
Pretexting
What is pretexting in cyber security?
Pretexting is a deceptive social engineering technique malicious actors use to trick individuals into revealing sensitive information by fabricating false believable scenarios to gain the target’s trust and then coaxing them into sharing confidential data or performing actions that the attacker can later exploit. To do this, attackers usually assume a false identity, impersonating someone the victim trusts.
Pretexting is one of the most common social engineering techniques. According to a 2023 report by Verizon, it comprises more than 50% of social engineering incidents, which shows how attackers continue to rely heavily on deception and manipulation, capitalizing on the human factor. And they do it because it works: In August 2023, software firm Retool suffered a cyber attack initiated by an SMS phishing scheme where the attackers posed as members of the IT team. They sent messages to employees instructing them to click on a link to address a payroll-related issue until one of them fell for this pretext. The hackers could then access the internal systems, take over 27 customer accounts, and steal close to $15 million worth of cryptocurrency.
Pretexting emerges as a very potent social engineering tactic, urging us to dust off our lenses and adopt a robust stance to ward off its cunning exploits. This article arms you with insights to recognise and the tools to shield against this lurking menace.

The mechanics of pretexting: How does it work?
At its core, pretexting is about trickery and manipulation to gain your trust and make you believe they have a legitimate reason for requesting sensitive information.
Pretexting attacks require extensive preparation by the perpetrator. Before the attack, the cybercriminal needs to research the victim to learn more about them. This research may involve gathering information from publicly available sources, such as the company’s website, social media profiles, and online directories. The attacker may also try to learn about the target’s recent activities or upcoming events within the organisation to seem more convincing. Most of the time, the level of thoroughness of this previous research is what sets up the attack for success or failure. This initial research serves two purposes: deciding which person of trust they will impersonate and elabourating on the personalized pretext they will use to trick the victim into trusting them.
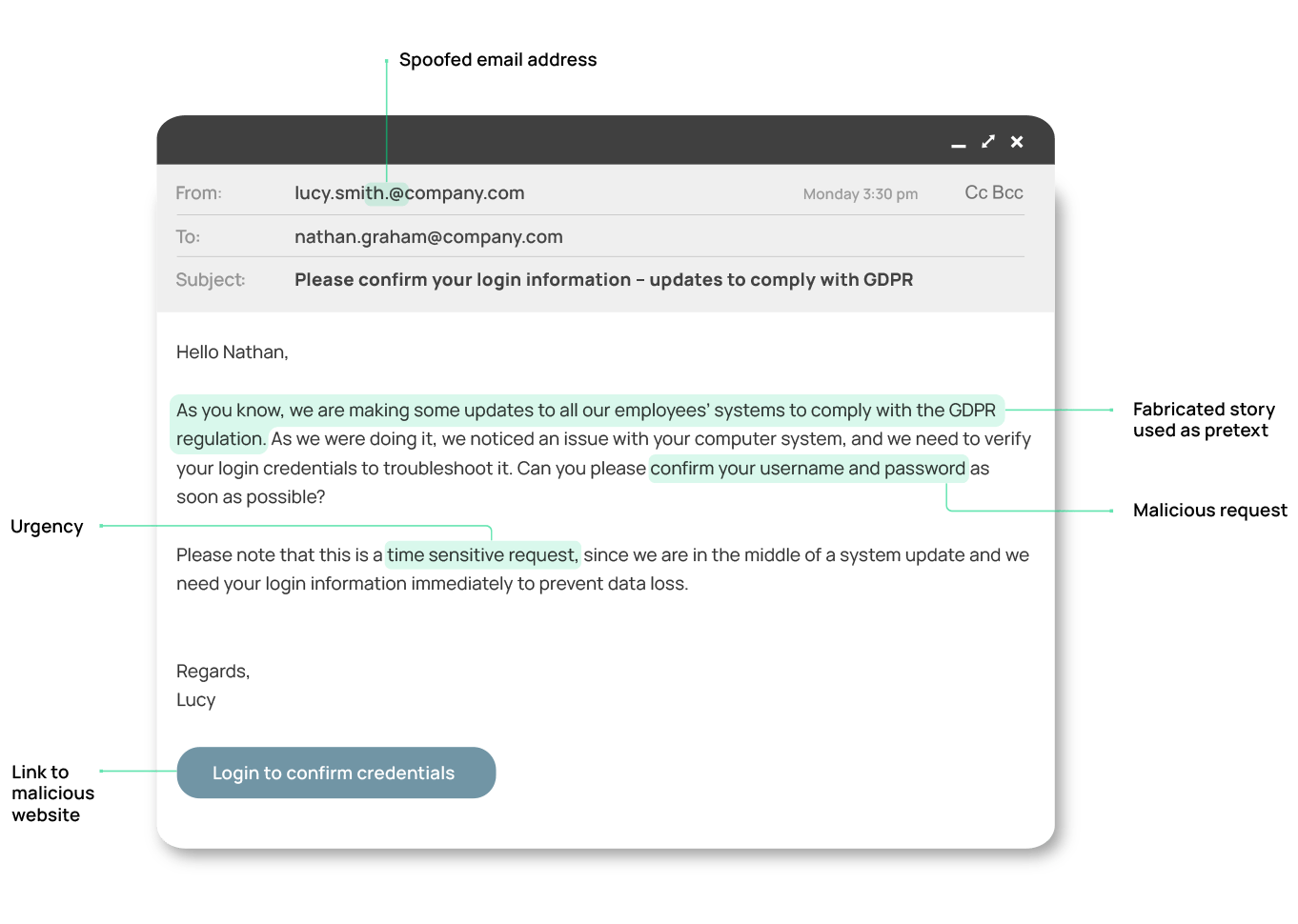
The attack begins when the hacker contacts the target using information obtained from their research. They may pose as an IT support technician and use a fake employee ID, email address, or even spoof the caller ID to appear legitimate. And they may communicate using several channels, such as email, SMS, or calls within the same attack.
The attacker will then assume a fabricated role like an IT colleague to create a plausible scenario using the information they learned in their previous research. They often employ elements of urgency, authority, or scarcity to add legitimacy to their request, making the target more likely to comply. Once the target believes the pretext, they may provide the attacker with sensitive information like usernames, passwords, or other credentials.
Pretexting vs phishing: What are the differences?
