Learn how to tailor your own phishing simulations to your organisation’s needs.

Phishing simulation
What is a phishing simulation?
Imagine a soccer coach who wants to test the team’s defensive skills against penalty kicks. The coach could provide endless lectures on strategy, but the most effective method is to simulate an actual penalty kick. This hands-on approach allows the coach to evaluate the team’s real-world readiness and identify areas for improvement.
A phishing simulation operates on the same principle but in the realm of cyber security. An organisation’s IT department sends out simulated phishing emails to employees that mimic the tactics used by actual scammers, such as requesting sensitive information or prompting the download of a malicious attachment.
The purpose of the exercise is not to penalize employees who fall for the scam but to identify potential vulnerabilities within the organisation. Those who do click on the simulated phishing links are not in trouble. Instead, they become prime candidates for further training. Following the simulation, employees can also receive educational resources to help them recognise the red flags of phishing attempts.
A phishing simulation is, therefore, a practical drill for recognizing phishing threats. It aims to assess and improve your organisation’s cyber security awareness, preparing employees for the eventuality of a real attack. Let’s dive deeper and explore the way these simulations work and how to successfully implement them to maximize your organisation’s defences.

How do phishing simulations work?
Phishing simulations are a great way to practice the lessons learned during the awareness training and create a safe, controlled environment for you to evaluate your employees’ ability to detect and respond to email-based threats. Let’s explore how these simulations typically work:
- Planning and objectives: The process begins with careful planning. Security teams define the simulation goals and scope, such as the number of employees to target, the complexity of phishing emails, and the types of scenarios to include.
- Targeting: The IT or security team selects the employees for the simulation using previously set criteria or by random choice.
- Response monitoring: The security team closely monitors how the employees respond to the simulated phishing emails. They track how many click on links, open attachments, or provide information. Having this data is essential to properly assess the organisation’s susceptibility to phishing threats.
- Education and feedback: After the simulation concludes, employees who interacted with the simulated phishing emails are not penalized. Instead, they are directed to educational resources, such as training materials and tips on identifying phishing red flags. Feedback is provided to help employees understand how they can improve their phishing detection skills.
- Analysis and reporting: Security teams analyse the simulation results to identify trends, areas of vulnerability, and specific employees who may need further training. They often generate a detailed report informing leadership about the organisation’s security posture.
- Repeat and improve: Phishing simulations should occur regularly to allow you to track progress and enhance your employees’ security awareness. The process is iterative, with each simulation further training the employees to better identify threats in the next round while also keeping them aware of the latest cyber threats.

Who can benefit from phishing simulations?
As a vital part of any cyber security strategy, security leaders should consider rolling out phishing simulations to all employees. Cyber threats can be quite indiscriminate, so every team member benefits from some level of readiness.
However, since not every company has the same needs when it comes to awareness, phishing simulations must be adapted to the difficulty, frequency, and topics that are more relevant for each organisation to maximize learning and increase the efficiency of the simulations.
How often should phishing simulations be done?
With phishing remaining the leading attack vector in cyberattacks in 2023, in 41% of cases, the main question is not if you should do phishing simulations but how often you should do them.
Determining the ideal frequency for phishing simulations is a dynamic process and will depend on the specific needs and circumstances of your organisation. Consider factors like your industry, cyber security maturity, and the threat landscape. It is important to remember that simulations that are too frequent can increase stress and reduce productivity, while infrequent simulations may leave employees underprepared for actual phishing threats.
While there’s no one-size-fits-all answer, many organisations have found that conducting one simulated phishing email per month strikes a harmonious balance. This monthly cadence protects the learned information from the Forgetting Curve and ensures that cyber security awareness stays on top of employees’ minds. You’re also less likely to overwhelm your employees with excessive simulations, maintaining their engagement and willingness to participate.
