Discover how our phishing simulations turn your employees into active defenders of your organisation.

Human Risk Management
6 ways to detect a phishing email – with examples
No time to read? Listen instead:
The notorious cyberattacks in recent years have raised the alarms of endless organisations across the globe. These include NotPetya, the SolarWinds attack, and the log4j vulnerability, to name a few. We are now facing an innovative dark economy in which cybercrime-as-a-service is a common business model and phishing attacks continue to increase in number and impact despite the advances in detection technology.
The pandemic worsened this threat landscape as it shifted work patterns with the arrival of remote working. Most employees don’t have enterprise-level cyber security at home, and some even connect with their own devices, which gives attackers a higher chance of successful phishing campaigns. Now it seems that hybrid and remote work models are here to stay —pandemic or no pandemic— and phishing continues to evolve. In fact, the Zscaler’s ThreatLabz research team noticed a 29% increase of phishing attacks in 2021 compared to 2020.
All these events have shown that people are still the primary gateway for criminals, with more than 82% of all attacks originating in the human factor. In our Human Risk Review 2022, we anonymously evaluated over 4.3 million simulated attacks from 2021 and the data showed that 2 out of 3 users open phishing emails, while almost every third user clicks on links, attachments, or other harmful content.
Phishing is a serious threat to both employees and businesses and it is therefore vital to learn how to avert security risks. That’s the main reason we have created this guide to help employees spot any phishing attempt that lands in their inbox.
But first, let’s look at what a phishing attack is.
What is a phishing attack?
Phishing is a type of social engineering attack, mostly carried out via email. This email is sent to a recipient with the aim of making this person perform a specific task like clicking on a link, opening an attachment, or providing sensitive data such as credit card numbers or login credentials. Cybercriminals love to use phishing emails because they are easy to obtain, free to send, and very effective. With zero to no effort, hackers can quickly gain access to valuable data.
Other popular types of phishing attacks are vishing, in which cybercriminals use phones and voice-altering software to trick users into providing personal information, and smishing attacks, which are carried out over text messaging. Moreover, after the pandemic hit, collabouration tools went into much wider use and cyberattackers are now ramping up efforts to target employees on additional platforms such as Microsoft Teams and Slack.
Similarly, many ransomware attacks on supply chains begin with phishing. One striking case was the Kaseya attack in July 2021, in which a number of managed service providers (MSPs) and their customers became victims of a ransomware attack that caused widespread downtime for over 1,000 companies. Incidents with these fatal consequences illustrate that employees are an active part of the solution to cybercrime and that a strong security culture is essential in every organisation.
Most common email phishing attacks in organisations
Email phishing attacks, sometimes even used in tandem with vishing, smishing, or other forms of cyberattacks, can come in any shape and size, and all employees in an organisation, including the C-levels, are at risk of falling victim to them. The most popular techniques among hackers, malware developers, and other threat actors are:
Mass phishing
Mass phishing is one of the most common types of phishing attacks used by hackers. It basically consists of sending scam emails to as many people as possible to extract sensitive information from them. They are not personalized nor targeted to a specific individual or a company, hence its name. An attacker that sends out thousands of phishing emails can still net significant information and sums of money, even if only a tiny percentage of recipients fall victim to this type of cyberattack.
Spear phishing
Spear phishing is a more sophisticated version of phishing, as it targets specific individuals, businesses, and organisations with the objective of gaining unauthorized access to confidential data.
Attackers normally achieve this by acquiring personal details on the victim such as their location, friends, or employer using their social media accounts and other pieces of personal information available online. The attackers then disguise themselves as a friend or trustworthy entity to acquire sensitive information.
One of the top spear phishing techniques is CEO fraud, in which the attacker impersonates a C-level executive, often the CEO, to try and fool an employee in the Accounting or HR departments into carrying out unauthorized wire transfers or sending out confidential tax information. One famous example is the Snapchat case, in which employee details were accidentally sent to an attacker after an employee fell for a phishing email that was supposed to have come from the CEO.
