ethernet connection etc. - Notify your IT security team
Your IT security team should be immediately alerted so they can deploy the necessary protocol. - Reset credentials
Change all login credentials, especially for admins and other privilege access accounts. This will prevent hackers from laterally moving around the network. - Notify authorities
Report the incident so authorities can carry out an official investigation. Under the GDPR, organisations in the EU are obligated to report incidents involving personal data within 72 hours. - Install updates
All systems should have the latest updates installed to prevent hackers from exploiting known and patched vulnerabilities. - Verify backup before restoring
Make sure your backup has not been infected and the device you are restoring to is also malware-free before proceeding.
Stay ahead to stay protected
The multi-faceted nature of ransomware attacks requires a multi-dimensional approach in averting them. Cyber security training forms a cardinal rule for organisations with emphasis on continuous learning to keep key insights top of mind and encourage security habits to become second nature.
It’s time to giddy up so you don’t have to pony up.
Schedule our demo to explore how you can strengthen your first line of defence, your employees, and protect your organisation from cyber attacks.





















