Learn how to recognize potential dangers early on. Includes a checklist for detecting dangerous emails!

Cyber Security Awareness
What’s the difference between spam and phishing?
No time to read? Listen instead:
Unsolicited emails are delivered in bulk to inboxes around the world every day –including those that are hard to identify as harmful. Now more than ever, it is important to verify the legitimacy of emails without having to send back another email to do so. Yet the line between harmless junk and potential threats is as complex as it is ever-changing. Therefore, recognizing the difference between spam and phishing attacks is the first crucial step to prevent being wrongfully lured.
What’s spam?
Spam refers to unwanted electronic advertising sent to our email or text message inboxes. These spam emails are often referred to as “junk mails”, mainly due to their nature: They are sent en masse as unprompted and unwanted advertising.
The senders or ‘spammers’ are usually commercial entities sending spam emails with advertisements for products, invitations to participate in sweepstakes, or offers on appealing investments. While the GDPR does not regulate unsolicited email like spam, there are legal principles when it comes to collecting and processing personal data.
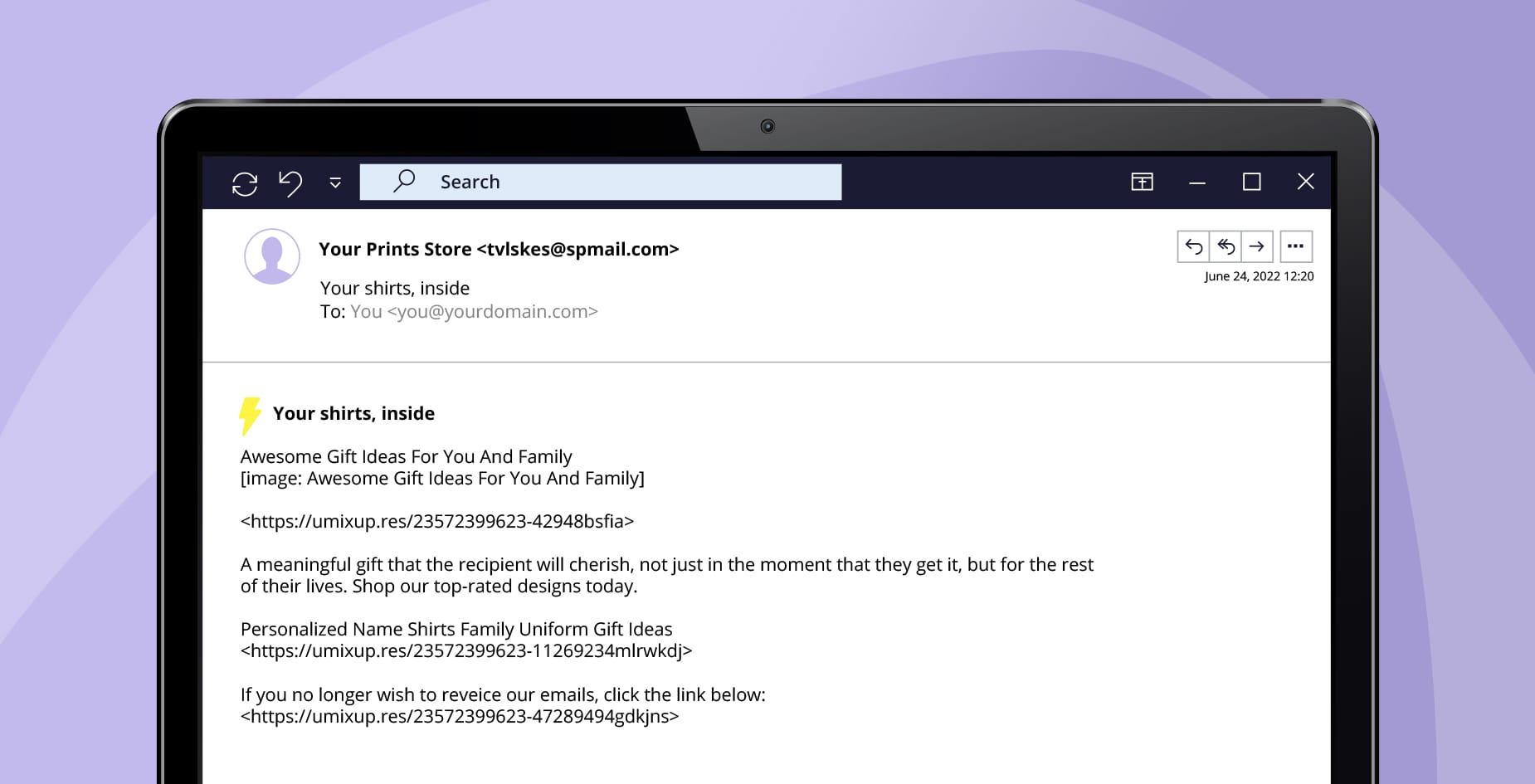
Spammers obtain email addresses in a variety of ways: by using automated tools to mine emails, using scanning programs on websites, buying email addresses from other companies, or even obtaining them on the dark net. As a result, spam can be sent to large groups of users simultaneously. These emails make it difficult for users to organize their inbox and become an everyday source of irritation—making them more likely to act carelessly.