Whaling
Whaling is another type of cyberattack aimed at top managers and C-level executives. Attackers send what seems to be a legitimate email from a trusted source, often an employee within the company, a partner, or a vendor. The executives are asked to share sensitive information such as payroll information or bank account numbers, or even to authorize a wire transfer to a fraudulent bank account. One characteristic example happened in November 2020, when the co-founder of the Australian hedge fund Levitas Capital followed a fake Zoom link that installed malware on its network. The attackers attempted to steal $8.7 million using fraudulent invoices. Although they only ended up gathering $800,000, the reputational damage was enough for Levitas’ biggest client to end their relationship, forcing the hedge fund to close.
6 tips on how to detect a phishing email
We have already covered the impact that a phishing email can have on both employees and organisations. Let’s now have a look at the different ways employees can spot a phishing email and become more cyber resilient:
1. Don’t trust the display name —always check the email address
A classic plot used by cybercriminals is to alter the display name of an email in order to impersonate a company while emailing you from a completely different email. If the email originated from an organisation with which you often correspond, you can check the sender’s address against previous emails from the same organisation. If not, you can also check the address to make sure there are no other warning signs such as typos or strange wording before “.com”. Here’s an example:
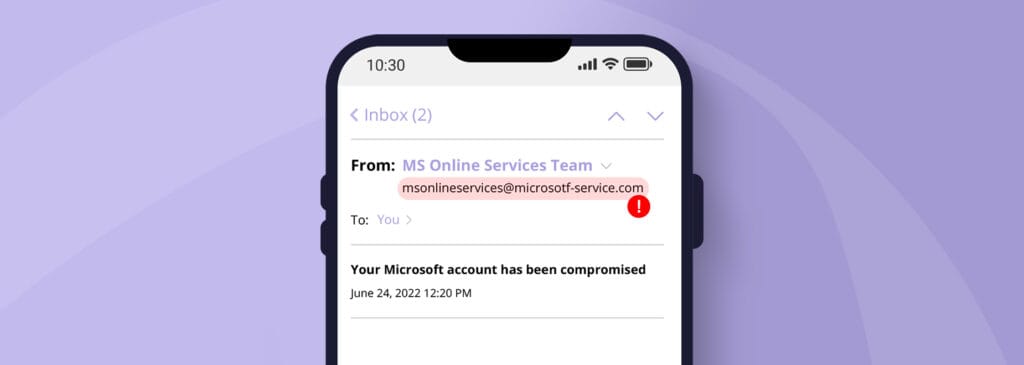
If you want to display sender details, there are different ways depending on the device being used. On desktop devices, move the mouse over the name without clicking on it. On mobile devices, you can view details from the sender after you have opened the email. Usually there is a small arrow in the rightmost header that you can click on. On some devices you can also keep the sender’s name pressed a little longer and then more details will be displayed.
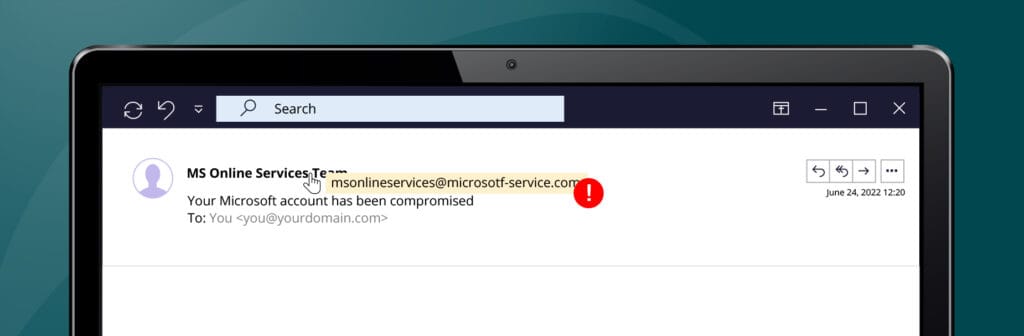
2. Is the salutation too impersonal? Then, think twice.
Mass phishing campaigns always use impersonal salutations such as “Dear customer” or “Dear Sir or Madam”. If the email is addressed vaguely, then it is probably a scam. Legitimate businesses normally use your first and last name.
