Discover the top 8 cybercrime trends for 2024, expert insights on the current threat landscape, and best security practices.

Cyberthreats
What are the biggest cyberthreats facing the healthcare sector?
A hospital hit by ransomware was forced to stop non-emergency surgeries, hundreds of ambulances were rerouted to other hospitals, and chaos reigned in waiting rooms. It may sound like fiction, but it is the reality of many healthcare organisations that have been hit by cyberthreats recently. According to ENISA’s Threat Landscape Report, the health sector accounted for 53% of total incidents in Europe, with hospitals bearing the brunt at 42% from January 2021 to March 2023.
The economic impact of cyberattacks on the healthcare sector has also skyrocketed and is already running into the millions. In fact, 2023 marked the 13th year in a row where the healthcare sector was at the top of the most expensive data breaches, at an average cost of $10.93 million.
And attacks don’t seem to be slowing down in 2024. In February, a data breach of French health insurance companies compromised the sensitive birth date, social security, and marital status information of nearly half the country’s population.
While governments and regulatory bodies are taking measures to counter the threats, resources are normally scarce, and hackers also keep innovating to find the newest, most effective cyberattack methods to exploit the sector’s vulnerabilities.
The digital pandemic: Top cyber security risks for healthcare organisations
Cybercriminals target the healthcare industry in many different ways. From asking for million-dollar ransoms to the more traditional approaches of exploiting vulnerabilities in outdated systems, these are the top common threats that the healthcare industry needs to watch out for:
Ransomware: A steep price tag on sensitive data
Ransomware emerges as the predominant threat to healthcare organisations, comprising a staggering 54% of cyber security incidents, as highlighted in the ENISA report. Most worryingly, almost half of these attacks resulted in data breaches or leaks, such as the attack on the Parisian maternity hospital Pierre Rouquès – Les Bluets, when the hacker group Vice Society leaked 150 GB of patients’ medical and personal data on the dark web after the hospital refused to pay the ransom.
The truth is that a single ransomware attack can cause serious disruptions in hospital operations. This happened when, in March of 2023, Spain’s Hospital Clinic de Barcelona fell victim to a ransomware attack that forced them to cancel 150 non-urgent operations and up to 3,000 patient checkups across multiple facilities. As the hospital struggled to restore its data, it had to redirect patients to alternative healthcare facilities and record data manually. In another case from 2023, the German hospital network Katholische Hospitalvereinigung Ostwestfalen (KHO) faced service disruptions across three hospitals due to a Lockbit ransomware attack on Christmas Eve.
But as we know, cybercriminals are versatile and keep adapting to the circumstances. They have now realised that, in most cases, threatening healthcare organisations with releasing sensitive patient data is frightening enough for organisations without the need to encrypt their data, which is why they are now moving towards a new type of ransomware that doesn’t use data encryption, called encryption-less extortion.
The digital fight of hacktivism
The healthcare sector is considered a vital part of a nation’s infrastructure, and any attack on it can have a significant impact on its people. This is why hacktivists often focus on these institutions as a means of expressing their disapproval or opposition to a social or political cause.
One of their favorite tactics is Distributed Denial of Service (DDoS). These attacks flood targeted systems with bogus traffic, blocking access for legitimate users, paralyzing operations or slowing them down considerably. Two of the prominent group actors that have targeted the healthcare system with this method are Anonymous Sudan and Killnet. In a recent case, Anonymous Sudan hacked a Danish hospital to protest against an episode where the Quran was burned in Stockholm in front of the Turkish embassy.
Third-party vulnerabilities in supply chain attacks
Like almost any organisation, hospitals need the services of third-party suppliers or providers that have access to sensitive data or critical processes. Unfortunately, third-party suppliers are an open door for hackers to compromise patient information, disrupt medical services, and damage the hospital’s reputation and finances.
One of the most notable cases of a supply chain attack is the data breach of healthcare software provider Dedalus Biologie, which exposed the personal and medical data of nearly 500,000 patients from 28 different labouratories. As a result, the organisation had to pay an administrative fine of €1.5 million for violating the GDPR (General Data Protection Regulation).