Some common spam examples include:
- Delivery failure: Receiving a delivery failure email to one you never sent in the first place, which can include malicious links.
- Fake response: Getting a fake response, usually with the prefix ‘Re: Subject’ to something you never requested, luring you into sharing personal details.
- Social media notifications: Imposter social media profile or notifications from platforms you may or may not have subscribed to, with the intention of stealing your data.
What’s phishing?
Phishing can be considered a type of spam. However, it is always more malicious. More than three billion emails are sent every day in the form of phishing attacks. By forging the sender identity and exploiting the trust users have in reputed brands, executives, and even company CEOs, these deceitfully crafted emails end up putting users at risk. Cybercriminals use phishing attacks to dupe individuals or entire companies for financially enriching themselves.
By using emotional manipulation in the form of social engineering, the attackers compel users to click on links in their emails and trick them into providing sensitive information. The cybercriminals “fish” for personal information such as username and password for bank accounts, social media accounts, or other online accounts for their own criminal agenda. Obtained information can be further sold to other parties or on the dark net. Phishing proves to be an effective social engineering tactic as hackers exploit the user’s limited security awareness and tendency to click on messages without analyzing the contents.
Cybercriminals can also pose as companies or trust-worthy public institutions like banks. These messages have become so sophisticated that phishing emails are hard to differentiate from authentic emails. The more tactfully targeted emails are designed to get the user, a single recipient, to respond in the form of spear phishing. Phishers gather very specific information on their target from meticulous research and insider knowledge, and tailor the contents of the email to appear convincing as a trusted sender. The end objective is always about urging the user to click on malicious attachments or links.
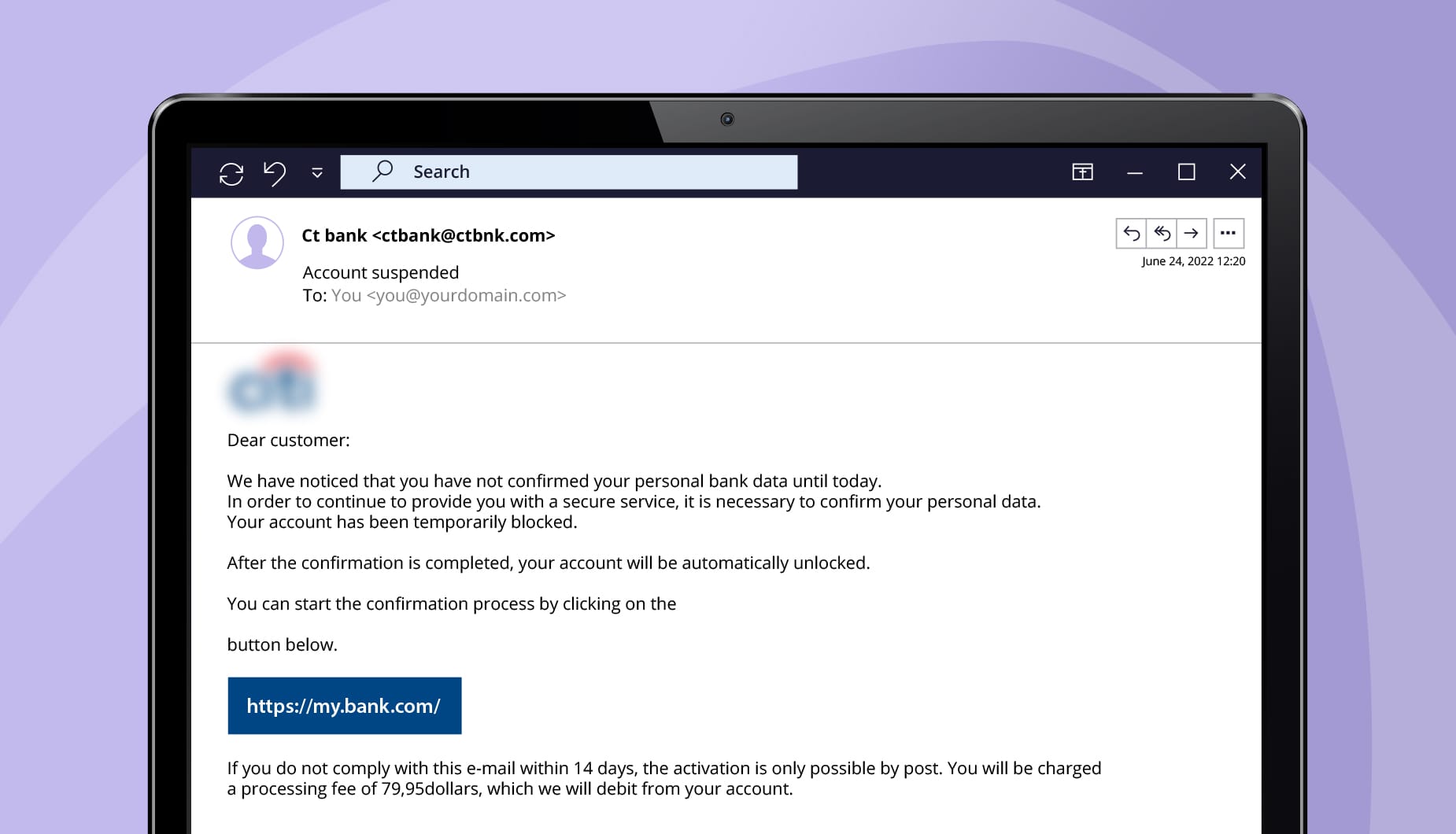
Out of the many variations that exist, some phishing examples are:
- Email account password change: Receiving notifications of email password change or expirations with urgent appeals from seemingly trusted sources.