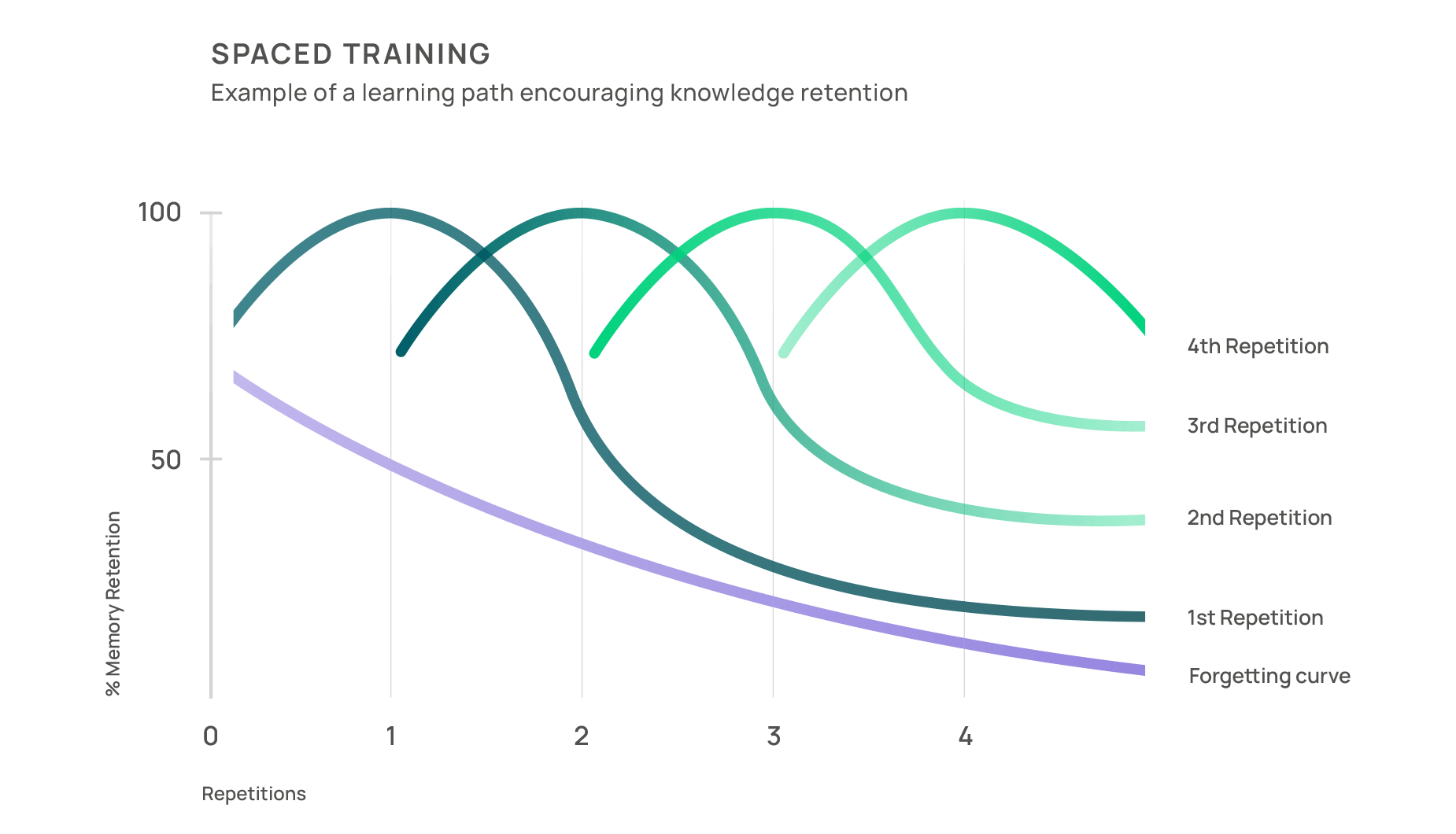
If you believe it’s necessary to conduct more than one phishing simulation per month, you can do that too, but keep the number of simulations under three to avoid overwhelming your employees and making them less invested in the learning process.
Remember that finding the right cadence for simulated emails is a dynamic process, and you may need to adjust it over time. Keep a close eye on your employees’ responses and keep adapting your approach as needed.
5 common myths about phishing simulations
Phishing simulations have become more effective and sophisticated over time, providing a robust and sustainable defence against ever-evolving digital threats. However, not everyone is a fan of phishing simulations, so myths and misconceptions often cloud their practical use. Let’s shed some light on five persistent myths about phishing simulations and uncover the underlying truths.

