
Multi-Factor Authentication
What is multi-factor authentication?
Multi-factor authentication (MFA) is a security protocol that requires users to provide multiple credentials to authenticate their identities before they can access digital resources. Unlike traditional security systems that only require a username and password, MFA adds extra layers of protection. The user may be asked to provide a code sent to their phone/email, insert a device or token, or provide some type of biometric.
As we plunge deeper into the digital age, the significance of robust security measures can’t be overstated. MFA, as one of the gold standards in cyber security, is now being implemented by government institutions and major organisations such as Google, Microsoft, Amazon Web Services, and Apple to strengthen their cyber defence.
Although we recommend MFA as a powerful, additional security layer, it is not 100% hack-proof. In the past, hackers have been able to abuse vulnerabilities and access MFA-protected accounts through various methods. This includes the 2021 phishing attack on more than 10,000 organisations using Office 365 and the attack against Uber in 2022 that gave hackers access to internal information and Slack messages. This means that factors such as the way it is implemented, employee awareness regarding MFA attacks, and the number of complementary security measures in place will determine the security level it provides.

What is the difference between two-factor (2FA) and multi-factor authentication (MFA)?
Two-factor authentication (2FA) and multi-factor authentication (MFA) are often used interchangeably, but there is a subtle difference between the two. 2FA requires users to provide only two factors of authentication, while MFA requires users to present at least two factors of authentication. This means that all 2FA is MFA, but not all MFA is 2FA (only those with two authentication factors).
Both 2FA and MFA are widely used today. Websites, social media apps, and online services typically rely on 2FA, while websites, apps, and organisations with heightened cyber security measures or compliance obligations often implement MFA to protect sensitive data and systems. In the rest of this article, we will be using the broader term ‘MFA’ to refer to both two-factor and multi-factor authentication methods.
How does multi-factor authentication work?
While MFA may sound intimidating, most people have had experience with it, whether through email accounts, social media, or corporate systems. Even if the process may vary from service to service, it is usually very straightforward and consists of the following steps:
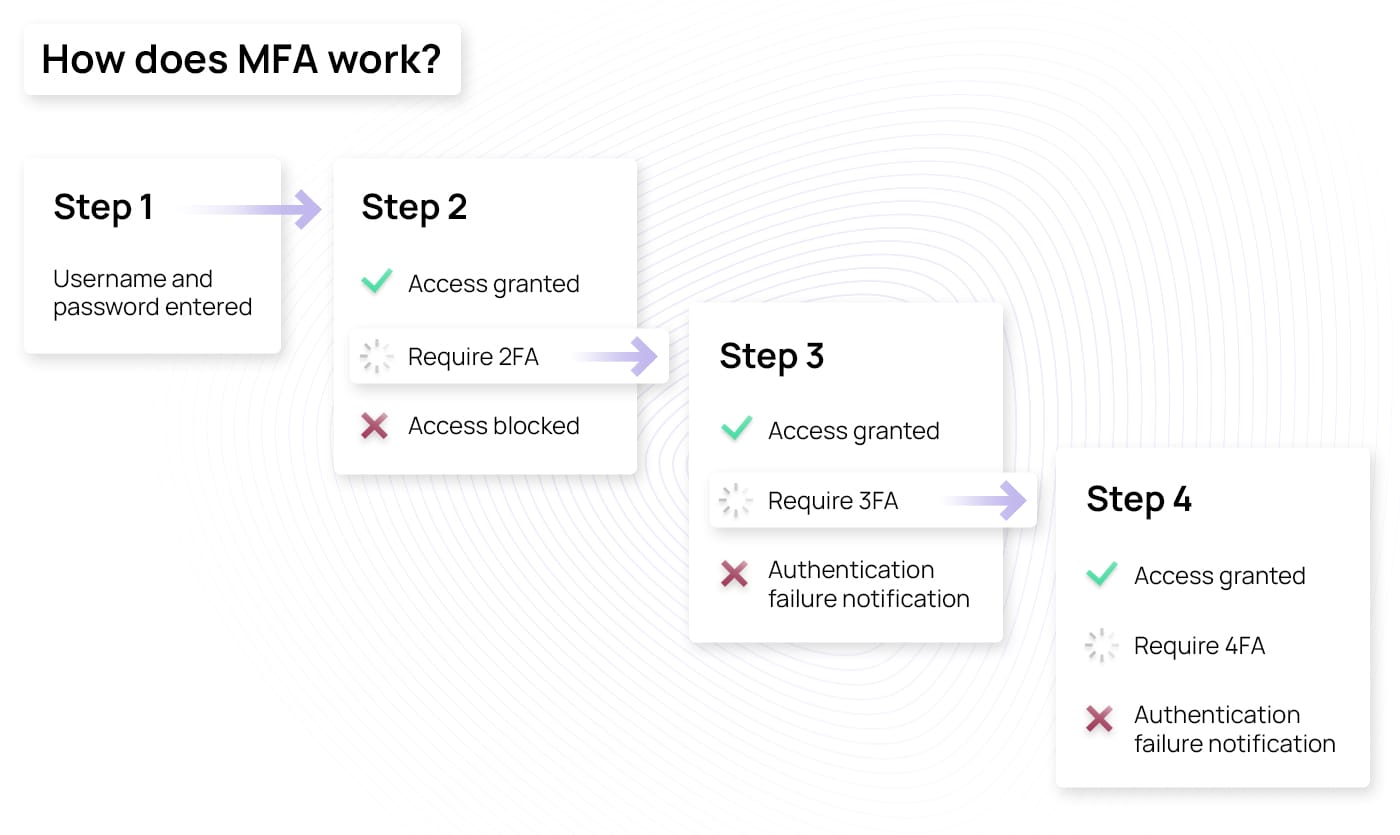
- Step 1: The user enters their username, email address, and password, which is considered the first verification factor.
- Step 2: The system validates the credentials by comparing them with the stored information. If it matches, the verification will proceed to the next step. Otherwise, you will receive a notification that the authentication failed.
- Step 3: After verifying the first factor, you will need to provide the second authenticator. This could be an OTP via SMS, using a mobile authentication app, inserting a device, or providing some type of biometrics. To find out more about the different types of authenticating factors, check the “More than just passwords” section further below in this article.