Although phishing and pretexting may be confused due to their close connection, they are different concepts in cyber security. Phishing is a general term for various attacks that can be executed through different channels like email, voice (vishing), or text messages (smishing), sometimes involving highly targeted methods like spear phishing. These attacks share a common goal: to deceive individuals into actions like downloading an attachment or clicking a link, thereby exposing sensitive information. They employ social engineering tactics, including baiting, tailgating, and pretexting. Specifically, pretexting involves creating a credible false scenario to build the victim’s trust, often enhancing the effectiveness of phishing attacks by making them seem more legitimate.
In essence, phishing represents the act of launching the attack, while pretexting is one of the social engineering methods that can be used in phishing attacks. There are many ways to deceive victims in pretexting attacks.
Common methods used in pretexting attacks
Pretexting attacks are cleverly crafted acts of manipulation, and they involve various common methods that exploit human psychology and trust.
In the preparatory phase of the attack, where they collect information about the victim, they can use the following methods:
- Dumpster diving: This technique refers to the practice of searching through a target’s trash or recycling bins to find information that can be used in a cyberattack. This could include documents with passwords, network configurations, or other sensitive data. It’s a low-tech method used to gather useful information for launching more technical attacks.
- Whois lookups within online research: Whois lookup is a service that tells you who owns a particular domain name. Hackers can use this to find out who owns a website and, sometimes, get contact information or learn about other domains owned by the same person or organisation. This can be a starting point to gather more information for their malicious plans.
- Prepare answers to questions: Attackers anticipate questions or concerns the target might have and prepare answers in advance. This ensures they can respond confidently and maintain the illusion of authenticity during the interaction.
- Test the pretext: Some attackers may conduct trial runs of their pretext on less-critical or lower-profile targets to refine their approach before targeting the main victim.
Armed with this gathered knowledge, attackers start to craft a persona that appears familiar and trustworthy. To do so, they may use one or more of the following:
- Impersonating authorities: Hackers might impersonate police officers, government officials, or company executives to create a sense of urgency and authority, which may lead individuals to comply with their requests without question.
- Creating fake identities: Attackers may create fake identities complete with believable backstories, job titles, and contact information. They might create fake LinkedIn profiles, business cards, or even websites to support their fabricated identities.
- Spoofing: Spoofing involves disguising a communication or data source to appear as trusted or originating from a different source. Cybercriminals use many types of spoofing to deceive and gain unauthorized access. These include, but are not limited to, IP spoofing, where hackers mask their IP address to mislead systems; domain spoofing, which involves creating fake websites or emails to trick users; and caller ID spoofing, disguising phone numbers to appear as a trusted contact.
