Phishing
What is phishing?
Phishing is a type of scam in which cybercriminals try to steal access credentials, bank information, or other sensitive data – usually via email. Phishing emails are a very common tactic among attackers because their victims’ email addresses are often easy to get their hands on and the emails are free to send. The criminals have a wide range of methods for acquiring their targets’ contact information, the most common of which are scanning websites, mailing lists, and Internet forums and social media platforms, buying data from third-party providers on the dark net, and generating automatic email addresses.
The attacks can occur both in our personal and work lives, and almost always follow the same pattern: The cybercriminals send fraudulent messages in which they pose as trustworthy persons or organisations. While doing so, they manipulate the reader’s emotions and create a sense of urgency – such as with an urgent warning or the possibility of a big reward – to keep the victim from thinking critically about the message. This method for inducing someone to perform certain actions or disclose sensitive information through psychological manipulation has a name: social engineering.
Phishing can refer not only to conventional phishing via email, but also to other social engineering methods. Two other examples are vishing (voice phishing – the theft of sensitive data via telephone or voicemail) and SMS phishing, also known as smishing (sending fraudulent text messages that lead users to nefarious websites via smartphone).
No matter the method, the goal is always to make money from the data that has been stolen, which makes successful attacks particularly damaging to companies. In fact, according to IBM, a cyberattack or data incident within a company costs an average of four million USD, although the sum can be much higher. That’s why it’s essential that all employees learn how to avert security risks.
Looking back: The beginnings of phishing
Phishing is one of the many new household terms to come from digitization and information security in recent years. Phishing as a term originated in the hacker scene, and there are several theories about how exactly it came to be. One possible origin is that it came from a portmanteau of fishing and phreaking. The term describes the use of bait – in this case, fake emails or websites – to “fish” for sensitive information. The spelling with “ph” comes from hacker-speak, as hackers were originally known as “phreaks”. Another possible etymology suggests that the term is a combination of password and fishing.
One of the first modern phishing scams arose in the mid- ‘90s. America Online (AOL) was the leading Internet provider at the time, with millions of daily users sending billions of messages. Its enormous popularity was inevitably a draw for criminals: Hackers from the “Warez Community”, a group of cybercriminals that communicated over AOL, are considered the first “phishers”. Members of this community posed as AOL employees in emails and instant messages, which allowed them to steal passwords and other sensitive information from users.
The hackers were then able to use the data they had stolen and an algorithm they had developed to generate random credit card numbers. They were only able to make a few random hits, but this was enough to have serious consequences for the people affected. With the credit card numbers, the hackers could open new AOL accounts that they would use for various fraudulent activities, such as sending spam to other users. AOL supposedly put an end to this scam when it updated its security measures in 1995.
Imitation attacks – the preferred method
AOL’s security update didn’t put an end to phishing attacks, however. In fact, the success that the attackers achieved with relatively simple means led to many copycats. The criminals started using imitation attacks, a new type of scam in which they posed as trustworthy organisations in instant messages and emails. The main advantage of these social engineering methods was that user manipulation promised greater success and couldn’t be inhibited by technical security measures. This technique is still widespread: Users receive messages that ask them to verify accounts or confirm invoice data. As this type of scam was still relatively new at the time, most users fell for the trap. AOL felt compelled to integrate warnings into its email and instant messenger services to prevent users from disclosing sensitive information in this way.
Attacks against e-commerce and payment service providers
As e-commerce grew, hackers increasingly began to target customers of online businesses and payment systems. By 2003, hackers had registered numerous domains similar to the names of popular websites like eBay and PayPal, and used them to send fake emails to these companies’ customers. The phishing messages aimed to get the recipients to disclose credit card details and other personal information, and then these attacks spread to banks, companies, and their customers. One of the main weapons was manipulated pop-up windows with login screens that would, unbeknownst to the users, record their sensitive information.
What is the difference between phishing, spear-phishing, and whaling?
Cybercriminals have devised a range of methods that fall under the umbrella of “phishing”, giving them an arsenal of means at their disposal for spreading viruses, Trojans, and worms. These cyberattacks come in all shapes and sizes, and can target thousands of recipients or just a few individuals. Knowing the difference between the most common types of phishing attacks – mass phishing, spear-phishing, and whaling – is crucial to staying safe.