- Step 4: Once you enter the second-factor information, the system will check if it matches the expected input. If it does, you will be able to log in. If not, you will receive a notification that the authentication failed. If the authentication is successful and the website or application uses a two-factor authentication method, you will be able to log in. However, the system may require a third or fourth authentication factor, in which case, you would jump back to step 3 and continue the process by entering the remaining authentication factors.
Remember that you won’t be requested to provide a second factor every time you log in. Once you verify your identity, the MFA session will last for a specific period, which depends on the system you’re accessing.
Cyberattack prevention with MFA
The importance of MFA in cyber security lies in its ability to protect accounts and systems against unauthorized access. Even if attackers are able to get your credentials through the dark web, brute-forcing, phishing, or any other data leak, once the MFA initiates and requests the second verification factor, they won’t be able to complete the request. The attackers will then be denied access, and your account will remain secure against common attack methods like phishing, brute-force attacks, credential stuffing, man-in-the-middle attacks, and more. Moreover, the MFA initiation will also let you know that someone is trying to access your account, giving you enough time to change the security settings and prevent the attack.
MFA benefits: Protecting your information
By protecting against cyberattacks, MFA acts as a safeguard for your information and allows you to benefit from that extra layer of protection in many areas of your life, including both professional and personal contexts:
- Personal accounts: MFA ensures attackers can’t access your emails, social media accounts, and online shopping platform accounts. This means conversations, messages, and purchase history will remain private.
- Financial information: When you enable MFA on your online banking or payment platforms, it becomes much harder for unauthorized individuals to access your financial accounts. This protects your bank statements, transactions, and financial privacy.
- Business information: Many organisations use MFA to secure access to their internal systems, VPNs, and collabouration tools. This ensures that only authorized employees can access valuable corporate resources, including sensitive company data, confidential documents, and intellectual property.
- Cloud resources and remote access: Cloud storage platforms often provide the option to enable MFA so that you can protect your cloud-based documents, files, and information. This is especially beneficial for organisations with remote employees. In these situations, MFA helps organisations protect their resources by requiring employees trying to log in from a remote location to provide several authentications before being allowed into the system.
- Critical systems and infrastructure: In industries like healthcare, energy, or transportation, MFA is essential. They are crucial systems that need to be secure and operate continuously, so MFA helps maintain their integrity and availability.