IoT device vulnerabilities: Security flaws putting lives at stake
The rapid integration of Internet of Things (IoT) devices into the healthcare sector has revolutionized how care is delivered and has allowed better monitoring of patient health and more efficient management of medical resources. However, many IoT devices in healthcare settings are not equipped with sufficient security measures, making them susceptible to cyberattacks.
These vulnerabilities can provide cybercriminals with unauthorized access to sensitive healthcare networks. Once inside, attackers can access and manipulate patient data, disrupt service delivery, or even take control of critical medical equipment, which has dire consequences for patient safety. This is exactly what happened when a group of cybercriminals hacked into a Silicon Valley startup called Verkada and accessed the live feeds of 150,000 surveillance cameras inside hospitals, putting thousands of patients’ privacy at risk.
Advanced persistent threats (APTs): Cybercriminals playing the long game
An Advanced Persistent Threat (APT) is a highly sophisticated and targeted cyberattack that is meticulously planned and executed by individuals or groups with specific objectives, such as accessing valuable patient data. These attacks are designed to be long-term threats involving continuous, stealthy, and refined tactics, which allow attackers to infiltrate networks and maintain prolonged access while avoiding detection.
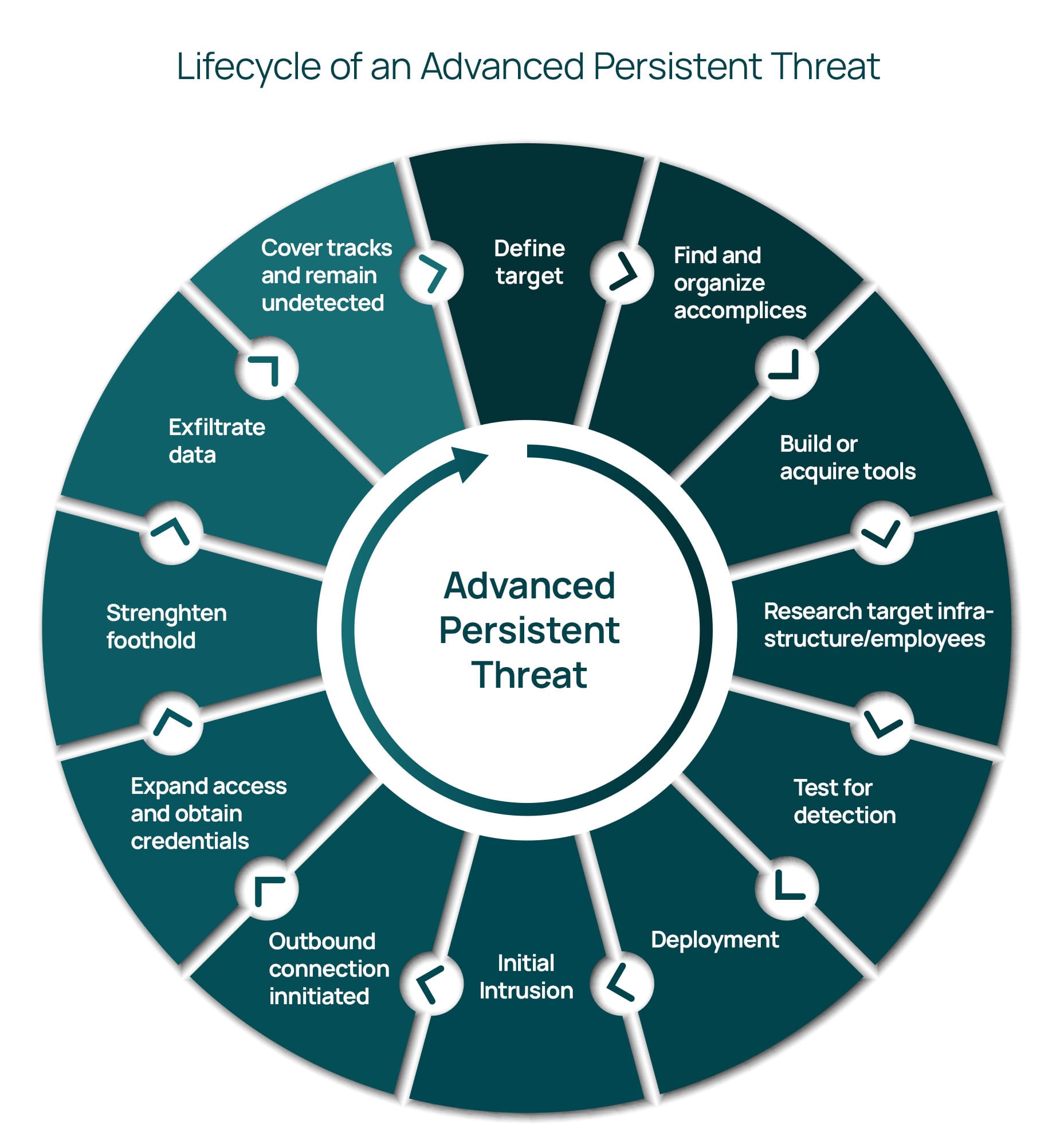
These attacks start with identifying a valuable target, followed by gathering a team and acquiring or developing tools necessary for the breach. Attackers conduct thorough research on the target’s infrastructure and key personnel, test their methods to ensure they can evade detection, and then deploy their tools to gain initial access. Once inside, they establish a foothold, often through phishing or exploiting vulnerabilities, and initiate an outbound connection to their command-and-control servers.
After gaining access, attackers move laterally within the network, stealing credentials and escalating their privileges to expand their control. They work to maintain persistent access by installing backdoors and other means to ensure they can return even if some elements are discovered and removed. The main objective is to exfiltrate valuable data stealthily. Throughout the attack, they take measures to cover their tracks, making detection difficult and allowing them to remain within the network for extended periods.