Mass phishing
Mass phishing refers to the sending of fraudulent emails to as many recipients as possible. This is a very common attack method because it’s fast, easy, and cheap. The criminals blindly send the exact same email to a large number of email addresses in the hope that as many people as possible will take the bait. The messages are not personalized and can target individuals as well as a company’s employees.
Spear-Phishing
Spear-phishing is a particularly sophisticated and personalized type of cyberattack. Unlike mass phishing, which has no specific target, spear-phishing is geared toward victims who were determined in advance – sometimes to the point of being spied on for months in the lead-up to a spear-phishing attack. The attackers may search for personal information like first name, surname, date of birth, city of residence, street, hobbies, personal interests, and information on family members, friends, and business partners. Spear-phishing messages appear more genuine in most cases because they contain insider knowledge and are tailored to the victim as an individual – a dangerous combination.
Whaling
If spear-phishing is a more honed type of phishing, whaling takes it to the next level. These attacks also target a specific individual, namely in positions of upper management, such as CEOs and CFOs. Like spear-phishing attacks, whaling requires thorough preparation, sometimes over a span of months. This is why they are generally more sophisticated and difficult to detect.
A textbook whaling attack took place in November of 2020, when the co-founder of Australian hedge fund Levitas Capital clicked on a fake Zoom link that installed malware in his network. The attackers attempted to steal 8.7 billion dollars with falsified invoices. In the end they were only able to make off with 800,000 dollars, but the damage to the company’s image had been done. Levitas’ biggest clients terminated their business relationship and the hedge fund had to close down.
Current threats – real examples of phishing
Cybercriminals get very creative with their attacks. New methods and phishing emails are showing up nearly every day, and criminals often make use of current events to make their messages appear genuine. Below are some examples of current phishing methods:
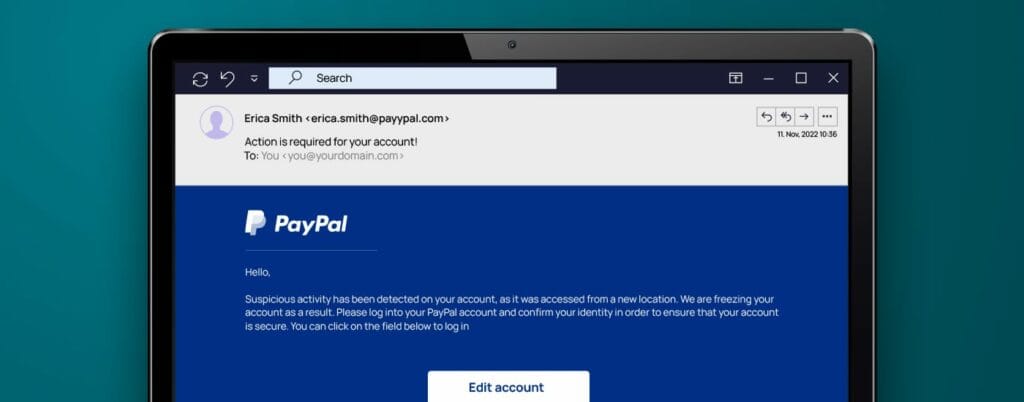
Suspicious activities
An email supposedly from payment service provider PayPal informs the victim that their account has been locked. However, the link in the email doesn’t lead to PayPal, but rather to a fake website.