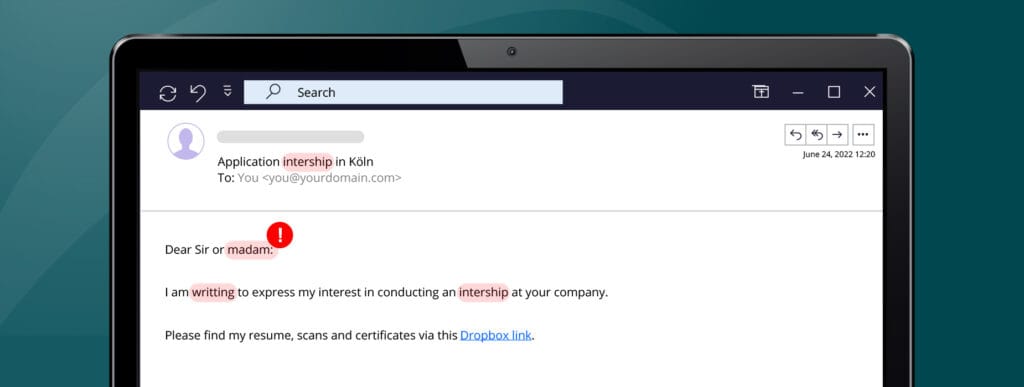
3. Check for spelling mistakes or unnatural language
Trustworthy businesses usually pay close attention when crafting emails to their customers. Even if hackers have become more sophisticated with their attacks, they still make basic mistakes, especially in mass phishing campaigns. If the text contains spelling or grammar mistakes, or the formatting seems off, the email is more likely fraudulent.
Make phishing attacks miss the mark
4. Stay calm, even if the email creates a sense of urgency
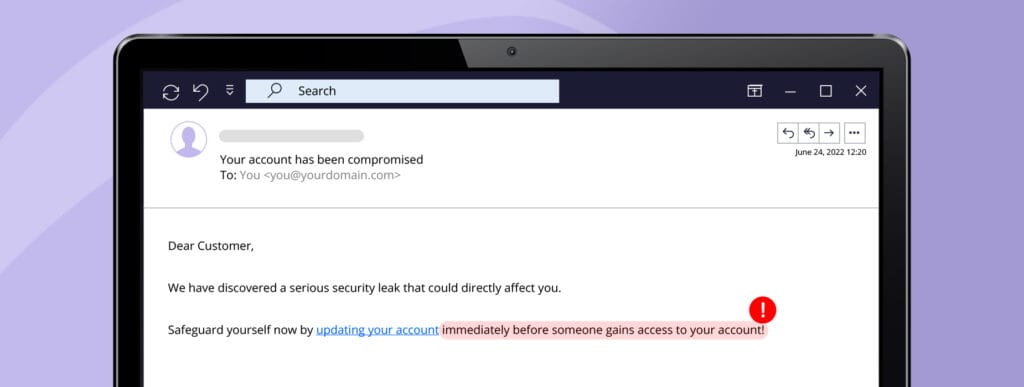
In most phishing attacks, people are asked to act quickly to get a reward or to avoid punishment. Cybercriminals often use this approach to rush their recipients into action before they have time to think clearly and analyse the email for spelling mistakes, flaws, or inconsistencies. Try to stay calm when receiving important requests and study the email before clicking on a link or sending any sensitive information.