Insiders, errors, and poor security practices
Cyberthreats do not come only from professional cybercriminals. Insiders, such as employees or contractors, can unintentionally or maliciously compromise sensitive information. For example, an employee might fall for a phishing scam, exposing patient data, or a contractor might misuse their access privileges to steal confidential information. Simple misdelivery mistakes, where someone accidentally sends patient records to the wrong recipient, can also lead to unauthorized access and misuse of sensitive information, eventually becoming a security risk.
Poor security practices can also pose significant risks and leave healthcare systems exposed to cyberattacks. Weak password policies, insufficient data encryption, and failure to update software regularly create easy entry points for cybercriminals. Also, an outdated system lacking multi-factor authentication makes it easy for attackers to infiltrate and compromise patient privacy. Such breaches can result in severe legal and financial consequences for healthcare providers.
Other major threats to the healthcare sector
The healthcare sector faces many more cyberthreats today, such as the use of AI and other new technologies by cybercriminals. To understand the full scope of cyber risks currently affecting the healthcare sector, click the banner below to access our Cybercrime Trends Report 2024.
Cybercrime
Trends
2024

Why do cybercriminals target the healthcare sector?
Cybercriminals are always looking for opportunities to achieve their goals, but they only devote their efforts to attacks and victims that are lucrative enough. One of the most powerful reasons they target healthcare organisations is the vast amount of sensitive information they hold – but it’s not the only reason. Let’s explore what makes healthcare so attractive to threat actors.
The inherent value of medical data
The healthcare sector holds immense value in medical data. From patient records, research, and development to pharmaceutical data, healthcare organisations have a wealth of information that is highly sought after by cybercriminals. In fact, according to the ENISA report, a staggering 46% of incidents affecting public health involve threats against data. This type of information can be used for various malicious purposes, such as identity theft, insurance fraud, and blackmail.
