
Human Risk Management, Phishing Simulations
How to successfully run a simulated phishing campaign in 6 steps
Picture the scene: Payday is fast approaching. Your employees have multiple bills to pay and rely on prompt company payment to manage their finances. Suddenly, they receive an email with the subject line “Payroll accounting error.” Naturally concerned, they open the email, which explains that they must urgently update their bank details by clicking on the link to receive their payment.
In a real scenario, this situation could have severe consequences, crippling the security team and damaging your company’s finances and reputation. However, a phishing simulation campaign transforms the situation into a valuable learning opportunity. By exposing your employees to these scenarios in a low-risk, controlled environment, you can effectively train them to recognise and respond to these threats.
While phishing attacks may sound like a thing of the past, they are very much still relevant and continue to have success by preying on human psychology, no matter the technological advancements. Research from our Human Risk Review 2024 confirms this: Phishing is still the number one tactic used in successful attacks, with 51% of security leaders reporting that their organisation has been targeted via email.

For maximum impact, phishing campaigns should be thought out meticulously, and certain aspects, such as previously communicating with employees and proper planning, can have a large impact on their effectiveness. In this article, we show you how to run a successful phishing campaign in just a few steps.
Step 1: Plan your phishing simulation strategy
Every successful phishing simulation campaign begins with careful planning. Security teams must start by defining the simulation goals and scope, such as the number of employees to target, the complexity of phishing emails, and the types of scenarios to include.
If you’re new to planning this type of campaign, it’s best to start simple and see how your employees react to the first simulation. If you have run phishing simulations before, now might be the perfect time to start defining different strategies per user groups, such as recent hires versus long-time employees or by department.
To establish a clear strategy that best meets your needs, ask yourself a few questions before moving to the next step:
- What are the objectives of this phishing campaign? Common goals include training employees, assessing vulnerability levels, and ensuring compliance with regulatory frameworks.
- Which type of emails are being used to target your industry or sector? This helps you choose which scenarios to include in your simulations. It’s essential to plan campaigns that reflect the latest phishing tactics to ensure training remains current and effective.
- What is the base knowledge across all employees? Simulations cannot be too easy or too difficult. They need to adapt to your organisation’s current awareness level. When this increases, it’s important to vary the difficulty of phishing emails to keep employees challenged and engaged.
- Which are the most common file types your employees work with? Identify the most commonly used file types, such as PDF, Word, and Excel, and then use them in your campaign to best mimic real phishing attacks.
- Are some departments more targeted than others? If so, consider whether these departments receive specific phishing attempts and tailor your simulation accordingly.
- How often should phishing simulations be sent? Regularly scheduled campaigns help maintain a high level of awareness among employees. We explore this topic in more detail below.
Once you decide on the main points of your strategy, it’s time to start building out your campaign.
Step 2: Build your phishing simulation campaign
This next step involves crafting the email templates and automating as many processes as possible, including email delivery, onboarding new users into the campaign, and integrating the data into an analytics dashboard. You can also automate email creation if you want to avoid writing them from scratch. Some providers offer a range of customizable phishing simulation templates that adapt to your organisation’s needs and vulnerabilities. But for learning to be maximized, training must be as personalized as possible. With this in mind, SoSafe has developed two different approaches beyond basic phishing templates that leverage the power of personalization to create effective and engaging phishing simulations – targeted phishing and behaviour-based phishing.
- Targeted phishing: One of the most effective strategies involves taking a role-based approach when tailoring emails. For example, finance teams might receive phishing emails related to invoice processing, while IT teams may see emails about system updates. Personalization is key. By sending phishing emails that resonate with specific roles, you can ensure simulations are relevant to each group’s responsibilities and vulnerabilities. Training employees on the specific risks they face in their roles also helps companies achieve compliance with security training regulatory frameworks.

- Behavior-based phishing: This involves adjusting the difficulty, topic, and frequency of phishing emails based on user behaviour and risk profiles. This is the more advanced approach recommended if you have experience in both basic and targeted phishing simulations and want further protection.
