Learn how to tailor your own phishing simulations to your organisation’s needs.

Human Risk Management, Phishing Simulations
How often should phishing simulations be done?
In today’s digital age, where technology is an integral part of our daily lives, the threat of cyberattacks looms large. And among the most common of these threats are phishing attacks. According to our Human Risk Review 2023, 80% of security experts see phishing as a major risk to their organisation, with over 500 million phishing attacks reported in 2022 alone.
To combat this ever-evolving hazard, many organisations have moved beyond traditional security measures and embraced phishing simulations. But these simulations aren’t merely “tests.” They’re ongoing educational initiatives. Here’s how they work: Employees receive simulated emails designed to mimic genuine cyberattacks yet are completely benign. The ultimate objective? To sharpen employees’ skills in identifying and sidestepping potential phishing traps.
In the past, some organisations used these simulations merely to identify “security risks” among their employees or repeated the same scenario. These tactics not only frustrate employees but are also fundamentally counterproductive. The real aim should be employee empowerment. Through phishing simulations, staff members don’t just retain knowledge, but they develop the essential habit of identifying and responding to cyber security threats proactively as they emerge.
So, if you’re pondering not “if” but “how often” to run phishing simulations, you’re already asking the right questions. Timing is a crucial factor, and in this article, we explore two key considerations: whether simulations should be a continuous effort or confined to a set period and how frequently they should occur – weekly, biweekly, monthly, or otherwise.
Why should phishing simulations be an ongoing practice?
Phishing simulations have become a cornerstone in the cyber security protocols of leading organisations globally, mirroring the ever-changing landscape of cyber threats. However, some individuals are of two minds about whether these simulations should be a continuous, evolving initiative or merely a pedagogical tool utilised during specified training phases.
Year after year at SoSafe, we’ve seen just how crucial ongoing phishing simulations are for upping our cyber security games. It’s not just us saying this because behavioural science backs it up, too. Here are a few reasons why:
Continuous skill improvement
Phishing simulations provide a useful method for employees to improve their skills in identifying and responding to phishing attempts. Through regular practice, these simulations help maintain awareness, aiding in recognizing the tactics used by cybercriminals. As time passes, employees become more adept at avoiding actual threats due to these exercises.
Addressing emerging trends
The professionalization of cybercrime has given rise to highly organized criminal groups that employ cutting-edge technologies like AI. These adversaries are relentless in their pursuit of vulnerabilities. Recent research from SoSafe’s social engineering team shows that generative AI tools can compose phishing emails at least 40% faster, and 78% of people opened AI-written phishing emails. Regular training ensures that employees are familiar with traditional phishing attempts and prepares them to identify and thwart sophisticated attacks involving AI and other cyber trends.
Onboarding new employees
If phishing simulations were merely a one-off event or forgotten for months on end, newcomers would miss out on crucial learnings. Ongoing phishing simulations ensure that new employees are swiftly brought up to speed with the organisation’s cyber security protocols, equipped with the essential knowledge to recognise and respond to phishing threats. Including them in these exercises helps maintain a consistent level of security awareness across the board, mitigating the risk of potential security gaps that might arise with staff turnover.
