
Human Risk Management
Human risk management has entered our lives at a time when organisations worldwide are facing an alarming increase in cybercrime. Of course, this is not a coincidence.
Attacks are becoming more sophisticated not only due to the rise of AI-powered tools but also due to the increasingly creative ways in which cybercriminals are targeting the human element with social engineering to bypass advanced technological defences. In this landscape, Verizon’s Data Breach Investigations Report estimated that up to 74% of breaches involved a human element in 2023, and the truth is: This is just the beginning of what’s to come. That’s why Forrester predicts that this percentage will even increase to 90% in 2024.

These figures underscore a critical gap. In the past, companies focused on improving their technical security measures but often neglected or paid insufficient attention to their employees’ roles. While strong technical security measures are essential, they alone are not enough to protect against the sophisticated tactics of modern cybercriminals who circumvent technical protection measures by taking advantage of the human factor.

Security awareness and training solutions (SA&Ts) came about to try to solve this problem, and compliance frameworks embraced them. However, they have been too focused on quickly transmitting information, not changing behaviour, and the current threat landscape shows us how checking the compliance box doesn’t make the cut anymore.
That’s why analysts and security leaders have raised their hands and asked for a more holistic approach to security that identifies, quantifies, actively manages, and ultimately reduces their human risk. They want an approach that prioritises the outcomes and drivers of behaviour to foster a security culture where secure behaviour becomes second nature. And this approach is what we now call Human Risk Management.
But before we go any further in explaining what human risk management really involves, let’s start with the basics and understand why we need to go beyond SA&T.
Let’s start with the basics: What is security awareness and training, and why doesn’t it serve us anymore?
Security awareness and training (SA&T) is the name the industry has used to refer to the programmes and initiatives set up within organisations to educate employees about the various aspects of information security.
It’s hard to pinpoint exactly when this category was first mentioned or formalized, but the concept really began to gain traction in the early 2000s – the era of the rise in Internet usage and the subsequent increase in cyberattacks. One example of an official source using this naming is the Special Publication 800-50, “Building an Information Technology Security Awareness and Training Program,” published by the National Institute of Standards and Technology (NIST) in 2003. This document provided guidelines for establishing effective IT SA&T programmes, marking a formal acknowledgment of the importance of such initiatives in cyber security.
In the beginning, however, the effectiveness of those early training programmes was very limited. They often lacked the engaging and interactive elements necessary to maintain attention and foster long-term behaviour change. And even as more modern approaches began to include phishing simulations and some form of advanced nudging, the reality is that the industry was still a bit dinosauric even at the beginning of 2020, with large but generic video libraries of one-size-fits-all content and a strong focus on compliance only. In fact, Jinan Budge, VP, Principal Analyst at Forrester, published an article in November 2021 about exactly this:

In 2022, there already seemed to be more awareness around the fact that companies needed to move beyond meeting compliance requirements and focus on positively influencing employee security behaviour, instilling a security culture, and managing human risk. Industry experts at Gartner also weighed in on how security leaders should reorient their awareness programmes to focus on human risk management outcomes, not just regulatory and audit compliance. But is the era of training people to check boxes on outdated and confusing compliance requirements really coming to an end?
The answer is: not yet. A recent NIST study found that 55% of security executives still believe that compliance is the most important indicator of SA&T success. However, even though they viewed compliance as an important indicator of success, there was also a clear recognition that it may not reflect actual effectiveness in terms of behavioural and attitude change. But when asked about how they track success, the survey revealed that organisations primarily rely on training completion rates (84%) and phishing simulation click rates (72%) to measure the effectiveness of their security awareness programmes.