Myth 1: Phishing simulations lead to uncertainty and mistrust
Phishing simulations are often misunderstood as breeding mistrust and uncertainty in teams. However, they can play a pivotal role in fortifying digital self-defence skills when implemented correctly. Far from instilling fear, these simulations nurture a culture of responsibility and awareness among employees. The secret to their success lies in transparent and effective communication with your employees. By proactively discussing the simulations’ objectives beforehand and making them part of the process, employees are more aware of their role in protecting the organisation and the need to participate in these simulations.
Myth 2: Phishing simulations make employees more vulnerable
Phishing simulations are often thought to increase employee vulnerability to cyber threats. In reality, continuous learning and regular training have proven to significantly reduce susceptibility to phishing attacks. Our platform data indicates a 70% decrease in click-through rate and an 80% drop in interaction rates post-simulation. Similar trends are observed in other studies, including Microsoft’s Digital Defence Report, which shows a 50% annual reduction in employee vulnerability after implementing simulations.
Myth 3: Phishing simulations overwhelm employees
This concern is particularly relevant in the current climate, where IT employees’ burnout rates are higher than ever. However, modern training methodologies like micro-learning and gamification are effectively countering this issue. Micro-learning delivers information in small, digestible chunks to prevent information overload, and gamification adds an element of fun to the training process. By introducing these elements into the simulation, such as providing bite-sized learning moments, users learn without much effort and receive only the minimum relevant information to foster ongoing learning.
Myth 4: Phishing simulations overload IT teams
Contrary to this belief, effective simulations incorporate advanced tools like integrated risk analysis and automated reporting buttons, which reduce the extra effort for IT teams. These features help employees identify suspicious emails, reducing uncertainty and enabling IT teams to focus on genuine threats. Additionally, this approach streamlines reporting and monitoring, significantly easing the administrative load on IT teams. As a result, it not only enhances security effectiveness but also reduces the long-term burden on IT staff, as employees become more knowledgeable and proactive in cyber security matters.
Myth 5: Phishing simulations should ensure a 0% click-through rate
The goal of aiming for a 0% click-through rate can be misleading as it may lead employees to focus solely on identifying simulated emails rather than developing a broader understanding of phishing tactics. Instead, the objective should be fostering broader awareness and employee resilience, enabling employees to recognise real phishing emails. To achieve this, a balanced approach that relies on targeted simulation difficulty and personalized learning is crucial.
Key strategies for successful phishing simulations
To ensure the myths about phishing simulations remain just that – myths – it’s crucial to approach their creation with care. This involves not just avoiding pitfalls that could harm employee resilience or burden IT teams but also actively putting people at the forefront. By integrating principles from psychology and behavioural science, we can craft phishing simulations that are both effective and considerate of our team’s needs. Below are some straightforward strategies that will help you seamlessly incorporate these principles into your phishing simulations:
- Announce instead of surprise: Announcing your plans in advance helps avoid confusion and motivates your employees to participate in the simulation. You can start spreading the word a few weeks before the simulation begins, maybe through a company-wide email or even by turning it into a friendly competition among coworkers. Include details like why you’re doing the simulation, what employees can expect, when it’s starting (no need to give a specific date), how the simulation works, and which person to contact for any questions.
- Training instead of testing: Blaming employees for their actions can hinder their willingness to learn from the phishing simulation experience. By being anonymous during the simulation, employees won’t feel monitored, allowing them to engage at their own pace. The collected data should solely aim to improve learning and not punish unsafe behaviour. It can provide positive reinforcement and tailor learning content.
- Educate instead of criticize: It’s not just about sending out phishing simulation emails. Instead, it’s about helping your employees learn how to stay safe when they actually receive one. After your employees click on a simulated phishing email, they should be directed to useful learning resources to maximize learning at the moment of highest retention. It encourages your employees to be more cautious in the future and empowers them to make safer choices.
- Personalized instead of general: It’s important to tailor the phishing simulation to your employees’ needs. If it’s too easy, it can make it less engaging, but if it’s too hard, it might discourage your employees. So, the trick is to find the right balance. This means combining easy and challenging emails and customizing them for the specific recipients. The goal is making the simulation seem real so that your employees can learn effectively.