Using templates or generating new emails with genAI instead of crafting emails from scratch is just one way to use automation in your phishing campaign. You can also automate employee onboarding, which allows you to quickly include new employees in phishing simulations without manual intervention or even schedule phishing simulation deliveries at varied times and frequencies. Randomizing delivery helps mimic the unpredictable nature of real phishing attacks, making the simulations more realistic and the training more effective. It also prevents employees from anticipating a test and better prepares them for genuine threats.
To gain the most insight, automating campaign tracking and reporting can provide detailed analytics on employee responses to phishing attempts, which we discuss in step five.
Step 3: Inform employees before launching
Once you’ve created your templates and automated as many processes as possible, then announce your plans. The key is advance notification instead of surprise. This helps avoid confusion and motivates your employees to take part in the simulation. It’s best to start spreading the word a few weeks before the start of the simulation, perhaps through a company-wide email or in a CEO communication in an All-Hands Call.
However you choose to tell your employees, be sure to include details like the reason for creating such a campaign, what to expect, and when it’s starting, but there’s no need to specify a specific date. Make it clear that the simulation is not a test and there is nothing to be afraid of. They need to understand that clicking on a simulated phishing email will have no negative consequences. And don’t forget to add how the simulation works and who to contact for any questions.
Step 4: Launch your campaign and start empowering employees
Now, it’s time to launch the campaign and start understanding how your teams react. For phishing simulations to serve as an education tool rather than a testing tool, they must educate and empower.
Training after clicking is essential – not just beneficial – for safer behaviour in the future. When an employee clicks on a link within a simulated email, they should immediately be sent educational resources like training materials and tips on identifying the main characteristics of a phishing email. This enables them to learn in real-time about what happened, which increases the effectiveness and impact of their learning outcomes. To maximize learning, it’s also crucial to debrief employees in a kind way so that they don’t feel ashamed of any mistakes they made.

Discover how the retail company Freudenberg achieved remarkable
click rates with SoSafe

However, employees should not only receive feedback after making a mistake. Regularly recognizing and reinforcing positive actions – using a behavioural science technique called positive reinforcement – not only supports learning but also keeps employees motivated and empowered.
To receive positive reinforcement through feedback, employees need to be able to report what they detected: either as a real phishing attempt or as a phishing simulation. To do this, they need the right context and reporting tools. A report button, such as SoSafe’s Phishing Report Button, is a useful solution that can be conveniently integrated into your email provider to make reporting quick and easy for your employees.