And this shows that there’s still a lot of work to be done to move all global organisations into a place where we look at security holistically and really go beyond compliance. Of course, compliance is not inherently a bad thing. It’s necessary. The problem is when it becomes the primary reason we do it. SA&T should be a method, not an outcome. By truly moving toward a more holistic approach to human risk management and developing tailored strategies that effectively engage individuals – with clear metrics to measure behavioural change and risk reduction – we can strive to transform SA&T and increase our organisational resilience and adaptability.
And that is what human risk management is all about: It’s not yet the reality where we live entirely, but the attempt by an entire industry to ensure that we all move in that direction as quickly as possible to be better protected.
But what is human risk exactly?
We have mentioned human risk quite a few times in this guide already, as it’s a key component of the human risk management approach. But do we all understand what human risk really means?
To fully grasp the concept, we must look at two key terms: vulnerability and threat. In the context of human risk, vulnerability refers to the susceptibility of individuals to engage in behaviour that could lead to security incidents. This could be due to a lack of awareness, technical limitations, poor choices, or simply human error. For example, an employee might be vulnerable to phishing scams due to a lack of understanding of how they operate. On the other hand, threat refers to a potential cause of an unwanted incident, which may result in harm to a system or organisation. In terms of human risk, threats could include social engineering tactics aimed at exploiting individuals, such as phishing, spear-phishing, or pretexting. But let’s see another tangible example before moving forward:

It’s between these two concepts that human risk lives, as it measures how vulnerable an organisation is to loss, damage, or any other undesirable event caused by a human vulnerability being exploited by a threat. In other words:

A new market category: What is human risk management?
And now that we have defined SA&T, vulnerability, threat, and human risk, we are better prepared to fully understand what human risk management is. You might have also heard it referred to as “Security behaviour and culture programmes” (SBCPs) or “Human detection and response,” but the exact term “human risk management” as a new industry category has been coined by Forrester in an article, “The Future Is Now: Introducing Human Risk Management,” and has been defined as follows:

This definition implies the same message we discussed above: Basic awareness efforts alone are insufficient and cannot achieve true risk reduction. While traditional awareness programmes focus on creating awareness and imparting knowledge – educating individuals about potential threats and instructing them on response strategies – this approach often falls short in today’s dynamic environment. The evolving landscape requires a shift to holistic human risk management that prioritises the outcomes and drivers of behaviour. This means understanding behaviours, their root causes, and their manifestations. It’s not just about knowledge transfer. It’s about fostering a security culture where secure behaviour becomes second nature, integrating specific behavioural science methodologies, and leveraging technology to support these efforts.
In other words, Human Risk Management (HRM) is an evidence-based method for training people and taking action based on their risk profile. This method relies on empirical data and research to truly understand where people-related vulnerabilities exist. It uses data from past security incidents, monitors user activity on the network, and identifies recurring behaviours that escalate risk, among other strategies.
But it’s best to go through each of the four elements in Forrester’s definition to fully understand all the dimensions of this category.
The first step: Detecting and measuring human security behaviours and quantifying the human risk
Traditional security awareness training solutions have long focused on limited activity metrics to measure risk, often overlooking the critical need to evaluate how well such training reduces vulnerability to actual cyber threats. While tracking completion rates and test scores provides insight into engagement and knowledge acquisition, it does not necessarily correlate with behavioural change or reduced risk exposure. And that’s why HRM seeks to go beyond simple activity metrics to incorporate more nuanced and meaningful risk metrics that measure the training effectiveness in mitigating real-world cyber security threats.

At SoSafe, for example, our Human Risk Score (HRS) is designed to exactly quantify the human-related cyber security risks within an organisation by detecting human security behaviours and the risks they pose. By detecting the highest risk areas, which can include different groups inside your organisation, CISOs can then respond with interventions focused on mitigating those risks. For example, by detecting different dangerous security behaviours in specific departments, such as inputting personally identifiable information into generative AI, sharing sensitive data over unsecured networks, or using weak or repeated passwords, targeted interventions can be developed to accelerate behavioural change.