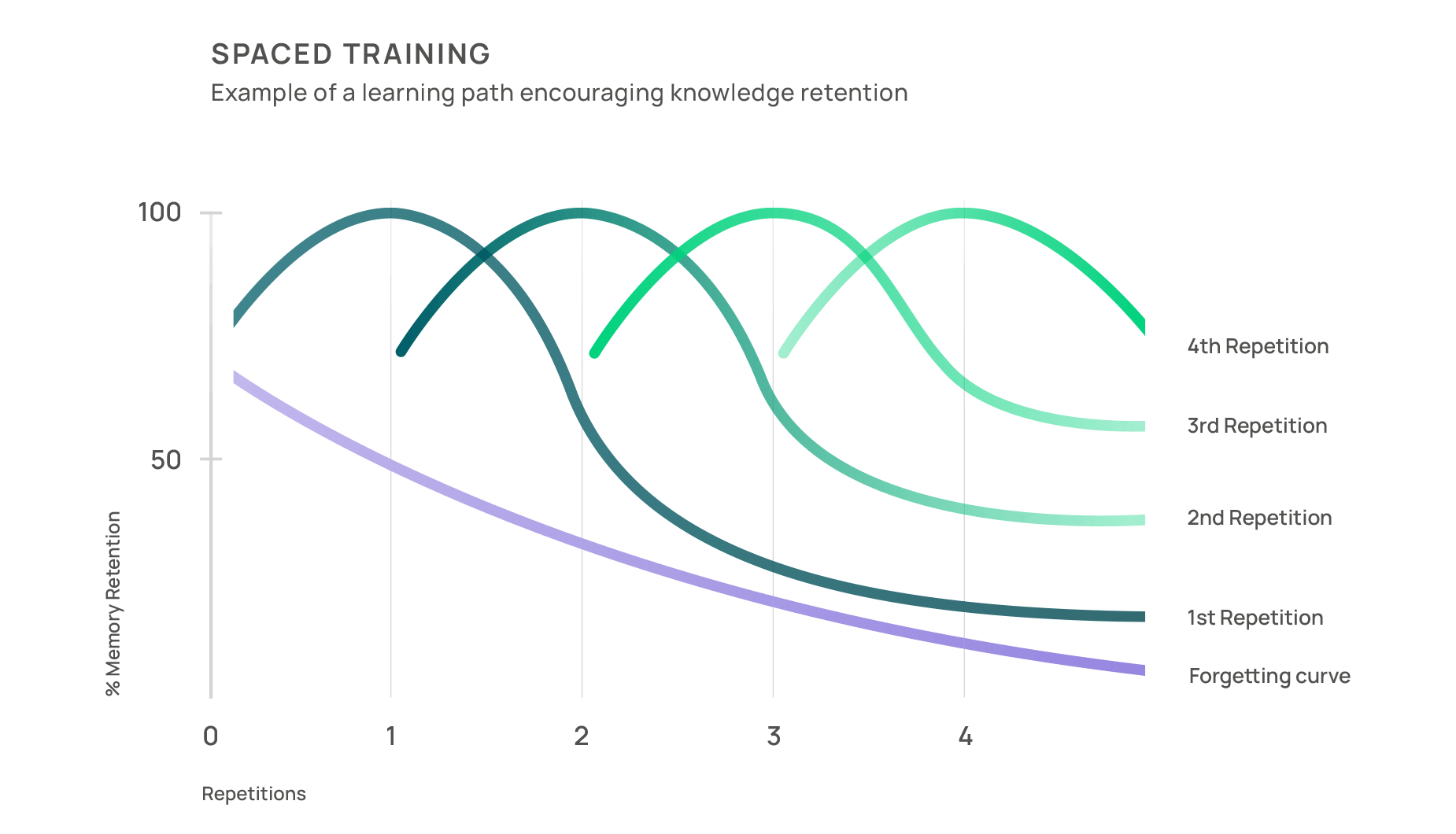
Combating the forgetting curve
According to the findings of scientist Hermann Ebbinghaus, information is forgotten at an exponential rate if not reviewed or reinforced, creating the popular Forgetting Curve. Regular phishing simulations help organisations combat this effect by providing employees with consistent exposure to simulated phishing attacks, reinforcing memory retention through repetition, and allowing employees to practice and refine their skills.
Cultivating a cyber security culture
When conducted regularly, phishing simulations convey that cyber security is a top priority. Employees become more conscientious about online activities and more willing to report suspicious emails or incidents. Over time, this cultural shift becomes a formidable defence against phishing attacks, as employees actively contribute to the organisation’s overall security.
Testing incident response
Regular simulations allow security teams to identify weaknesses in their incident response plans and make necessary improvements. This proactive approach ensures that the organisation is better prepared to mitigate the damage and respond effectively when a real phishing attack occurs.

By providing consistent exposure, repetition, skill refinement, and long-term awareness, phishing simulations help employees effectively retain and apply their knowledge of phishing threats. This proactive approach strengthens an organisation’s cyber security defences and ensures that employees remain vigilant against phishing attacks over the long term. However, the frequency question still lingers in our minds.
What is the recommended interval for phishing campaigns?
The recommended interval for phishing campaigns varies, depending on the organisation’s size, industry, cyber security maturity, and the evolving threat landscape. A general guideline is to regularly conduct phishing campaigns while balancing training effectiveness and employee well-being.
For this reason, security professionals have voiced some concerns. One challenge is balancing creating realistic phishing simulations and avoiding overwhelming employees. Simulations that are overly convincing or too frequent can lead to stress and reduced productivity, while overly benign or infrequent ones may leave employees underprepared for actual phishing threats. Overcoming resistance to change is also important, as some employees may view simulations as disruptive or unnecessary, potentially hindering cooperation and engagement. And since data privacy and compliance are paramount, security professionals must balance regular cyber security checks without compromising workflow and employee satisfaction and ensure compliance.
The sweet spot for us is normally one simulated phishing email per month – also backed up by sources like the Cyber Resilience Centre. This monthly cadence avoids inundating users with excessive simulations that could lead to frustration or complacency while cultivating a habit that becomes second nature.
While it might be tempting to conduct phishing simulations frequently, our findings with our platform indicate that sending more than three simulated phishing emails monthly can result in declining engagement and effectiveness. Therefore, the ideal learning outcomes are achieved with a moderate frequency of one to three monthly simulated phishing emails. This approach enables employees to hone their skills and awareness without feeling overwhelmed, ensuring that your organisation’s defences against real-world phishing threats remain robust and continually improving.