More than just passwords: Types of MFA
MFA relies on several independent factors to verify the identity of the user trying to access the account or system. This usually includes something the user knows, something the user has, and something the user is. MFA can utilise a combination of two or more of these factors to enhance security and create a robust authentication mechanism. Let’s explore how MFA uses each of these factors:
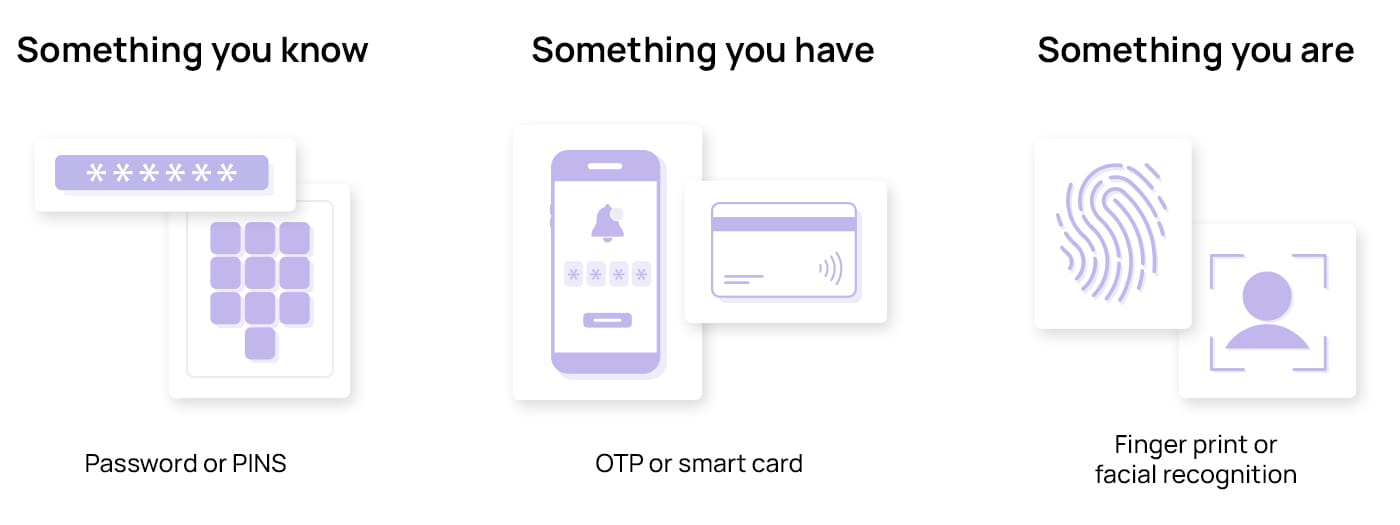
Something you know
As its name suggests, this is a knowledge factor. It’s something only you, the account owner, know, typically a password or a PIN (Personal Identification Number). This is the most common factor in MFA that you should enter as the first step in the authentication process.
One of the bigger issues with passwords is that most people use common password patterns, making their accounts vulnerable to a wide range of cyberattacks. Although there are a few recommendations users can follow to create strong passwords, there is always the potential danger of forgetting your password, creating an additional administrative burden for your organisation.
To help solve this, the FIDO (Fast Identity Online) Alliance and the WWWC (World Wide Web Consortium) introduced a password-free sign-in standard with which users can log in using alternative authenticators like a fingerprint, face scan, or a device PIN. As members of the FIDO Alliance, companies like Apple, Google, and Microsoft have announced their intention to implement this technology across their devices and platforms.
Something you have
This factor involves either possessing a device that generates a one-time password (OTP) you need to provide during the authentication process – such a mobile phone app or an OTP generator device – or a physical item embedded with a chip that has your credentials that you would need to insert into a device to authenticate, which could be a hardware token like USB, smart card, fob, or security key card.
Some OTP generators use a time-based authentication technology that relies on an algorithm to generate an OTP that is valid for a single use and for a short period of time, usually 30 seconds. This method – known as time-based one-time password or TOTP – is more efficient at keeping hackers at bay, since they will not be able to gain access with that OTP after it expires.
This possession factor acts as a safeguard because even if someone knows your password, they still need the physical item or device to complete the authentication process. When you change devices, remember to transfer your authentication information to the new device and delete the information on the old one if you won’t be using it anymore.
Something you are
The last factor is something you are, which involves biometric data. It refers to unique physical or behavioural traits that are difficult to replicate or forge. These factors include fingerprints, facial recognition, voice patterns, palm print, and iris scans. While some biometrics, like voice patterns, are easier to bypass and spoof due to the popularization of AI voice cloning tools, other biometrics are inherent to one person and are significantly harder to fake and, thus, abuse to bypass MFA.
The widespread adoption of smartphones and other mobile devices has made biometric verification more accessible. Many modern smartphones feature built-in fingerprint scanners or facial recognition capabilities, making MFA more convenient for both individuals and organisations.