Once they report the email, they can receive feedback on whether the reporting was on point or not. SoSafe’s Phishing Feedback feature is a good example of how to introduce positive reinforcement in your phishing campaign strategy. And employees always receive an email explaining whether the reported email was a simulated phishing email, a real attempt, or an inoffensive email, which enhances the learning experience by allowing them to learn from their interactions and feeling useful at protecting their organisation.
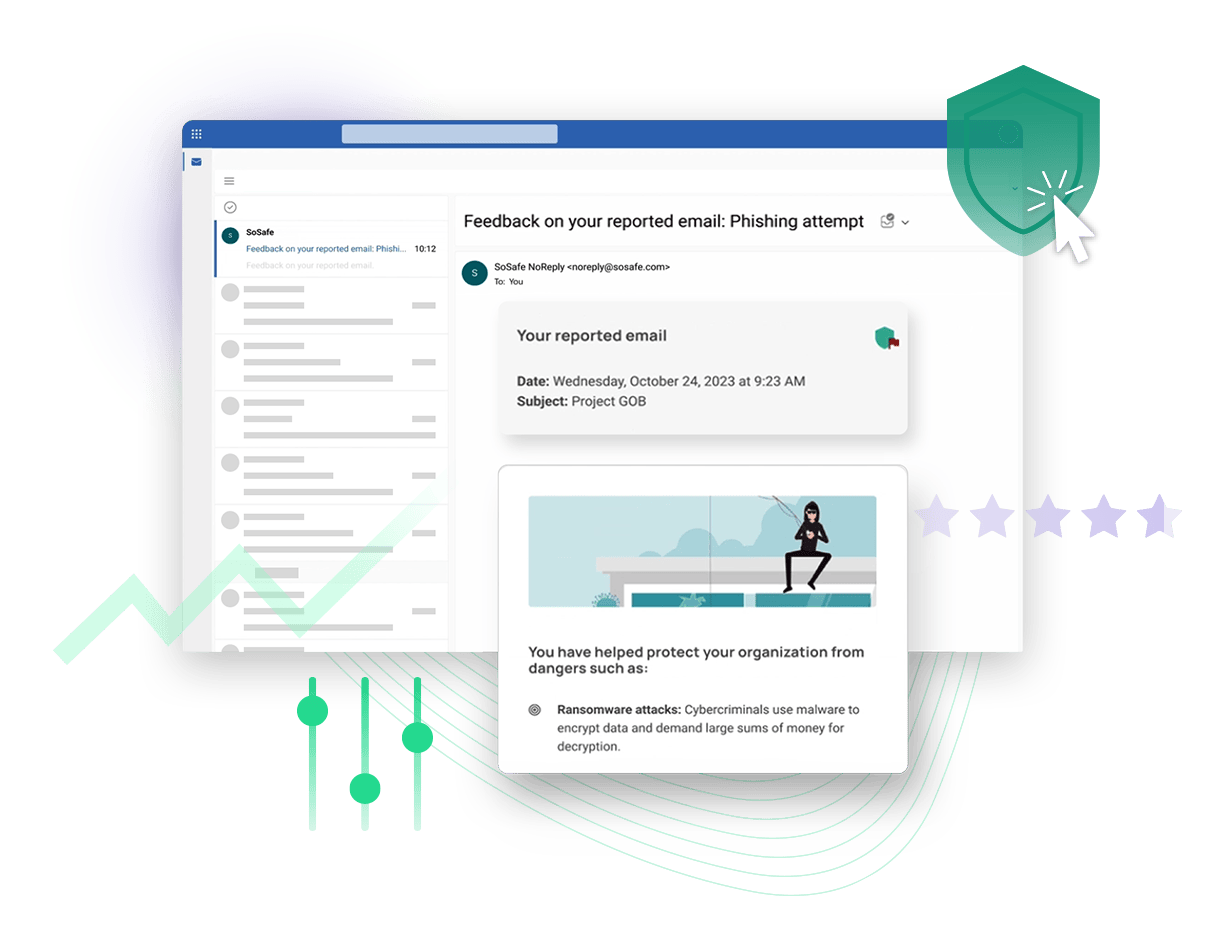
These reporting tools enable quick and easy reporting of suspicious emails and allow you to gather data on user behaviour, such as which departments are more proactive in reporting. They can also empower employees to act as an extension of your security team by helping them stay aware and allowing them to easily send attack attempts your way.
Step 5: Measure and analyse
Evaluating and interpreting the outcomes of your phishing simulation campaign is a crucial process that cannot be overlooked if you want to maximize its benefits. This stage allows you to spot trends, vulnerabilities, and areas for improvement to ensure your campaigns become more effective over time.
While there are many interesting metrics available, we suggest starting with analyzing the interaction rate, click rate, incident reporting rate, and time to reporting to understand how much your employees interact with the simulated phishing emails and how often they identify them as such. This helps you thoroughly assess your organisation’s security posture and pinpoint where employee knowledge gaps exist. But there’s more to analyse. You can aggregate the above rates by geography, role, and function to identify risk levels and analyse the emotional triggers and subject lines that drive more clicks. You can also aggregate them by different context and culture metrics. With this information, you can focus on closing gaps in a specific way by personalizing training rather than making employees redo the entire training.
But improving the effectiveness of future simulations isn’t the only reason these metrics matter. Using this data during discussions with the C-level executives and the board can help persuade them of the effectiveness of security awareness training, ultimately leading to increased support and funding to address any awareness gaps.
Step 6: Repeat and improve
This final step allows you to track progress and enhance employee security awareness. By making the simulation process iterative with regularly occurring phishing campaigns, you can advance employee training and help teams better identify threats with each new round. Repeated training also keeps employees in the know about the latest cyberthreats by receiving updated training materials and resources.
To refine and improve simulations, incorporating user feedback and performance data is essential. For example, perhaps your employees report that they found the simulation too easy or too hard. Maybe performance data shows they are breezing through the simulations, indicating the need to increase the difficulty. Now is the time to revisit your data and feedback so you can make each new simulation even more effective based on what your employees need and their awareness level. A basic campaign can provide some hints for when you decide to carry out more targeted campaigns and which user groups most urgently require your attention.