SoSafe’s data dashboard
And now that we have mentioned interventions, we can move to the second part of the definition that tackles exactly that.
Initiating policy and training interventions based on the human risk
Quantifying risk is just one piece of the puzzle, which becomes more complete when we then design interventions that directly address the identified vulnerabilities and threats to ensure proactive security measures. For example, if the data dashboard shows that there is a specific knowledge gap and that a certain group is engaging in behaviours that increase the organisation’s risk, CISOs can tailor the learning experience with active interventions, such as a nudge with a conversational bot to these employees. Phishing simulations can also be adjusted in difficulty and psychological vectors based on risk and specific behaviours. At SoSafe, for example, we offer the ability to target high-risk user groups like finance, HR, security, senior management, and engineering with personalized phishing simulations. But that’s just the tip of the iceberg. There are as many interventions as there are potential risks, and the most efficient way to tackle this is to make sure we prioritise interventions based on risk. This screenshot shows an example of four different interventions that can be registered and triggered through the SoSafe platform.

SoSafe’s interventions hub
Leveraging integrations for deeper behavioural insights
There is something very transformative about taking a holistic view of security and trying to gain as much insight as possible into the secure behaviour of our teams. Gathering data from other sources is another step in that process – making sure that we use all the technologies available to us to identify and quantify the risks for any organisation. This effort to connect and utilise diverse security tools gave rise to a concept that Gartner has termed “cyber security mesh” or “cyber security mesh architecture (CSMA).”
This integrative approach represents a pivotal shift toward a more collabourative and interconnected security framework by emphasizing the power of integration across a distributed network of security tools and controls. By centralizing the management of data and control mechanisms, CSMA enables these tools to work together seamlessly. The result is a robust security infrastructure that can provide more sophisticated detection capabilities; streamline threat response; ensure consistent management of policies, postures, and playbooks; and implement more adaptive, granular access controls.
Human Risk Management embraces this philosophy and recommends that any HRM platform should integrate with the rest of your technology stack to provide a more holistic view of the security culture within an organisation and to provide the necessary interventions to reduce human risk. For example, following this principle, the SoSafe platform integrates with:
- Microsoft 365 for collabouration and data loss prevention behaviours (e.g., sharing personal information) as well as responding to real phishing simulations;
- Microsoft Entra for identity events (e.g., travel, impersonation) and authentication behaviours (e.g., MFA enabled, password spray, etc.);
- and Microsoft Defender for endpoint protection behaviours (e.g., antivirus), among others.
Educating and enabling the workforce to protect themselves and their organisation against cyberattacks