- Using technical tools: In some pretexting attacks, hackers may use advanced technical tools to enhance their impersonation and make their deception more convincing. Hackers can use voice-changing technology, such as voice cloning apps, to impersonate someone over the phone. They might also use software to create realistic-looking documents or emails from reputable sources. Additionally, tools that create deepfakes can replace a person’s likeness in videos, making the pretext more convincing to the victim.
- Document forgery: Attackers create or manipulate documents to impersonate legitimate individuals or entities. This method relies on fraudulent documents like agreements, invoices, or fake emails to establish credibility and deceive targets into divulging sensitive information or taking specific actions.
Pretexting is often just the first step in a more comprehensive attack. Attackers may be planning to use the information or access gained through pretexting for further exploitation and cause harm to both individuals and organisations. Their success and effect have been exposed in real-life scenarios.
Real-life pretexting examples
With pretexting attacks growing exponentially in the past few years, we have seen how they affected individuals and companies of all sizes. Through the following real-life examples, we explore the intricacies of these attacks, shedding light on the methods and tactics employed by attackers in their quest to manipulate individuals and organisations for personal gain.
Uber’s critical software exposed by hackers using pretexting
This case is an example of how cybercriminals used multiple channels in one attack to circumvent Uber’s security. The attackers repeatedly triggered push notifications in an authentication app. They further deceived the victim by sending a WhatsApp message posing as Uber’s IT department, instructing the employee to confirm the legitimacy of the login attempt. This strategy granted the attacker access to a VPN, subsequently providing access to Uber’s corporate intranet and enabling them to scan the network for sensitive files and applications otherwise inaccessible from outside the VPN.
The consequences of this breach were significant, as the hacker obtained an admin password granting access to Thycotic, a privileged access management (PAM) tool controlling access to critical software used by the company. As a result, they extracted secrets for all services, exposing Uber to substantial risk.
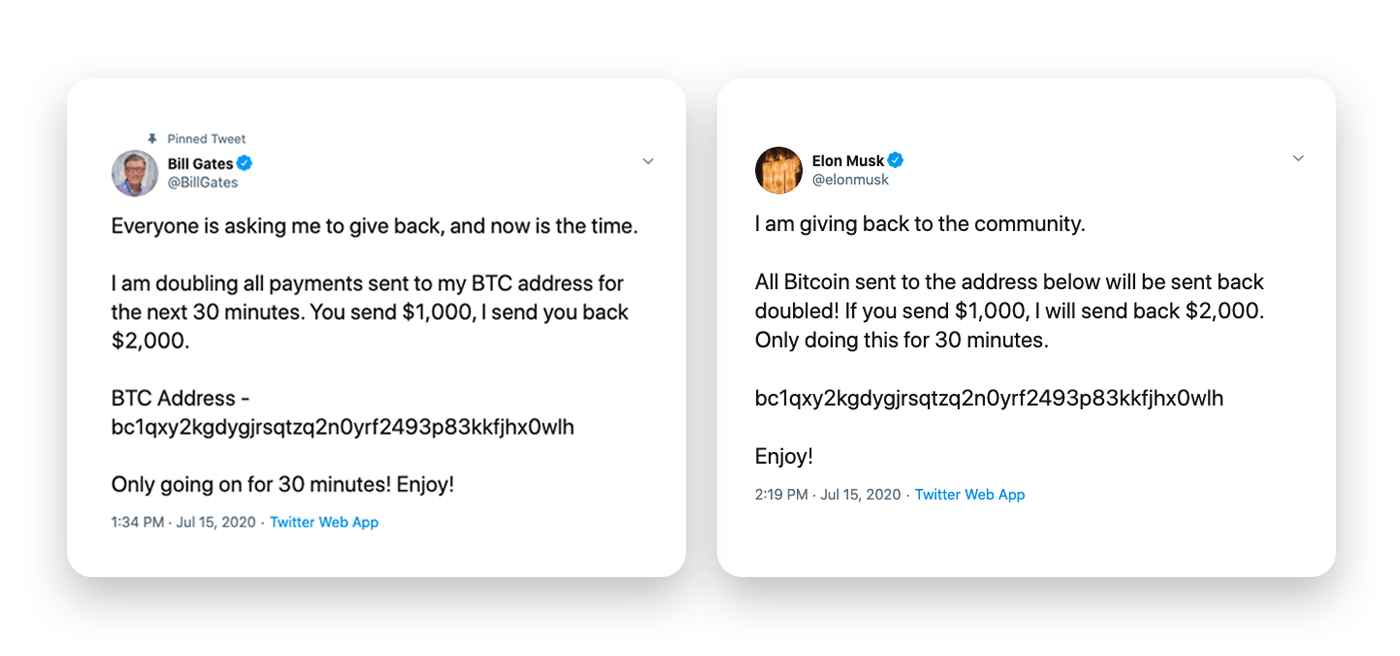
Twitter Bitcoin scam of high-profile accounts
In 2020, Twitter suffered a significant security breach that targeted high-profile accounts, including Elon Musk, Joe Biden, Barack Obama, and the corporate account of Apple, all trusted figures in the public’s eye. The scammers posted tweets from these accounts, requesting Bitcoin payments to specific accounts and promising to double their investment, but only for a specific amount of time or until a certain sum was met.