Unlocking the full potential of phishing simulations requires a multifaceted approach. Beyond these strategies, there are additional ones to consider, such as ensuring GDPR compliance and implementing effective incident response plans. To discover these and more advanced tactics, explore our guide on best practices for phishing simulations.
Best Practices
Phishing Simulations

Filling in the phishing gaps: What to do in between campaigns
Phishing simulation campaigns should be ongoing to keep cyber security top of mind and ensure a strong cyber security culture. However, there may be instances where there is an impasse between phishing campaigns. During these times, organisations have a chance to boost their cyber security and foster a culture of heightened awareness. It’s important not to consider these as breaks but as pivotal moments for assessment, education, and empowerment. Here’s what to do between campaigns:
- Identify vulnerabilities: Check reports from phishing simulations to see where your cyber security stands. If a specific department consistently has a high click rate on simulated phishing emails, analyse the reason for that and customize your training to tackle that threat. Adjust your defence based on identified weaknesses, choosing targeted learning modules to strengthen your team.
- Take action: Basic training covers general prevention, but it’s crucial to address specific vulnerabilities or departments between campaigns. Run regular campaigns targeting weaknesses to check your progress and ensure regular phishing simulations support ongoing training efforts.
- Maintain awareness: Keep your team updated about the latest phishing tactics. Use MS Teams integrations like Sofie Rapid Awareness to quickly share news and updates within the company.
- Encourage open discussions: Set up internal forums where employees can openly share their phishing experiences, both real and simulated. Create a culture where reporting suspicious emails is encouraged, and foster an environment where employees feel comfortable raising security concerns.
- Reward and celebrate improvements: Praise internal groups or departments that performed the best in your last phishing campaign and identify security champions in each department – people who are passionate about security and have the drive to improve metrics and come up with new ideas. This will ensure that the rest of the department continues making progress.
- Establish executive sponsorship: Make sure you have a C-level champion who can draw attention and resources to your awareness efforts and establish a clear chain of responsibility between managers and employees.
The strategic actions taken between phishing simulations can significantly impact your readiness to combat real cyber threats when they actually happen. Use this time to refine your defence strategies, gain valuable insights from past experiences, and ensure your workforce remains informed, engaged, and adept at effectively countering phishing attacks.
How SoSafe can help you build resilience through phishing simulations
Phishing simulations aren’t just tests – they’re your secret weapon for turning your team into vigilant guardians of digital security. Having a holistic approach that blends theoretical knowledge with practical training is key to enhancing the overall security of your organisation.
By breaking down the complex topic of phishing and similar cyberattacks into bite-size lessons, our micro-learning provides engaging learning experiences that help avoid information overload. Our gamified training methods add an element of fun to training, promoting continuous learning without overwhelming your employees. And our recent feature launch, personalized learning, makes sure that each employee only receives what’s relevant to them.
To reinforce the training process, SoSafe’s phishing simulations create a safe environment where employees can practice what they learned during training. They provide a safe environment to understand, detect, and neutralize phishing attempts. The goal is not only to accumulate knowledge about how to recognise phishing attempts but also being able to translate it into actual safe behaviour.
But what happens once they have identified simulated phishing emails – or even actual threats? A prompt response is key to protect your organisation and minimize risks. This is where the Phishing Report Button comes into action by offering employees an easy way to report threats. This streamlines the reporting process and provides guidance to your employees to make better decisions through our PhishAssist feature. In addition, it lightens the IT department’s workload by automatically filtering out emails from the simulation.
Most importantly, the Phishing Report Button provides insightful data about your organisation’s reporting rate, and when combined with two other key metrics – the simulation’s click rate and interaction rate – contributes to a comprehensive assessment of your organisation’s security posture. These insights are encapsulated in the Behavior Score metric, which quantifies your organisation’s cyber security risk, enabling a more targeted and effective response strategy.
In today’s ever-evolving threat landscape, this commitment to ongoing education is your strongest defence against the relentless tide of cyberattacks. With each simulation, your team grows more resilient, ready to protect your organisation from the next wave of phishing threats.


















