Discover how our phishing simulations turn your employees into active defenders of your organisation.

Human Risk Management
What are the differences between spear phishing and phishing?
No time to read? Listen instead:
Cybercriminals have long been operating at the professional level, and Cybercrime-as-a-Service has become a popular business model. One of the most effective and popular tools attackers have in their arsenal is spear phishing, which can be dangerous for individuals as well as entire organisations. This article is going to look at, amongst the different types of attacks that exist, what the differences are between phishing and spear phishing so that you won’t get lured into them.
Phishing in the current cyberthreat landscape
Cybercrime reached an unprecedented peak in 2022, with a spike in attacks as a result of global events that impacted the world such as the Ukraine war and the ongoing COVID-19 pandemic. Companies around the world are now facing an innovative dark economy that is becoming more sophisticated by the minute. Phishing waves based on current events, supply chain,and ransomware attacks, and deepfakes are just a few of the many dangers threatening organisations.
The majority of cyberattacks – over 82 percent – begin with the human factor, usually in the form of a phishing email. Recent studies have shown that the number of phishing attacks during the pandemic was a whopping 220 percent higher than the previous year. The way it changed the way we work with the transition to hybrid work models proved to be a boon and a bonus for cybercriminals. Cyberattack methods like phishing and spear phishing became more successful as a result of structural changes that left employees uncertain about IT policies or protecting data, and those in charge of security came under increased stress. It’s now harder for them to ensure cyber resiliency, across teams and at every level. Cybercriminals take advantage of vulnerabilities that are an outcome of dynamic changes, such as remote work, with social engineering. With this tactic, the criminals seek to emotionally manipulate people into disclosing confidential information (passwords, account data, etc.), circumvent security systems, or even carry out financial transactions, among other things. This tactic has proven to be very successful in times of uncertainty and change, and so it has quickly become a favorite amongst cybercriminals.
Let’s take a closer look at phishing, and what separates it from an even more dangerous tactic: spear phishing.
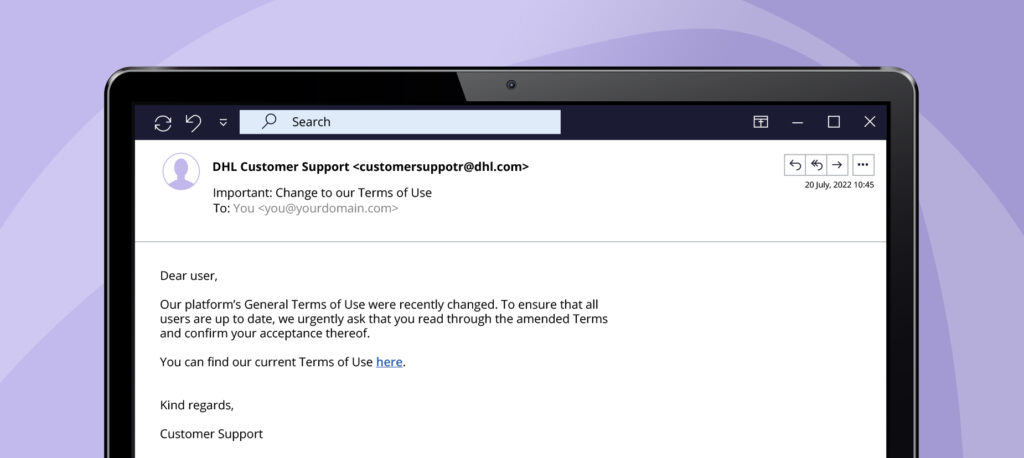
What is phishing?
Phishing is a type of digital fraud with which cybercriminals try to cause harm, usually with the motive to steal money or acquire personal information, and are often delivered in the form of a phishing email. Unlike spam emails, phishing emails are both annoying and dangerous: They can contain harmful content or seek to lure recipients into clicking on a link or downloading an attachment. For example, the shared URL could lead users to a form asking them to enter personal information like account details. If the recipient opens the attachment without paying attention to details, malware can be automatically installed on their computer. These are just two of many types of phishing. Our blog post “What’s the difference between spam and phishing?” contains more information on the many ways cybercriminals target users.

Phishing emails are sent en masse to multiple recipients. Cybercriminals are aware that most of these emails will not be successful in fulfilling their motives, which is why the effort that goes into making them is relatively low. This method is similar to casting out a fishing net: A few fish get caught, but most get away. However, there is a more sophisticated method that requires far more work and is also more successful, known as spear phishing.
What is spear phishing?