What’s the ideal frequency for phishing simulations?
Deciding how often to send phishing simulations is a dynamic process that should be tailored to your organisation’s unique needs and circumstances. Key factors, such as the nature of your industry, your level of cyber security readiness, and what the current threat landscape looks like, should always be considered.
You may be eager to schedule phishing simulation campaigns very frequently to see improvement. Far from better protecting your company, running campaigns too often can increase stress and hinder productivity. On the flip side, erring too much on the side of caution and conducting them too seldomly risks leaving employees ill-equipped to handle real-life phishing attacks.
Although there is no cookie-cutter solution, many organisations find a balance by sending one simulated phishing email each month. This regular monthly schedule helps prevent the decay of newly acquired knowledge and keeps cyber security awareness in front of mind for employees. By not overloading them with too many simulations, you’re more likely to maintain their focus and encourage active participation.
Ideally, a simulation campaign should be ‘always on’ and adjusted each time to individual user needs by taking a behaviour-based approach. For example, if employees have low awareness of phishing threats, they might benefit from more than one email per month, whereas if awareness is high, then one email per month is probably appropriate.
How to ensure continuous learning between phishing simulations
The intervals between phishing simulation emails – and between phishing simulation campaigns – are also a great opportunity to strengthen your cyber security measures and foster a culture of increased vigilance. To enhance the effectiveness of phishing simulations, here are some actions to take during these breaks:
- Gain valuable insights: Thoroughly review your phishing simulation reports to enable you to better understand your organisation’s current security posture. For example, suppose the marketing team shows the highest click-through rate on a particular type of phishing email. How can you customize training to help them recognise and combat that specific threat in the next campaign or even adapt to the current one?
- Encourage shared experiences: Enable employees to freely exchange their encounters and observations related to phishing attempts by creating internal forums. This helps cultivate a culture that actively encourages reporting suspicious emails or incidents and where employees can confidently voice security concerns without fear of consequences.
- Strengthen knowledge in high-risk areas: If you can identify areas where your employees need to improve or the knowledge gaps they have, take advantage of the time between simulations to send them learning nudges that bridge that gap. AI-powered tools – like SoSafe’s Sofie – can conveniently and quickly send alerts to all your employees, alleviating the security teams’ workload and providing a highly effective training method.
- Ensure ongoing awareness: Keeping your teams updated on the latest phishing strategies and methods is crucial for long-term protection. One effective way to achieve this is by sending employees bite-size security information that fits perfectly into their workday. By deploying a conversational AI security chatbot like Sofie, employees can not only receive security alerts but also easily initiate conversations and seek clarification on any security-related concerns, promoting a proactive security culture within the organisation.
How SoSafe can help you run effective phishing campaigns
Phishing simulations are a transformative tool that can turn your team into adept cyberattack defenders. One of the key steps in designing your phishing campaign strategy is to tailor it as much as possible to your company and your employees to effectively address their training needs.
That’s why SoSafe offers AI-powered, user-centric simulations that are quick and easy to set up. Targeted emails adapt to the specific employees’ needs of their role and risk profile. In contrast, behaviour-based emails adjust the simulated emails to the user’s behaviour to address their knowledge gaps more efficiently. This provides a safe environment where they can understand, detect, and neutralize phishing attempts, undergoing the right amount of training for them, without taking away unnecessary time from their workday.
Their learning is then complemented by contextual learning pages when they click on simulated emails and instant feedback on every reported email. This process should ideally be combined with a comprehensive learning experience where employees can gain all the necessary knowledge that they can later apply in the simulations, helping bridge any knowledge gaps they may have. SoSafe’s cyber security awareness training has a curated content library where employees can follow bite-sized, story-driven modules that fit perfectly into their workday. The goal is to not only teach employees how to recognise phishing attempts but also to enable them to translate knowledge into safe behaviour.

Phishing threats aren’t going away anytime soon. They remain a highly cost-effective and successful tactic for cybercriminals, and they know it. As these threats persist and prove just as effective as ever, it’s crucial to strengthen our defences and protect ourselves against phishing attacks. To learn more about how SoSafe can equip your team to be more resilient, request a demo with one of our experts.






