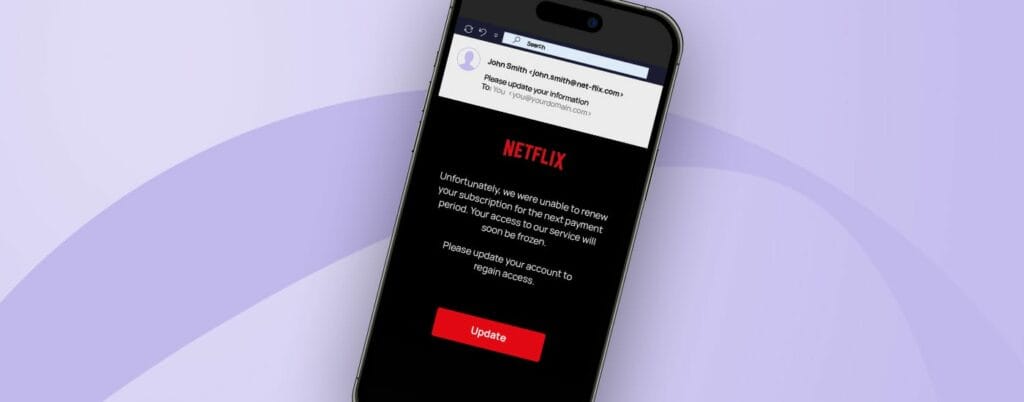
Update account information
Netflix customers were asked via email to update their information because of a supposed problem with their accounts. The recipients were pressured into taking immediate action, as they were told that their accounts would otherwise be locked.
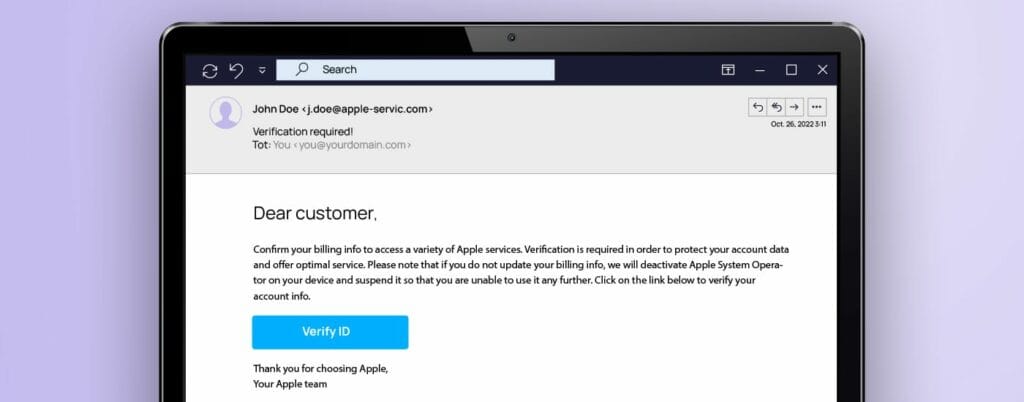
Security check
This phishing email that supposedly comes from Apple informs the recipients that the ID operating system will be locked if they don’t update their billing information.
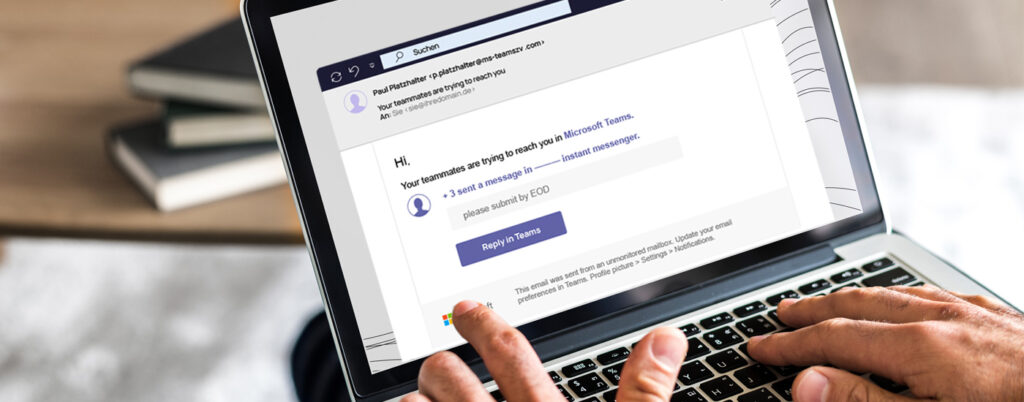
Automated software notifications
This attack is disguised as an automated message from Microsoft Teams, with the goal of stealing recipients’ login credentials. The subject line says: “New activity in Teams,” and informs the users of unread messages in a chat before asking them to click on “Reply in Teams.” However, the link actually leads to a phishing page that records all the data entered in it, such as the username and password for the respective Microsoft Teams account.
Why is phishing so dangerous?