This scam had everything to be successful: Messages came from trusted and known senders, and there was a sense of urgency created in victims that rushed them to make a hasty decision. However, while this attack amassed over $121,000 from over 400 payments, the scammers struggled to capitalize on it fully, mainly because of the rapid response from Twitter and the vigilance of the cryptocurrency community regarding scams and fraudulent schemes.
Global COVID-19 scams
The pandemic chaos and worrisome environment of 2020 and 2021 was the breeding ground for pretexting attacks. During this time, hackers became creative by using the pandemic as the main pretext to lure their victims. For example, many users reported receiving fake emails, calls, or text messages requiring them to fill out a vaccine survey in exchange for a “free reward” where they had to pay shipping fees. The survey was phony, and of course, the attackers received the supposed shipping fees individuals paid for.
With the stimulus checks in the US aimed at reducing the setbacks from the pandemic, attackers seized another opportunity to exploit unsuspecting individuals. They sent emails from seemingly reliable sources promising expedited check delivery, urging recipients to register their email addresses and personal details. Once they registered, cybercriminals harvested the victims’ information and often stole individuals’ payments.
According to the Federal Trade Commission’s annual Consumer Sentinel Network report, the successful attacks resulted in a $86 million loss for individuals and organisations in 2020 alone. The spike was so drastic that the FBI issued a warning, cautioning the public about the most common methods scammers use to take advantage of individuals.
Pretexting done by companies to employees
Although not the most usual pretexting use, sometimes it’s not professional hackers who target employees with pretexting but their own companies. Computer hardware company Hewlett-Packard (HP) admitted to using pretexting tactics to investigate its board members after leaks about its strategic plans surfaced in a news article. The company that HP hired to carry out the investigation called the telecom company AT&T using pretexts and impersonated several board members to access their cell phone records.
This scandal ended in significant legal fees for HP, who agreed to pay the state of California $14.5 million to settle state civil claims.
These pretexting incidents serve as eye-opening reminders of the ever-evolving landscape of cyber threats. As organisations and individuals navigate this intricate digital realm, early detection and prevention become paramount.
Seeing through the scam: Identifying pretexting attempts
The danger of pretexting lies in how convincing it can be. Attackers are often well-prepared, having extensively researched their targets and the organisations they are impersonating and combining it with a realistic scenario to make their narrative more believable. They may use official-sounding terminology, provide fake credentials, or even have background noise in phone calls to appear genuine. Here are some of the tell-tale signs of a pretexting attack:
- Urgency: These attempts frequently create a sense of urgency to rush their targets into making decisions without thinking. Take a step back if the requestor pushes you to act quickly, especially when dealing with sensitive information or transactions. Genuine requests rarely require immediate, hasty actions.
- False familiarity: Be cautious of anyone who seems overly familiar and ensure they provide a legitimate reason for having access to personal information or details about your life or organisation. If the person making the request appears to know more than they should or they reference personal details you haven’t shared with them, be suspicious.
- Inconsistent details: Pay close attention to the information provided by the requester and be alert to any contradictions or discrepancies. When you notice such irregularities, proceed with caution and consider verifying the authenticity of the request.
- Excuses to avoid ongoing communication: If the person making the request becomes defensive, evasive, or provides reasons for why you shouldn’t contact others or verify their identity, it can be a sign of a pretexting attempt. Genuine requests for information or actions should not discourage you from seeking confirmation or additional information.
- Domain spoofing: If you receive an email from what appears to be a well-known organisation or website but the domain in the email address or URL seems slightly altered or misspelled, it could be a pretexting attempt.
- Requests for verification codes: Pretexting attackers may request verification codes, often claiming it’s for security purposes or to confirm your identity. Be cautious if you receive such requests, especially through email, phone calls, or messages. Legitimate organisations don’t usually request verification codes without a valid reason or without you requesting it first.