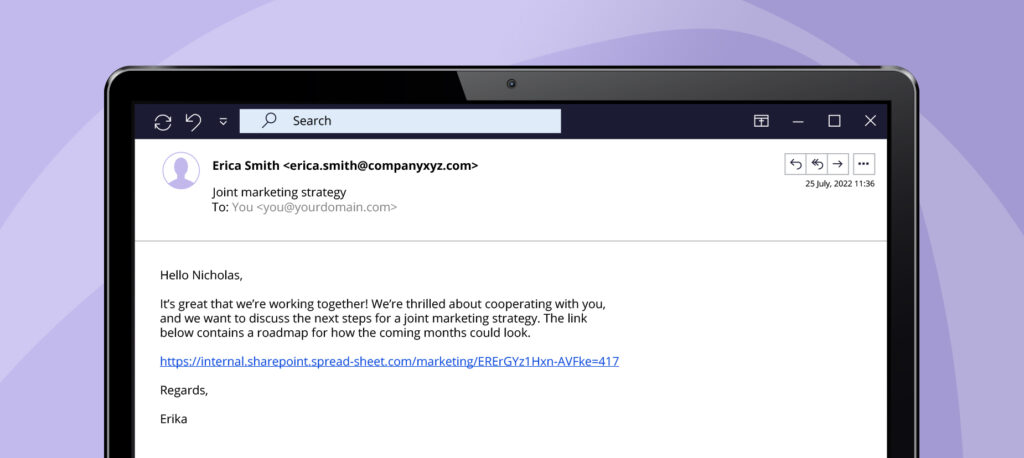
Much like a spear itself, spear phishing attacks are designed to target one specific individual or group – thus requiring a lot of research and preparation beforehand. Whereas conventional phishing is akin to casting a net, spear phishing requires taking a very close look at the targets in advance.
There are various ways in which cybercriminals can research their victims, including algorithms and crawlers that scour the Internet for personal and professional information. However, one relatively simple and highly effective method for getting info on potential victims is a Google search. Social networks and profiles on shopping websites provide details on buying habits, hobbies, preferences, and general interests. What makes spear phishing attacks so dangerous is that, because they are heavily tailored to a specific individual, they are much harder to recognise than “conventional” phishing attacks.
Imagine posting on a social network about how excited you are for an upcoming concert. This already makes a good reference point that cybercriminals can use to create fraudulent emails. Receiving an email that asks you to confirm your contact information for the tickets will then not seem out of the ordinary, but they have malicious motives that are not apparent at first glance. And these attacks have become common in everyday life: For example, a hacker can learn from a LinkedIn post that you’ve begun working with an agency. They could then pose as your contact person from that very agency and send you an email asking you to click on a link – a seemingly normal request but one that will carry regrettable consequences.
Spear-phishing vs. whaling
Some varieties of spear phishing have bigger, more authoritative targets in mind. When cybercriminals target C-level positions and other managers, this is referred to as “whaling”. What makes them prized targets is having access to highly confidential information. If decision makers at this level are compromised, the cybercriminals could demand high sums of money or threaten to release business secrets – both of which can harm the company’s finances and reputation.
A widely publicized example of this occurred in November 2020, when a co-founder of an Australian hedge fund – Levitas Capital – clicked on a fake Zoom link that installed malware onto his network. The attackers tried to steal 8.7 million dollars with forged invoices, although they were “only” able to make off with 800,000 dollars. Because of this incident the company’s reputation was so badly damaged that it lost its largest clients, and the hedge fund was forced to close.
Like the Levitas example, it is evident that cyberattacks can have serious consequences. To understand how these attacks are strategized, it is important to first learn the differences between spear phishing and phishing.
Make phishing attacks miss the mark
What differentiates spear phishing from phishing?
The biggest difference between spear phishing and phishing is the amount of effort and preparation involved in crafting the content. Phishing attacks generally involve little effort, and their generic nature makes them easy to create and recognise as harmful. Spear phishing, on the other hand, requires much more research, as cybercriminals need more time to create convincing and deceiving emails.
And this could soon become easier for criminals. According to a study by a research team in Singapore, it will soon be possible to misuse artificial intelligence (AI) to send spear phishing emails en masse. During the study, subjects clicked more frequently on AI-generated messages than they did on messages created by humans. This shows how easy it will be for cybercriminals to attack potential victims with harmful messages, that they don’t even have to spend effort in creating.
Another key difference is the way the reader is addressed. Phishing emails often contain very formal, inappropriate greetings that are easily recognised as artificial, which is why they are mostly unsuccessful. Spear phishing emails, on the other hand, look like they have been written by someone the recipient knows, and have a more familiar and personal touch.
