
Brute-Force Attack
What is a brute-force attack?
A brute-force attack in cyber security is a hacking method that uses automated software to find the correct combination of credentials that provide access to a system or account. It’s a time-consuming method requiring many resources but can be very effective against vulnerable passwords and accounts with weak security.
The pandemic and surge of recent working models, such as hybrid work and remote work, have fueled the acceleration of brute-force attacks in the past few years. 2021 was a critical year for cyber security with several high-profile hacking cases like the attack on Microsoft Exchange servers that gave attackers full access to the emails and passwords, administrator privileges, and devices of over 250,000 servers in several public organisations worldwide, such as the European Banking Authority and the Norwegian Parliament.
According to a study by Google Cloud in 2022, brute force is the most common attack vector used against cloud providers, with the main cause being weak or default passwords. More recent attacks, such as the hacking of Linux servers, demonstrated that this method remains an important threat in today’s cyberthreat landscape. Moreover, the latest developments in artificial intelligence allow hackers to crack more complex passwords in only seconds, underscoring the crucial need to adopt security measures like strong password policies, advanced detection systems, and multi-factor authentication to minimize the risk of falling victim to a brute-force attack.

Types of brute-force attacks
Hackers use different types of brute-force attacks to evade detection by security systems and make their activities less noticeable. Most brute-force attacks use automated software due to its speed and efficiency in testing a large number of username and password combinations to crack the system or find a vulnerability. They also prefer automated software because it eliminates the probability of human error that can happen during manual brute-force attacks, while allowing them to target multiple organisations or individuals. The main attack types are:
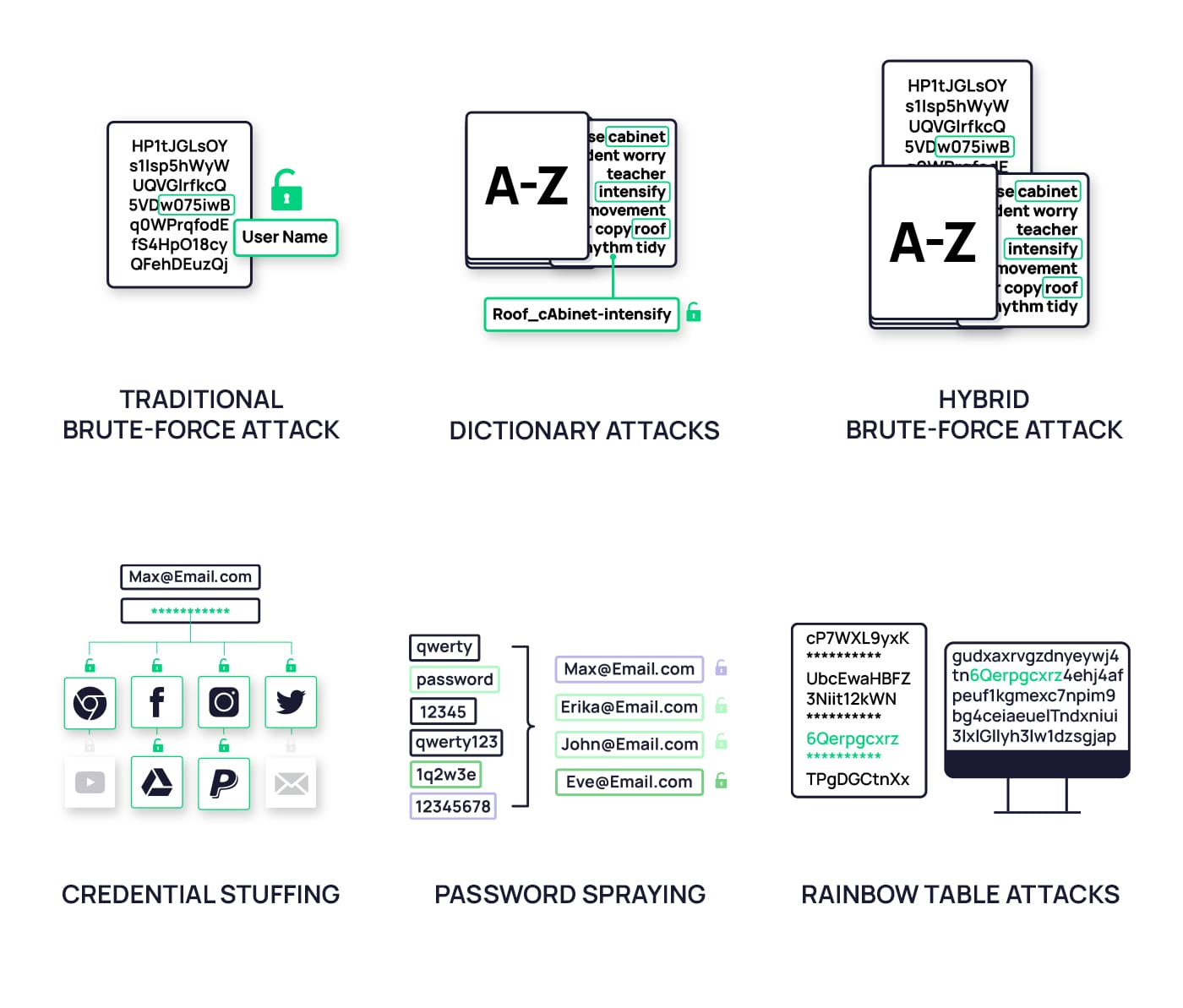
- Traditional brute-force attack: It uses hacking software that generates a random combination of characters until it discovers the correct password that matches a specific username.