5. Don’t share sensitive information hastily
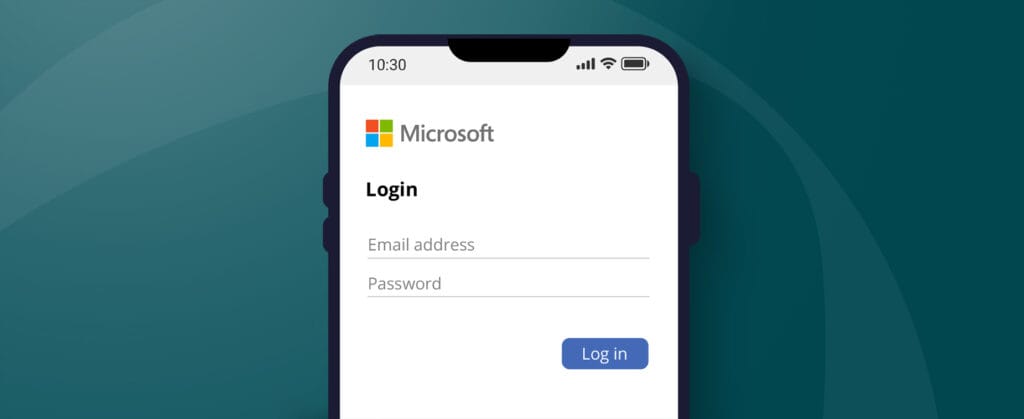
The target of a phishing email is usually the entry of personal data or the execution of a money transfer. Spear phishers can create login pages that look like the real ones and send an email containing a link that directs the recipient to the fake page. Don’t share sensitive information when receiving an email like this one unless you are 100% certain that the email is legitimate. When in doubt, we recommend you reach out to the company or a trusted contact person directly for confirmation.
6. Watch out for unexpected email attachments or suspicious links
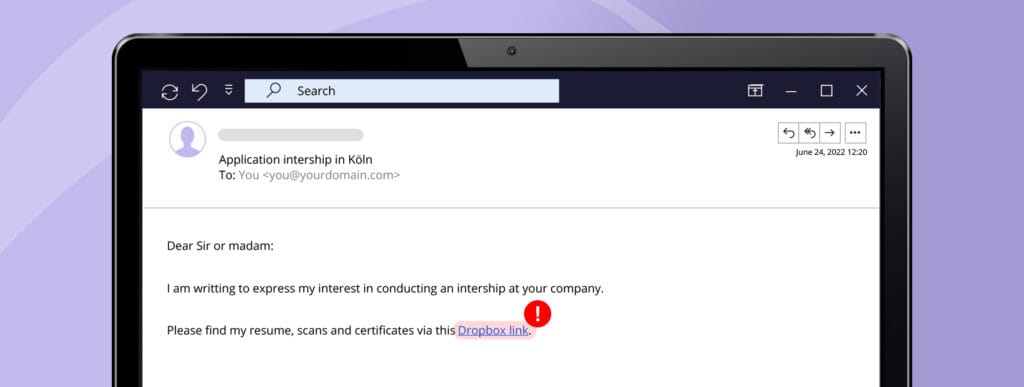
Phishing emails usually contain links, attachments, or forms that the victim is supposed to open. Most work-related file sharing is now taking place in collabouration tools such as Google Drive, OneDrive, or SharePoint. If you receive an email with suspicious links or with attachments, especially if they have unfamiliar extensions, treat them suspiciously and ask your colleague about it on your usual communications platform.
How can organisations and employees protect themselves from phishing attacks?
Today’s digital world is very different from what previous generations experienced, and security risks are inevitably arising in every organisation. The security measures of any business or organisation are only as good as their security culture and, therefore, regular staff awareness training becomes an essential piece of the cyber security puzzle.
From using behavioural science-based training to receiving phishing simulations accompanied by engaging education pages, organisations now have numerous tools to scale their security cultures with ease. SoSafe’s awareness platform manages human risk with people always front of mind. Either if you are in charge of the security in your organisation and want to learn how our phishing simulations can help you scale your security culture, or you are an employee and want to put your security awareness to the test, you can try our phishing demo to experience our product first-hand.






