There is simply no other way to do it. Human Risk Management emphasizes how teams are trained and empowered to protect themselves. This is something we have been advocating for for a long time. And, one of the biggest levers you can use to ensure that this training is effective and that you provide ongoing security culture management is to use the principles of psychology and behavioural science in every learning experience you provide to your employees. The benefits of this approach are plentiful. The risks of not doing it are too high.
One of the main reasons for moving to this approach is that traditional methods of cyber security training, such as a standardized training programme or fixed curriculum, are no longer sufficient. They often lead to a rapid decline in engagement and a significant decrease in knowledge retention, as shown by Dr. Ebbinghaus’ forgetting curve. The graph shows how learners forget 90% of what they learn within the first seven days, and this rate of information loss increases when learners interrupt their learning routine and frequency.
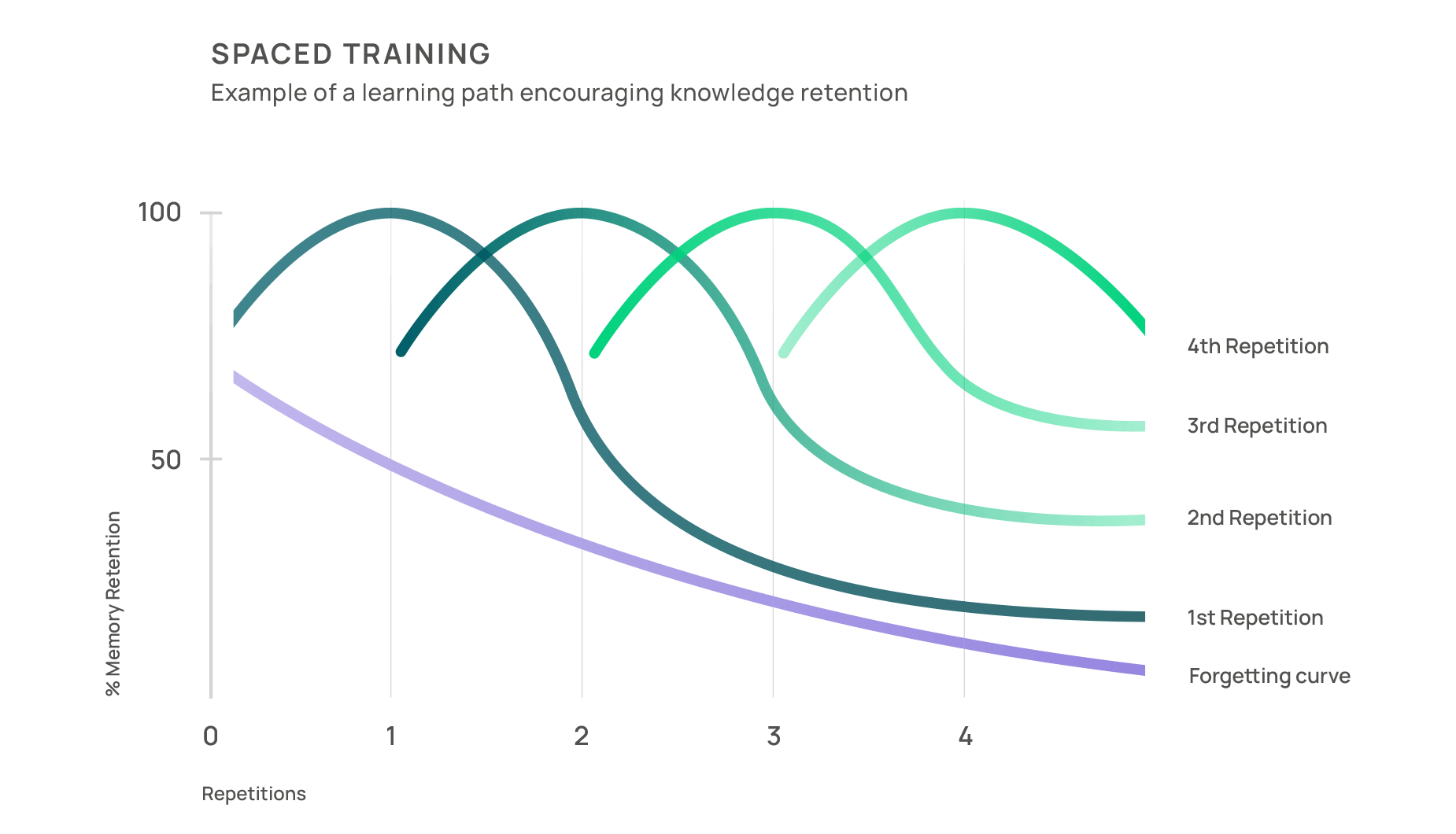
However, strategic approaches exist that can enhance information recall and reinforce training efforts. Spaced training, consistently delivered in nudges via diverse channels like email and collabouration tools, allows learners to revisit and reinforce what they’ve learned. One example is our conversational bot, which offers multi-channel nudges and conversational culture building.
Incidental learning is another element in behavioural-based security training that shares similarities with nudging as it supports learning in real-life scenarios. In a world saturated with information and where time is often scarce, delivering bite-sized learning modules at critical moments is key. A learning page appearing after clicking on a phishing simulation email is a perfect example. These brief five-minute snippets of security awareness training seamlessly integrate into a busy workday, facilitating continuous learning without overwhelming the learner. But there’s more to incidental learning than that. Research data shows that people learn more quickly from mistakes than from theory, and phishing simulations can thus become a safe space for people to make mistakes and learn from them.
Gamification: Another powerful tool in any behavioural science toolkit
By transforming traditional sessions into interactive experiences, learning becomes not only informative but also fun and engaging. The flow theory, developed by Csikszentmihalyi, supports this claim as it explains that people have a state of heightened concentration and immersion in activities that are both challenging and enjoyable. Gamification elements that match a learner’s skill level can help induce this state of flow, making learning more enjoyable and effective. Moreover, according to a Talent LMS survey, over 80% of respondents felt that gamification improved their learning and fostered a stronger connection to the content.
In essence, to cultivate a culture of cyber security, it’s essential to transform learning into an experience that’s both educational and enjoyable, ensuring that motivation and security awareness grow hand in hand. Our own product data supports this: Immersive storytelling and deep gamification increase user engagement to 54%.