When patient data is exposed, the consequences can be severe for both individuals and organisations, and attackers are well aware of this. Organizations risk lawsuits, financial loss, and reputational damage, making them desperate to find solutions in the event of an attack. Cybercriminals exploit this urgency as leverage to demand high ransoms for the sensitive information they have stolen.

Interconnected systems: A broader attack surface
Hospitals and healthcare providers operate within a web of interconnected systems and devices, from advanced medical equipment to comprehensive IT networks. Although this is beneficial for the operation of the organisations, it can also wreak havoc fairly quickly in the event of an incident. If cybercriminals compromise only one of these network systems – usually an older one that is not properly secured – they can exploit this weak link to infiltrate the entire network, compromising interconnected systems with ease. This extensive interconnectedness gives cybercriminals a larger attack surface, amplifying the potential for widespread disruption and data breaches throughout the healthcare network.
Resource limitations are exploited by cybercriminals
Despite the critical importance of protecting patient data, many healthcare organisations face resource constraints in cyber security. Tight budgets often force these organisations to prioritise immediate patient care over necessary technology upgrades. This trade-off results in outdated systems that can’t defend against modern cyberthreats, creating significant vulnerabilities.
Additionally, the healthcare sector has a significant shortage of skilled cyber security personnel. The demand for these experts far exceeds the supply, leaving many organisations without the necessary expertise to defend against sophisticated cyberthreats. The cyber security talent gap is a critical issue, as healthcare organisations struggle to compete with other industries for qualified professionals. This shortage means existing IT staff are often overworked, trying to manage both routine IT operations and complex security tasks. The lack of dedicated cyber security staff leads to inadequate threat monitoring, slower response times, and an overall weaker security posture.
The compliance trap: Following regulations does not mean real protection
The lack of resources in healthcare organisations has additional far-reaching consequences, particularly in how security efforts are prioritised. Often, these organisations are forced to focus their limited security resources only on meeting regulatory security compliance requirements.
Regulatory standards are necessary to avoid legal penalties, and they provide a baseline for security practices, but they are often not sufficient to protect against the sophisticated cyberthreats that healthcare organisations face today. This focus on compliance over comprehensive security leaves organisations in a vulnerable state where they lack proactive measures to protect their organisation. Besides, this approach can create a false sense of security, where healthcare providers believe they are more protected than they are to detect, respond to, and recover from cyber incidents, which puts patient data and overall system integrity at continual risk.
Organizations should invest in a security solution that can not only ensure compliance but also tackle other crucial aspects of cyber security protection, such as human risk reduction and personalized awareness training.
Primary targets: The most vulnerable healthcare organisations
Several types of healthcare organisations are particularly vulnerable to cyberthreats, mostly due to the potential of disruption they can cause and the type of data they hold.
According to the ENISA report, hospitals are the most targeted organisations in the healthcare sector. Cyberattacks on hospitals can disrupt critical healthcare services and compromise patient data, causing significant financial and legal consequences. One of the many cases of cyberattacks on hospitals happened recently, when the hacker group LockBit hacked a hospital in Cannes, France and released confidential data from their patients after the hospital refused to comply with their ransom demands.