Spear phishing is also very different from phishing when it comes to the target: Phishing emails are sent to hundreds or even thousands of random users, with the senders expecting most of the recipients to recognise it as a fake email. Spear phishing, on the other hand, is tailored to a particular recipient. It’s hard to tell spear phishing apart from a genuine message, as cybercriminals hope that the recipients will fall into this trap. Max Tjong-Ayong, Team Lead Social Engineering at SoSafe, explains the additional risk of spear phishing:
“We first have to understand that spear phishing attacks aren’t the same as mass phishing attacks. Spear phishing primarily targets specific individuals, and so is made to look genuine. If the attacker has enough time and preparation, it can be really hard to recognise a sophisticated spear phishing attack.”
Max Tjong-Ayong, Team Lead Social Engineering at SoSafe
Below is a summary of the most important differences between spear phishing and phishing.
| Spear – phishing | Phishing | |
| Recipient | Individual persons and groups | Hundreds or thousands of people |
| Delivery | Specific | Random |
| Effort | High | Low |
| Personal address | Personal | Impersonal |
| Tone | Familiar | Formal |
How to recognise phishing attacks
You have to be alert to successfully handle potential attacks. Because phishing emails often come from unknown senders, make unexpected demands, and contain unrealistic content, they can be easy to identify. You should always take the following steps in order to identify cyber security threats:
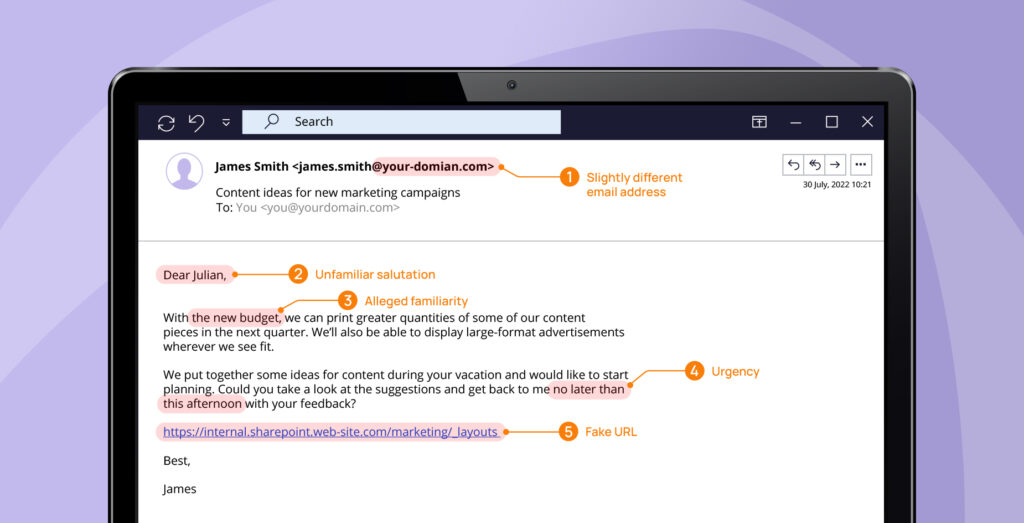
- Check the email address: Are there any grammatical errors or irregularities?
- Formalities of salutation: Does the salutation/closing seem artificial or unusual?
- Familiarity: Does the sender claim to know you and refer to something you are familiar with?
- Time pressure: Does the email create pressure by asking you to take care of something urgently?
- Check the hyperlink: Does the link match up with the URL that it leads to?
There are a number of indicators that you can use to tell whether an email might be a spear phishing or phishing attack. You can learn more about this in our blog post “How to spot a phishing email”.
Raising awareness: Foresight is better than hindsight
The examples we’ve presented show that phishing attacks are a danger that must be taken seriously, and that no organisation can be entirely immune to them. So how should you handle cyber security threats? While the threat landscape is rather complicated, the answer to this question is simple: Cyber Security Awareness Training.
9 out of 10 phishing attacks begin with the human factor, so it’s important for companies to teach their employees about the imminent dangers of such attacks and prepare them for the worst-case scenario. One effective way to stay protected against cyberthreats are phishing simulations, as they have been proven to raise awareness and provide realistic training for how to handle these threats. After one year of training, it can reduce human risk by as much as 88%. With consistent and continuous training, employees are better equipped to recognise and thwart phishing attempts.
Are you in charge of cyber security in your organisation and want to learn how phishing simulations can help your employees become an active line of defence? Or are you an employee and want to find out if your cyber security is robust? Start your Phishing Simulation demo and simulate realistic cyberthreats with personalized phishing templates. Take the next big step in strengthening your security culture.





