Getting the most from phishing simulations
As organisations recognise the pivotal role their employees play in fortifying their cyber defences, the importance of effective training and phishing simulation strategies becomes evident. Within this context, our Best Practices for Phishing Simulations report provides a set of best practices that have proven instrumental in safeguarding organisations against the perils of phishing attacks.
Best Practices
Phishing Simulations

Below are some of the main recommendations about phishing simulations included in this report:
- Instead of surprising, announcing: Communication before, during, and after the simulation is paramount for any learning-oriented phishing simulation. This involves IT, Help Desk, executive management, and if applicable, the Works Council and Human Resources department. Announcing the phishing simulation in advance is crucial for an insightful learning experience. When employees understand that the simulation contributes to a stronger security culture and safeguards the organisation against attacks, they become more engaged in the content and open to learning from it.
- Instead of testing, training: The practice of assigning blame can dampen employees’ willingness to learn and their motivation to engage. Conducting simulations anonymously, without collecting and analyzing individual behaviour data, is more effective and sustainable. It’s crucial to clarify in the simulation announcement that it’s not a test so that users don’t feel surveilled but rather empowered to complete the phishing simulation at their own pace and to the best of their abilities.
- Instead of outdated, real-life based: Simulated phishing attempts must accurately mirror the types of phishing emails employees are likely to encounter. Use up-to-date phishing simulations that will realistically represent the phishing situations employees may come across.
- Instead of daunting, educational: Enhance the phishing simulation with corresponding educational content, such as e-learning modules that provide guidance on secure everyday conduct and walk-throughs after clicking on a phishing simulation. If clicking on a simulated phishing email leads to no consequence or educational resources, recipients may be uncertain whether it’s part of the simulation or a real attack. IT Support may experience a higher volume of tickets, and the desired educational impact may be compromised.
Implementing these best practices is more than just a security measure. It is an investment in your organisation’s resilience against phishing threats and a commitment to nurturing a cyber security-conscious workforce.
What to do in between phishing campaigns
In the periods between phishing campaigns, organisations possess a unique chance to fortify their cyber security defences and cultivate a culture of heightened awareness among their staff. These intervals are not idle pauses but windows of opportunity to assess, educate, and empower. Here are some things you can do in between phishing campaigns to maximize their efficiency:

- Get insight: When you delve into the reports generated from phishing simulations, you gain a clearer picture of your organisation’s current security landscape. For instance, if the marketing department exhibits the highest click rate for a specific type of phishing email, you can tailor training to help them detect and counter that specific threat. It’s like customizing your defence playbook based on observed vulnerabilities and selecting modules to reinforce your team’s resilience.
- Targeted action: While fundamental training should cover standard prevention techniques like email source validation and cautious email scrutiny, addressing specific vulnerabilities among your employees is equally crucial. This calls for running distinct campaigns targeting identified weaknesses. Recurring phishing simulations should regularly complement training sessions to ensure tangible progress, keeping everyone sharp and up to date.
- Continuous awareness: Keeping your team well-informed about the latest phishing tactics, techniques, and procedures is pivotal. Leveraging MS Teams integrations like Sofie Rapid Awareness streamlines this process, ensuring your workforce is promptly notified about any important news and updates in the company.
- Share experiences: Establish internal forums where employees can openly discuss their personal experiences and insights about phishing attempts. Cultivate a culture where reporting suspicious emails or incidents is encouraged and embraced. In this environment, employees feel comfortable raising security concerns without apprehension of repercussions, enhancing the organisation’s cyber resilience.
The actions taken between phishing simulations significantly impact an organisation’‘s readiness to confront cyber threats. This is the time for organisations to refine their defences, draw wisdom from prior experiences, and ensure their workforce remains informed, engaged, and adept at repelling phishing attacks effectively.
How SoSafe can help you with your phishing campaigns
In our commitment to staying at the forefront of cyber security, we align our content with the newest trends in phishing. By continuously incorporating the latest insights and tactics employed by malicious actors, SoSafe’s phishing simulations provide real-time relevance and readiness for organisations to counter evolving threats effectively. They instill secure habits through implicit, incidental learning and contain context-based walkthroughs, created by learning specialists, that deliver personalized experiences across various channels to enhance digital self-defence skills. In fact, according to our 2023 Human Risk Review, combining gamified e-learning, phishing simulations, and contextual reporting tools increases phishing reporting rates by up to 80%, minimizing the threats to your organisation’s digital landscape.
Your interest in learning more about our phishing simulations or our holistic cyber security awareness platform is a step towards a stronger digital stance. Request a demo, and one of our security experts will guide you through how our platform can serve as a resource for your team, continually helping to mitigate cyber threats and enhance the overall security of your organisation.





