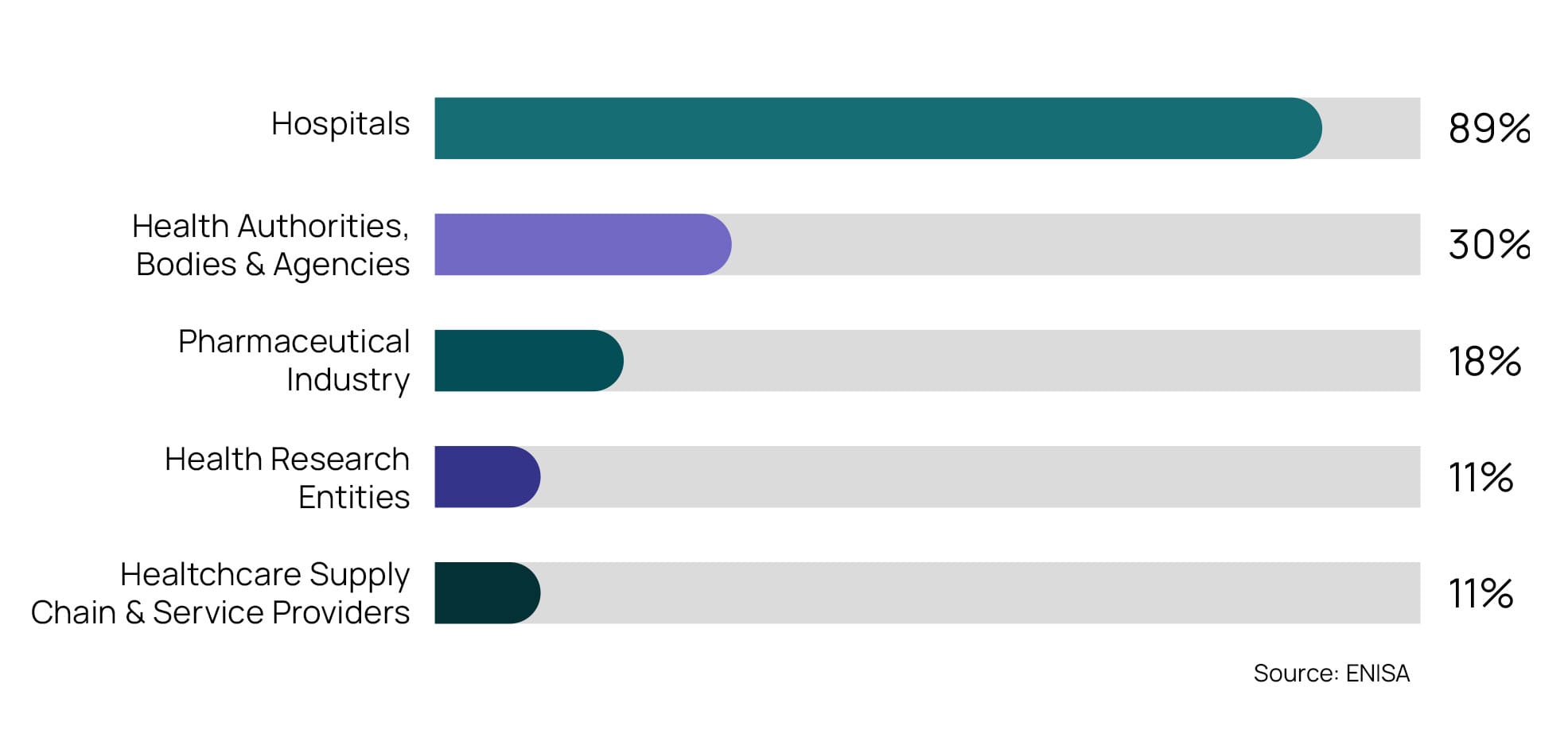
Health authorities, bodies, and agencies are the second most targeted organisation type. Since they often belong to governments, they are targeted by state-sponsored actors, hacktivists, and independent hackers. These organisations play vital roles in healthcare governance and public health initiatives, so attacks can compromise crucial public health data or disrupt emergency response coordination. For example, several years ago, an attack on the Healthcare Service Executive (HSE) organisation in Ireland caused €100 million in damage and compromised the personal data of 100,000 people. In 2022, another cyberattack took down the non-emergency 111 service line and affected mental health services and emergency prescriptions management systems.
The pharmaceutical industry is the third most targeted type of organisation. Pharmaceutical companies hold important information about drug development processes, intellectual property, and patient data safety, making them a lucrative target for cybercriminals. Besides, an attack on a pharmaceutical company can impact many different health institutions, such as hospitals or pharmacies, as it happened in a recent cyberattack to Alliance Healthcare Spain, which caused drug supply delays to pharmacies in certain regions of Spain.
Attacks on the healthcare industry sometimes target third-party providers rather than the healthcare organisations directly. For example, as highlighted in the introduction, in the largest cyberattack ever recorded in France, two of the leading providers of medical third-party payment in France were hacked, compromising the personal information of 33 million citizens.