Cybercriminals use phishing emails because, unfortunately, it’s still a highly successful tactic. They can use the data stolen in this way for identity theft, further data theft, unauthorized use of credit cards, account takeovers, malware installation, or the sale of personal information. Such an attack can have serious consequences for the victims.
But phishing attacks can target individuals and entire organisations alike. According to Verizon, 36 percent of all security breaches start with a phishing attack. In the past, all criminals needed to get their foot in the door was send a seemingly harmless email. Phishing messages gave them access to emails and social media accounts of employees, and they then used this information to hack into and manipulate systems connected to them or spread harmful software, like ransomware. For example, all it took was a series of smishing messages to employees of American communications provider Twilio for the cybercriminals to get their hands on the data of more than 125 customers and organisations. To do this, the criminals posed as employees from Twilio’s IT department, which gave them access to login credentials and allowed them to bypass two-factor authentication setups.
According to the Allianz Risk Barometer from 2022, cyberattacks like phishing pose the greatest risk to businesses. The report from the year prior estimated that cyberattacks cost the global economy an unbelievable 1 trillion US dollars per year – 50 percent more than two years before. Some estimates, such as Cisco CEO Chuck Robbins’, go even higher: At the RSA cyber security conference in June 2021, Robbins put this figure at 6 trillion dollars’ worth of damages.
How do I recognise a phishing email?
Most users are aware of phishing nowadays, but the attacks are becoming more sophisticated. Unexpected rewards, sudden warnings, and notifications from banks and service providers demanding immediate action are almost always a red flag. That’s why we have gathered the following steps that will help you recognise a phishing email:
- Check the sender address. In phishing emails, the sender’s name doesn’t always match the email address. Always check the domain (the text after the @ symbol in the email address) if you’ve received a suspicious message.
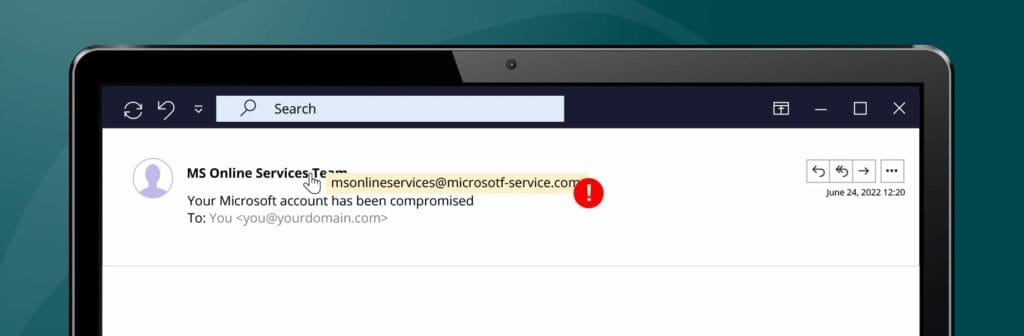
- Keep an eye out for mistakes. Cybercriminals often use automatic translators with imperfect grammar and spelling. This is why many phishing emails contain small typos.
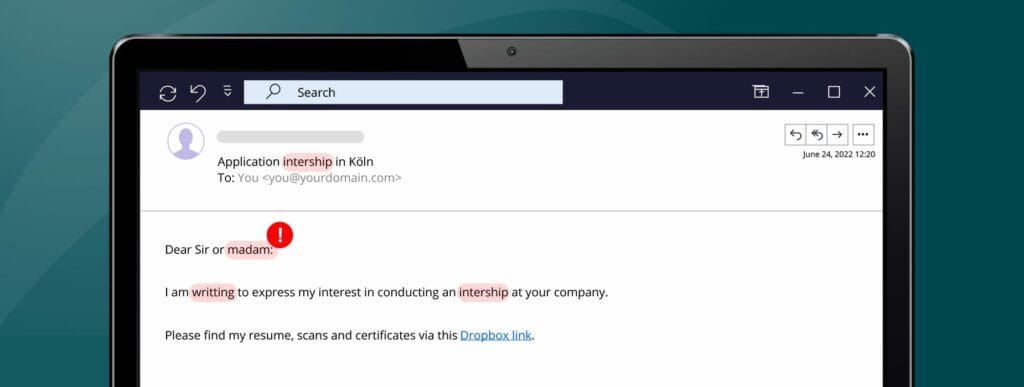
- Be careful with links. If you’ve received an unexpected email, it’s best to check all the hyperlinks before you click on them. If you drag your cursor over a link, you will see whether the URL matches the link’s supposed destination.