Adaptive or risk-based authentication
Adaptive authentication takes into account various risk factors and adjusts the authentication requirements based on the perceived level of risk. It relies on artificial intelligence (AI) and machine learning (ML) to analyse various factors like behaviour, device information, geolocation, and IP address to compare your current login attempt against your established patterns. Deviations from the norm or unusual patterns, like logins during late or odd hours, unusual locations, public networks, or unknown devices, are flagged and given a risk score. The higher the risk score, the higher the likelihood of it being unauthorized access or fraudulent behaviour.
Based on the risk score, the system will adaptively apply additional authentication methods. It may ask you to provide additional verification or will send real-time alerts to you and your system administrator.
By leveraging AI and ML, risk-based authentication systems can analyse large volumes of data, identify patterns, and make accurate predictions about the risk levels associated with each authentication attempt. This approach helps protect against unauthorized access, account takeovers, and other security threats while not hindering the user’s authentication process by asking for several factors when the risk is low.
MFA hacking techniques
While MFA is highly secure, like other cyber security measures, it’s not entirely immune to attacks. Some vulnerabilities still exist, including social engineering attacks, compromised device security, or vulnerabilities in the implementation of the MFA. It’s essential to remain cautious, be mindful of device security, and stay informed about emerging MFA hacking techniques to maintain the highest level of security. Here are some of the most common ones you should be cautious of:
MFA fatigue
MFA fatigue is a social engineering cyberattack that works by spamming the target’s device with authentication requests until they give in and confirm the access. It’s a common method of MFA hacking that relies on the user’s resistance (or lack of) to spam requests. MFA fatigue was used to hack Uber in 2022, when a hacker stole an employee’s password and tricked them into approving the attacker’s push notification for Uber’s MFA. This allowed the attacker to access a network share with high-privilege credentials, which consequently led the attacker to Uber’s internal information and Slack messages.
Use phishing or vishing to get the verification code for authentication
In phishing and vishing, attackers use emotional or psychological manipulation to make you provide the information they need to bypass MFA. Phishing usually consists of attackers sending deceptive emails and messages that contain urgent requests, alarming statements, or enticing offers to grab your attention. In vishing attacks, on the other hand, attackers use the same emotional engineering methods, but rather than send emails, they make phone calls to potential victims. In both cases, attackers impersonate trusted individuals, such as bank representatives, customer support agents, or even government officials, to manipulate victims into providing sensitive MFA-related information.
Attacker-in-the-middle technique
The attacker-in-the-middle method is similar to phishing but a bit more sophisticated. The attack starts when the user clicks on a phishing email that directs them to a fraudulent login page meticulously designed to resemble the authentic one. These attackers employ a proxy, positioned between the fake and genuine pages, enabling the attackers to capture the session cookie produced when the user enters their login credentials and MFA passcode. After that, the hackers utilise these cookies within their own browsers to automatically access the targeted individual’s account, bypassing the need for further authentication. This is what happened in 2022 when a business email compromise campaign combined spear phishing and AitM to hack Microsoft 365 accounts of corporate executives, allowing hackers to divert large money transactions to the hackers’ bank accounts.
SIM-swapping
SIM-swapping is an efficient way of bypassing MFA relying on mobile numbers. This method doesn’t target users directly but rather the network service providers. Attackers pose as real subscribers and convince service providers to issue a new SIM and transfer the phone number to it. According to an FBI Public Service Announcement, SIM-swapping was responsible for adjusted losses of more than $68 million in 2021 alone. To overcome the risk of this happening, the FBI recommends keeping your mobile phone number private, avoiding posting or storing financial or personal information online, using a variety of unique passwords, using strong MFA methods, and keeping up with any changes in SMS-based connectivity.
Man-in-the-endpoint attacks
In a MitE attack, malware is installed on the user’s device, allowing hackers to start rogue sessions in the background – only visible to them – once the user completes MFA. The attackers can use the rogue session for malicious purposes, such as rerouting pay checks to the hacker’s bank account, obtaining information, exploiting trusted relationships, or modifying the current MFA settings.
Rebuilding password generators in OTP systems through reverse-engineering methods
Reverse engineering is a technique used by hackers to bypass one-time password generators used in authentication systems. These systems work with an algorithm and a seed number and deciphering them requires a high level of technical skill. If the cybercriminal achieves it, they can send passcodes to the user, thereby effectively bypassing MFA.