In some less frequent cases, hackers target health research centres, seeking valuable information on new studies or unpublished data. Once they have this information, they threaten organisations and demand a ransom.
Strategies for preventing cyberthreats in healthcare
Hospitals and healthcare organisations need to actively work on their security protocols and employee education to protect their systems and ensure the integrity of patient data. Here are some strategies that work towards that goal:
- Conduct regular risk assessments: Regular risk assessments should be a core part of the cyber security strategy and business operations of healthcare organisations. It enables organisations to identify potential vulnerabilities in their systems and implement the right security measures to eliminate them.
- Incident response plans: Healthcare institutions must have an incident response plan that highlights the steps to take to restore systems and minimize potential damage to patient care or data integrity in case of a breach. These plans need to be updated regularly based on knowledge from previous incidents.
- Third-party risk management: Healthcare organisations must proactively evaluate and manage security risks associated with third-party vendors. This includes prioritizing vendors based on data sensitivity and service criticality, establishing clear contractual agreements with cyber security requirements, and regularly monitoring vendor security postures.
- Identity access management (IAM) and asset management: IAM plays a crucial role in ensuring that only authorized personnel can access necessary resources precisely when needed. Healthcare providers must find a balance between allowing quick access to patient data for medical needs and protecting this sensitive information from unauthorized breaches.
- Biometric security: Embracing technologies like biometric authentication can enhance data integrity and user authentication. These systems provide a reliable method of user identification, reducing the risk of unauthorized access.
- Protect IoT devices: Healthcare providers must prioritise the implementation of advanced security protocols for IoT devices. This includes regular software updates, the use of strong, unique passwords, and the installation of security layers, such as firewalls and encryption. Additionally, there should be a continuous assessment of the security measures in place, adapting to new threats as they arise.
- Establish leadership in digital transformation: Healthcare organisations should choose a dedicated person, such as a Chief Information Security Officer (CISO), to lead their digital transformation efforts. This person needs to understand how important digital changes are and be able to guide the organisation’s security strategies.
- Compliance with data protection laws: Compliance with national and EU-wide data protection laws is essential to keep a baseline of security. However, as previously mentioned, they need to be accompanied by a more holistic human risk management strategy to achieve a real risk reduction.
- Strengthen the human factor: Technology alone is insufficient against sophisticated social engineering attacks. Healthcare organisations must strengthen on the human factor through human risk management to improve their security, including implementing personalized and continuous employee training programmes and targeted interventions that are tailored to the specific challenges of the healthcare sector.
Protecting public health: How SoSafe can strengthen the cyber security of your healthcare organisation
Healthcare is under constant pressure to defend against very sophisticated cyberattacks with very few resources, which is why it is important to be mindful and invest in the most efficient security measures. Considering that 68% of cyberattacks originate from the human factor, mitigating and managing human risk should be an area that all healthcare organisations need to protect. However, there is much to be done regarding human risk management. In fact, according to the ENISA report, 40% of the organisations have no security awareness programme for non-IT employees, and 46% have never performed a risk analysis.
SoSafe is the leading provider of human risk management services. Our human risk management platform reduces human risk through personalized training and phishing simulations tailored to your employees’ knowledge, roles, and risk levels. For example, if someone in the organisation is responsible for handling sensitive data, the training will tackle the risks and security best practices they should know to keep that data private. Our E-learning platform also has specific modules about security in healthcare, ensuring the training is personalized and covers all the needs of such an important sector for society.
Once the training has started, our Human Risk OS helps you identify risks in real-time, gain behavioural insights, monitor the state of your security culture, and automate targeted interventions accordingly. By effectively managing human risk and strengthening your organisation’s security culture, you can better protect patient data and ensure the safety and well-being of individuals and communities. If you want to see first-hand how SoSafe can help you with that, book a demo with one of our experts today.






