- Invoking compliance or legal obligations: Attackers may use compliance or legal language to pressure you into complying with their requests, making you believe you have a legal obligation. Legitimate legal or compliance matters are typically handled through formal channels, so be careful of any emails or calls pressuring you into taking immediate action, especially when sensitive information is involved.
- Requesting discretion: If a message says things like “Keep this between us,” “Don’t share this information with others,” or make similar isolating or secrecy requirements, it’s a red flag. It may be an attacker attempting to control the situation and prevent you from seeking advice or verification from trusted sources to discover the deception.
Proactive measures against pretexting
Preventing pretexting attacks often requires a combination of vigilance, education, and security best practices. Here are the best ways to protect yourself, your employees, and your organisation from pretexting attacks:
For individuals and employees:
- Guard your personal and financial information: Never share your passwords, account numbers, or other sensitive information online, especially in emails or over the phone. Legitimate institutions will never request such data through these channels. If you receive a request for sensitive information and doubt its authenticity, hang up or close the email and contact the institution directly using trusted contact information to verify the request’s legitimacy.
- Exercise caution with unknown contacts: Be cautious when communicating with individuals you don’t know, especially if they request sensitive information. If you’re unsure about the legitimacy of the person contacting you, use established and reliable communication channels to verify their identity.
- Strengthen your passwords: Avoid using the same password across multiple websites and create strong and unique passwords. Varying your passwords also helps minimize the impact of a potential breach. If one account is compromised, the others remain secure.
- Secure your personal information: Protect digital data by using encryption and secure storage practices. Keep physical documents containing sensitive information secure and dispose of them properly when no longer needed.
- Report suspicious activity: If you suspect that you have been the target of a pretexting attack, take immediate action. Report the incident to the appropriate authorities and inform relevant online services that may have been involved in the attack, such as your email provider. Prompt reporting can help prevent further harm and aid in apprehending perpetrators.
For companies:
- Encourage reporting: Promote a culture of reporting within your organisation. Encourage employees to report all phishing attempts or suspicious activities promptly. Swift reporting can help security teams take action before an attack escalates.
- Implement multi-factor authentication: Using multi-factor authentication (MFA) adds an extra layer of security by requiring multiple forms of authentication for access. Even if an attacker obtains one form of authentication, such as a password, they would need the second form, such as a phone-based token, to complete the login.
- Verify external parties: Vigilance should extend beyond your internal employees to anyone interacting with your systems. When external parties require access to sensitive information, ensure they adhere to your organisation’s cyber security protocols.
- Regular software patching and updates: Maintain the security of corporate devices and machines by keeping all software continuously patched and updated. Outdated software can present vulnerabilities that attackers may exploit.
- Adapt cyber security policies: Regularly update your cyber security policy to account for new types of social engineering attacks, including pretexting. This ensures that your defences remain robust and up to date.
- Refine incident response plans: To minimize the impact of any successful pretexting attack or alternate tactics, update your incident response plans. Having well-defined procedures in place for identifying, containing, and mitigating the effects of an attack is essential in maintaining business continuity and security.
- Employee training and awareness: Regular and continuous training on the latest cyber security threats, including pretexting, will keep employees informed about identifying and responding to suspicious activities. This education is crucial in building a vigilant workforce that can recognise and thwart pretexting attempts.
Staying vigilant: How to protect your organisation from pretexting attacks
The stories of real-life pretexting attacks underscore the cunning tactics employed by adversaries who exploit human nature to achieve their malicious ends. Sophisticated pretexting attacks are very convincing, so it’s paramount for individuals and organisations to maintain a constant state of alertness.
By arming your employees with knowledge, awareness, and a well-fortified security infrastructure, you can build a resilient defence that stands firm against even the most artful of deceivers. SoSafe’s Micro-learning modules simplify cyber security training by making it accessible and enjoyable for employees. By employing gamification techniques and psychology-driven learning, it empowers employees to recognise and neutralize pretexting and social engineering attempts.
Another important aspect of continuous learning is practical training that will equip employees with real-life experience of how these attacks work. By providing a controlled environment, our phishing simulations create scenarios through which you can give your employees the skills to recognise, report, and curb the pretexting attempt.
Remember, the power to defend against pretexting lies in the hands of your employees. With the right knowledge and training, they become active defenders, capable of identifying and thwarting pretexting threats. Their vigilance, commitment to security, and willingness to report suspicious activities are the keys to maintaining a strong cyber security posture.




