Consent phishing
Open authorization (OAuth) is an authorization framework used by applications to request limited access to users’ accounts without revealing their passwords. For instance, when you click a YouTube link through Instagram, OAuth requests access to your YouTube account without requiring verification. It’s a quick and convenient way of verifying your account without having to go through the whole login process.
However, attackers take advantage of this framework by creating fake applications that replicate legitimate ones, such as popular social media or productivity tools. If they gain access, attackers can bypass MFA requirements, enabling them to take over your account.
A cybersecurity investigation at GitHub in 2022 revealed that an attacker abused third-party OAuth user tokens to download private repositories from organisations. While there are no official reports of any damage, GitHub and the third-party token operators had to temporarily disable the integration to work on the issue.
Brute-force attacks
A brute-force attack relies on automated tools to obtain the verification code or break the MFA security. It does this by systematically trying all possible combinations of codes until it discovers the correct code. For instance, the attacker may get your login credentials through hacking or the dark web but lack the verification code sent to your device. However, with the right tools, cracking a 4-digit code, even if randomly generated, wouldn’t be difficult.
Accounts with MFA are generally less vulnerable to brute-force attacks than accounts protected solely by a password. However, the password’s strength also plays a role in the safety of your account. Brute-force attackers need only seconds to hack accounts with weak and common passwords, while complex passwords can take years to crack.
Stealing physical tokens
As we mentioned previously, most MFA methods rely on a possession factor, typically a hardware device that generates an OTP. As with any other physical item, attackers can steal the tokens, fobs, security keys, or other hardware and use them to generate an access code – especially if they are stored in an unsecured location. Physical tokens can also be compromised if they are misplaced or lost. If a token falls into the wrong hands, the person who finds it may attempt to use it for unauthorized access.
How to protect yourself against MFA hacking
By implementing reliable MFA methods and keeping up to date with the latest cyber trends, you can significantly reduce the chances of falling victim to MFA hacking and keep your online accounts secure. While no security measure can guarantee 100% protection against hacking, here are some things you can do to protect yourself:
- Create a strong password. The most important safeguard for an account is its password, so make sure you choose a strong and unique password for your accounts. You should also avoid using the same password across multiple accounts. If one account gets compromised, it could also give hackers access to your other accounts.
- Rely on biometrics. Whenever possible, use biometrics as an authentication factor. It’s the strongest verification method, as biometric data is unique, making it almost impossible to mimic or deceive.
- Use a reputable MFA app or device. It’s crucial to choose a reliable MFA method from trusted providers and keep it up to date. Options like Google Authenticator, Microsoft Authenticator, or hardware tokens like YubiKey can generate unique codes you’ll need to provide along with your password when logging in.
- Stay vigilant. As attackers commonly rely on phishing and vishing attacks, be skeptical of any messages asking for your personal information, even if they appear to be from trusted sources. Always verify the authenticity of the request through a separate channel before sharing sensitive information.
- Keep your devices and apps updated. Regularly update your devices, MFA apps, and operating systems to ensure you have the latest security patches and protections. Older versions may have vulnerabilities known to attackers, making them vulnerable to MFA hacking.
- Monitor account activity. Enable push notifications for suspicious login attempts or changes to your account. If you notice any unusual activity, take immediate action, such as changing your password or reporting the incident.
- Restrict the number of unsuccessful MFA login attempts. Limiting the number of failed login attempts can mitigate the risk of unauthorized access, as the system will temporarily or permanently block suspicious attempts. This is especially effective against brute-force attacks, as it ensures attackers can’t experiment and use many different credential combinations to access your account.
Combatting MFA hacks: How to mitigate risks in your company
Multi-factor authentication protects accounts by requiring users to provide more than two authenticators, making it significantly harder for attackers to gain unauthorized access. However, as security measures evolve, so do the methods employed by attackers. Hackers continuously refine their methods to exploit vulnerabilities and bypass MFA using methods such as MFA fatigue, phishing attacks, SIM swapping, attacker-in-the-middle, and other sophisticated techniques. Therefore, it’s important to remain updated on the latest hacking trends and employ a multi-faceted approach that includes not only MFA but also regular security awareness training, strong passwords, and timely software updates.
To help organisations combat the rising threat of MFA hacking, we have developed an e-learning curriculum where employees will get the knowledge to recognise MFA hacking attempts and the tools to prevent them. By using real-life scenarios and practical examples, our snackable modules can play a vital role in enhancing online security and promoting responsible digital practices in your organisation.


