- Dictionary attacks: This attack uses software that automatically tries the most commonly used words and phrases from a dictionary to discover the correct password. This underscores the importance of using passwords with random word combinations or invented words that would be unknown to the attackers but are completely logical and memorable for the user.
- Hybrid brute-force attack: This method combines the previous two – traditional and dictionary brute-forcing passwords. Attackers rely on sophisticated hacking software that uses dictionaries and random characters to guess the correct password.
- Credential stuffing: Attackers use previously hacked credentials and run the same username and password combination across different websites until it finds a match. Therefore, it is important to have different credentials for different points of access. If one gets hacked, the other ones will remain safe.
- Password spraying: Also known as “reverse brute-force attacks,” password spraying works the opposite of traditional brute-force attacks. With the traditional method, intruders try to determine the correct combination of passwords against a single username. Password spraying, on the other hand, relies only on the most commonly used passwords and runs them against a large number of usernames until it finds a match.
- Rainbow table attacks: In a rainbow table attack, the attacker uses a specially prepared table filled with precomputed hash values and their corresponding passwords. These hash values are the result of a mathematical algorithm that turns a password into a randomized sequence of letters and numbers. The attacker then gets a copy of the hashed passwords from the targeted system and compares them to the hash values in the rainbow table. If they find a matching hash value, they see its corresponding password in the table and can use it to access the user’s account.
Consequences of brute-force attacks
Everyone, from individuals to businesses, can be susceptible to the detrimental impacts of brute-force attacks, ranging from unauthorized access, financial losses, and identity theft to malware dissemination.
In the case of businesses, hackers often deceive certain employees to gain access to the organisation’s network, rather than targeting the entire entity. The repercussions are potentially catastrophic, leading to financial losses, legal liabilities, damage to reputation, and loss of customer trust:
- Unauthorized access
When a system becomes compromised, attackers gain access to emails, social media accounts, and financial information they can use for manipulation, data theft, the spread of malware, and other malicious activities. Moreover, if individuals use the same password for multiple accounts, attackers can use the already hacked credentials to access those accounts as well. - Monetary loss
A successful brute-force attack can lead to the theft of financial information of individuals or organisations. Intruders may use this information to steal funds from financial accounts and cryptocurrency wallets, make unauthorized purchases from malicious websites, or ask for a ransom to give back access to the hacked account and return the stolen information, as the case with T-Mobile in 2021 illustrated. As a result of unauthorized access to its systems, the personal data of over 76 million users was listed for sale on a cybercriminal forum. This resulted in a significant financial loss of $350 million for the company in the form of settlement and legal fees. - Identity theft
Attackers may try to access personal information like names, emails, addresses, Social Security numbers, and credit card data to commit fraud, ask for ransom, blackmail individuals, carry out cyberstalking, steal data, damage the victim’s reputation, or commit other criminal activities. This can cause multiple issues for the victim, including damage to credit scores and legal repercussions, making the recovery from this attack difficult and time-consuming. - Spread of malware
If intruders successfully enter a system, they gain access to contact lists and devices they can use to distribute malware, ransomware, and other malicious software within the compromised system. For example, attackers can use a hacked email account to send spam emails and malware attachments or add devices and systems to a botnet that will then spread it to other systems within the organisation. This gives attackers access to the target’s system, which they can use to steal data, view other account credentials, or find valuable information. - Loss of intellectual property
Attackers can steal or modify valuable intellectual property like trade secrets, proprietary information, or research data to gain a competitive advantage. Losing intellectual property can result in a decline in the organisation’s market position, as competitors may replicate or improve upon stolen innovations. - Damage to reputation
Insufficient cyber security measures can affect the organisation’s brand and reputation, especially if personal information leaks happen. When customers, partners, and even competitors lose trust in an organisation, it may result in business declines, broken partnerships, or loss of revenue opportunities. According to a Forbes Insight report, an IT system failure, such as those caused by cyber security breaches, has the potential to do the most damage to an organisation’s reputation. They also found that the reputational damage lasts far longer than the recovery time, and in some cases, it persists for years after the attack. - Legal and regulatory consequences
Organizations may face legal and regulatory penalties for failing to protect user data or maintain compliance with data protection regulations like the EU Cybersecurity Act, General Data Protection Regulation (GDPR), and Health Insurance Portability and Accountability Act (HIPAA). - Business disruption
Successful brute-force attacks can cause system downtime, disrupt operations, and compromise essential services, leading to lost productivity and additional costs to recover from the incident. While the organisation copes with the brute-force attack, it may also experience lost opportunity costs like missed contacts, emails, sales, deals, or investments that would otherwise occur if the brute-force attack didn’t happen.