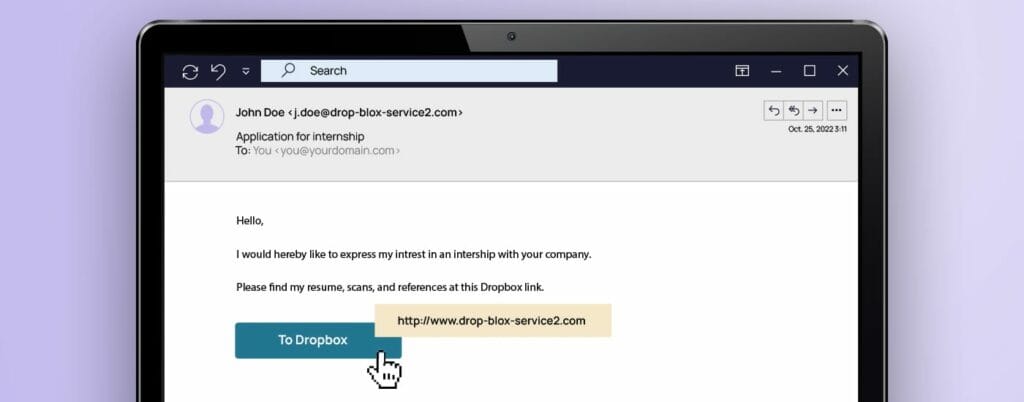
Phishing poses a real threat, both for individuals and for organisations. Often all it takes is one careless click on a link to become the next victim. Since you will probably be faced with such an attack yourself sometime, you should know what to look out for. If you want to learn more about how to deal with an attack, read our blog post: “How to spot a phishing email | 6 tips for employees.”
How to protect yourself
If you carefully check each email for signs of a scam, you will reduce the risk of a successful phishing attack considerably. There are also some behaviours you can adopt to mitigate this risk even further:
- Don’t open any suspicious attachments. This may be the most important rule of all: Don’t click on any attachments if you aren’t 100 percent certain that it is genuine. Attachments in a phishing email can install malware onto the computer upon being opened. If you’re not certain, contact your IT department or get in touch with the supposed sender by other means.
- Don’t send any confidential information. Legitimate companies will never request sensitive or personal information via email. If an email requests credit card information, social security numbers, or other details, do not provide this information. If you’re not sure what to do, call the company’s customer support. But remember: Look up the number yourself, and do not call the number provided to you in the email.
- Trust your instincts. People are good at noticing deviations from their routines, especially when they pose a threat. Contact your IT team if you have even the slightest feeling that something is off with a certain email.
Phishing is always a threat: How can companies protect themselves?
The digital world demands new approaches to cyber security. From multinational corporations to medium-sized companies, nobody is entirely safe. According to the Human Risk Review 2022, one-third of people in charge of cyber security who were surveyed say that their company or a service provider has been affected by a cyberattack. Even though 90 percent say that awareness is important, more than 40 percent of organisations surveyed say that employees aren’t sufficiently informed of the dangers of phishing and cyberthreats. This lack of awareness of security risks is one major reason why phishing is one of the most frequent causes of costly cyberattacks and data breaches. According to the DBIR 2022, 82 percent of all data protection violations are caused by a human factor.
In addition to the necessary precautions, the establishment of a security culture is essential. Companies should continuously communicate the relevance of cyber security and the dangers of cyberthreats, while motivating employees to abide by the security requirements. But there is a silver lining: There are many ways to do this, from training and e-learning platforms to attack simulations and early, tech-supported identification of vulnerabilities.
SoSafe offers attack simulations rooted in behavioural science that, in combination with gamified e-learning, continuously teach employees about the dangers of phishing. Learn more about how SoSafe’s Phishing Simulations work and how you can help strengthen your organisation’s security culture.


