- Document sharing: Getting links to google docs, from supposed known and unknown senders, encouraging you to click.
- CEO fraud: Urgent emails that are made to appear as if sent from your CEO, asking you to share confidential internal information.
Is phishing more dangerous than spam?
While spam emails can include harmless, mass advertising, phishing is targeted and malicious. In December 2021 alone, spam made up more than 45%, over 300 billion, of all emails. This goes on to show that as they are sent in massive volumes facilitated by botnets, spam has an immense reach. Their commercial nature and low implementation cost in spreading harmful content makes them a popular choice in defrauding users.
Malware spam is another type of phishing. This includes Trojan horses (also known as Trojans), viruses, and worms used to deceive users. If they click on an attachment in a supposed “marketing email” without thinking twice, malware is downloaded onto the user’s system. This malware spreads its harmful code throughout the infected devices and systems, allowing it to gain system access or steal data.
Each harmless spam email can thus be a phishing attempt in disguise. However, instead of focusing on the differences between them, it is far more important to know how emails can be dangerous. Users should practice identifying questionable emails to reduce their interactions with potentially malicious content and minimize personal and financial consequences thereof, regardless of whether emails are spam or phishing attempts.
Brief overview: Spam vs. Phishing
Phishing emails are often considered a type of spam, as they are also unsolicited and often sent to users in bulk. We have created a simple overview that summarizes the differences between these two types of email:
| Spam | Phishing | |
| Definition | Unwanted advertising emails sent in mass numbers | Fraudulent emails that lure users into disclosing sensitive data |
| Objective | Usually for advertising, but also used to send malware | Acquiring data, defrauding individuals or companies, financial self-enrichment |
| Examples | Product marketing, sweepstakes, offer of cash investment | Freezing bank account, urgent email from supervisor |
Do you want a more in-deep overview of the differences between spam and phishing and how to protect yourself? You can download our Phishing vs. Spam whitepaper here.
Spam vs phishing
info sheet

How to protect yourself against spam and phishing emails
Spotting the early signs is one of the effective first steps to keep your data secure. Here are some measures you can implement to reduce incoming and impact of malicious emails:

Worst-case scenario: What should you not do if you receive a suspicious email?
- Do not respond to spam or phishing emails, as this will signify to the spammer that this email address exists or has a real email format. The sender can then get motivated to target more employees of the company (e.g., firstname.surname@examplecompany.com).
- Do not click on links or attachments in emails sent by someone you do not know. Emails sent from an unknown source that you are not expecting should be examined more closely before you click on any links or attachments. You also should not click on the “Unsubscribe” button in a supposed newsletter without taking a closer look, because that can also be a dangerous link.
- Do not provide any personal information. If you receive emails that place pressure on you (including ones that come from “official” institutions or banks). Remain cautious. Contact the senders by telephone to verify.
“Using caution with messages that appear suspicious. Contacting your IT department or the bank, in specific cases, would be advisable. Clicking on unsolicited links or attachments is never recommended.”
Source: ENISA EUROPE
Long-term awareness: Why spam filters alone are insufficient
Spam and phishing emails both end up in our inboxes frequently. But, apart from staying vigilant, how can you prevent these unwanted and potentially dangerous emails? Spam filters are one option for keeping these emails out of your inbox in advance: Emails from specific addresses are sent directly to your spam folder.
But no technical filter is perfect, and an increasing number of spam and phishing emails are being circulated every day. Cybercriminals are professionalizing their templates to the extent that it is hard to differentiate between real and dangerous emails, many times even for spam filters.
Establishing safe habits when handling emails is paramount to minimizing risks —both in a personal and a professional environment. Testing users’ knowledge through practical examples is the best way to prepare for the worst-case scenario without any actual risk. Cyber security awareness training based on behavioral science covers this entire spectrum: Gamified learning modules and continuous phishing simulations help create a sustainable security culture in an interactive and impactful way – something we all need to make a priority, today.