Personalized learning to accelerate time to awareness and simplify the user experience
To create a secure culture, personalized training programmes that address the specific risks and roles within an organisation are also essential. For example, managers who frequently use business cell phones will need training sessions that educate them on the risks of mobile threats and how to deal with them properly. The IT department, on the other hand, will need specific security knowledge that is irrelevant for other end users.
Tailoring training content to everyone’s unique challenges and security awareness will not only make learning more effective but also more engaging. According to research conducted by Towards Maturity, 77% of learners seek content relevant to their work. Therefore, this behaviour-based approach focuses on the employees, addresses their unique challenges, and delivers content specific to their roles, profiles, and awareness levels.
Positive reinforcement is the only way to really empower employees
Traditional training approaches and views of the human role in security have also focused on the message that humans are the weakest link in an organisation’s cyber security. As a result, there’s a long tradition of victim blaming and fear. However, psychology tells us that this can lead to learned helplessness, a concept developed by Seligman. According to this theory, people who believe that they are victims of their circumstances and, therefore, have no control over their situation become very passive and depressed. They don’t act and become part of the solution because they don’t even believe it’s possible and end up living in fear. At SoSafe, we believe in empowering employees through positive reinforcement in the form of personalized, relevant, and interactive training, regular feedback loops, and recognition.
By providing constructive, engaging, and situation-specific training, organisations can cultivate a proactive security culture where individuals feel responsible and equipped to act against threats. This empowerment strategy is built on the understanding that people are more likely to take positive action when they feel competent and valued. Through gamified learning experiences and real-life simulations, employees not only acquire the necessary cyber security skills but also build confidence in their ability to contribute to the organisation’s safety. Regular feedback sessions serve to reinforce their progress, acknowledge their contributions, and guide them through areas needing improvement, fostering a sense of achievement and belonging.
Additionally, by promoting an open and supportive environment, we encourage employees to share their experiences and learn from each other. We believe that by shifting the narrative from blame to empowerment, we can transform the human element from a liability into a powerful ally in the fight against cyber threats.
Creating more security champions to accelerate digital proficiency
Bandura also explained in his Social Learning Theory that people learn through observation, imitation, and modeling of other individuals. In cyber security contexts, positive models of conduct (e.g., colleagues demonstrating good security practices) enhance learning and the adoption of secure behaviours. At SoSafe, we believe in the strength of this theory, and that’s why, through our analytics dashboard, we pinpoint standout performers in your organisation so that you can identify those security champions, foster an increased collabourative defence, and make security everyone’s responsibility.

Creating security champions through SoSafe’s dashboard
Security culture as a key ingredient to effectively manage human risk
All this boils down to one thing: The ultimate goal is to build a strong security culture to effectively manage human risk. Secure habits protect your organisation, such as locking the screen when leaving a desk, reporting security incidents to IT, and checking emails for suspicious content. But fostering these daily digital habits strongly depends on the culture you have been able to create. How can we then define what a security culture is?

At SoSafe, we developed the Behavioral Security Model to go beyond traditional security approaches by placing employees at the centre of the cyber security strategy. This approach recognises that a sustainable security culture can only be achieved when employees are understood not only as potential risks or the weakest element but rather as key actors in their organisation’s defence.
The Behavioral Security Model is based on four dimensions: knowledge, context, motivation, and behaviour. These dimensions are not viewed as separate entities but rather as an interwoven system that encourages employees to be proactive. The holistic approach of this model aims to strengthen every aspect of how employees interact with cyber security, and the interplay of these four dimensions creates a strong line of defence that promotes both individual and collective security efforts.

Here, we summarize the four dimensions, interweaving each with the psychological theories and concepts mentioned above. Combining these four creates a strong security culture with a focus on the human risk management approach. However, if you want to read more about the model specifically, read our blog post, “How to create a security culture: The Behavioral Security Model”:
- Knowledge involves understanding cyber security threats and best practices through a sound training programme with continuous, contextual knowledge delivery.
- Context ties security actions to the employee’s daily tasks, emphasizing the need to receive knowledge that is personalized and relevant to their work.
- Motivation drives employees to adopt secure behaviours through positive reinforcement practices, such as rewards or recognition.
- Behavior focuses on integrating these security actions into everyday routines, creating secure habits in the organisation.
How can SoSafe help you manage and reduce your human risk?
SoSafe is the leading human risk management platform built on the foundation of psychology and human-centric design, making secure behaviour second nature. We believe people want to do the right thing but need to be empowered to succeed. In times of an escalating and highly professionalized AI-powered threat landscape, that’s more important than ever. That’s why we aim to create security cultures that strengthen digital self-defence, involving people to mitigate human risks.
But to create such a culture, it is crucial that employees have relevant knowledge, are trained in the right context, are motivated to get involved, and adopt secure behaviour as a daily routine. SoSafe supports organisations in the practical implementation of the four key dimensions of the Behavioral Security Model, whereby cyber security e-learning sharpens the security skills of everyone through personalized, gamified e-learning modules. Our real-life personalized phishing simulations also include detailed walkthroughs designed by learning experts, making the training more effective. When combined with ongoing learning, these simulations help employees develop secure habits in their daily work. As these habits become routine, the risk to the organisation lowers, and the ability to quickly respond to incidents increases.
With tools like the Phishing Report Button, SoSafe enables employees to effectively put their knowledge into practice, actively contributing to the protection of the entire organisation. But there’s more: Our conversational bot, Sofie, enables you to rapidly connect with your employees on collabouration tools. Enable rapid micro-learning to address emerging threats, grow the culture by having 24/7 access to the first line of security support, and transform users into your strongest defence.
On top of that, our Risk Scoring and Culture Automation dashboard helps you ingest first- and third-party data, track activity and risk metrics, assess human risk, identify vulnerabilities, and make data-driven decisions, all in one place.

This is our only chance to alleviate the burnout crisis facing security teams today
As we mentioned earlier, Human Risk Management has entered our lives at a time when organisations worldwide are facing an alarming increase in cybercrime. But we’ll add more: It has come at a time when security teams are under unprecedented pressure.

A key factor exacerbating this pressure is the shortage of skilled labour in the industry. According to ISC2’s latest report, there are 3.9 million unfilled cyber security positions worldwide. But that’s not all. According to a study by ISACA, 59% of organisations have a shortage of cyber security staff, dramatically increasing the workload for existing teams and often driving security officers to the brink of burnout or even resignation.
A survey of over a thousand security team members in the US and Europe confirms this: 66% of respondents suffer from significant work stress, 51% have been prescribed medication for mental health, and 19% consume more than three alcoholic drinks a day as a coping mechanism. But this condition goes far beyond a personal burden. It can also cause teams to overlook important details, affecting their ability to respond effectively to threats and significantly increasing the risk of security breaches in their organisations. This risk is compounded by the fact that cybercriminals are constantly evolving their techniques and becoming more sophisticated in their attacks, as we have already seen in the past sections.

In this dynamic and challenging environment, it is essential that organisations invest in their security teams to promote the well-being of their employees. And using the right Human Risk Management platform can really make a difference by helping them identify and manage risks, prioritise interventions based on risk, and offer sustainable and effective training solutions that accelerate time to awareness.
We cannot deny the reality: Security teams are overwhelmed and need simple and effective solutions to mitigate human risks. That’s why at SoSafe, our main goal is to reduce the burden of security leaders and teams by enhancing efficiency, simplifying where others complicate.


