Common attack tools: Cybercriminals’ go-to brute-force arsenal
Depending on the objective, cybercriminals use a variety of tools or combination of them to carry out brute-force attacks. These tools often rely on sophisticated and powerful software to crack usernames and passwords or exploit a vulnerability in a system.
Knowing the main tools hackers use and how they work can help organisations take appropriate measures to protect their accounts and systems from brute-force threats. With that in mind, the most common tools used for brute-force attacks include:
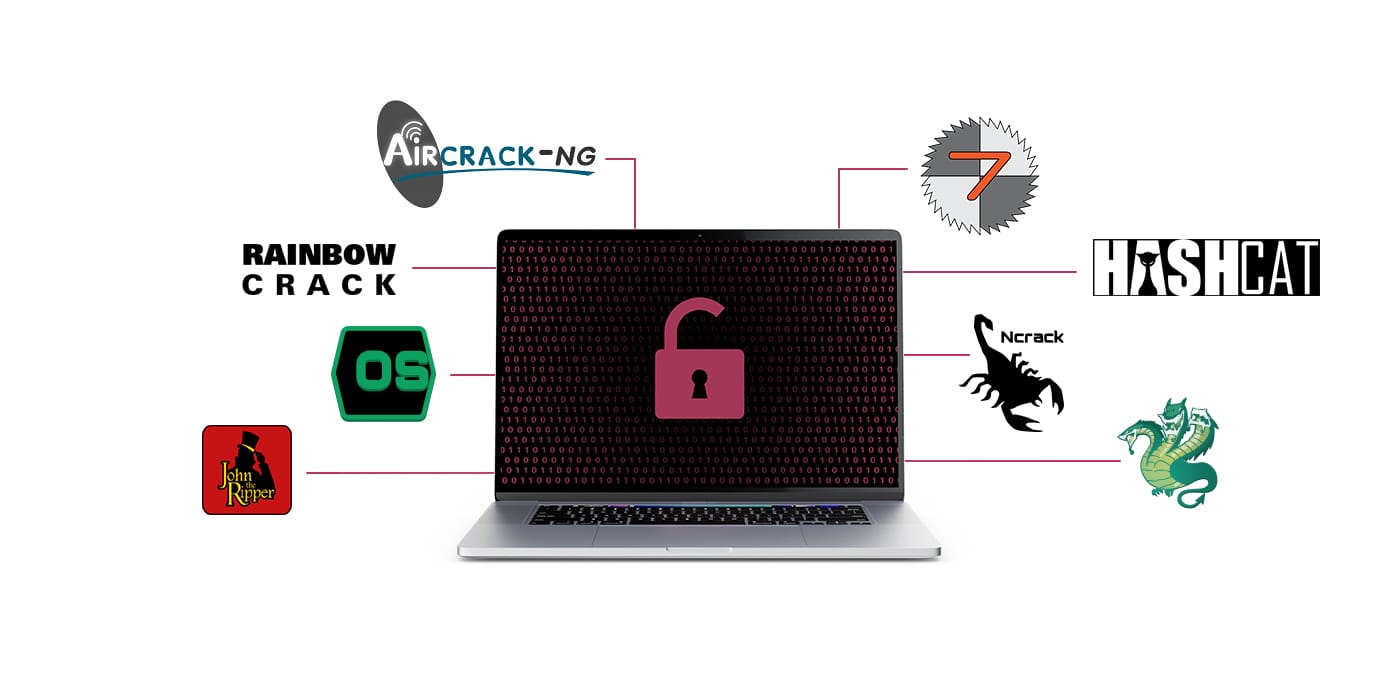
- Aircrack-ng: A free Wi-Fi cracking tool that uses a dictionary of commonly used passwords to hack wireless networks. The success of this tool depends greatly on the password dictionary. The better and more effective the password dictionary is, the better the chances are for cybercriminals to hack the system.
- Rainbow Crack: Another popular attack tool that generates precomputed rainbow tables to reduce the time needed to crack a password. The rainbow tables contain a list of password hashes that are run through a database through multiple reduction stages to split into smaller components.
- L0phtCrack: Extremely effective on Windows passwords, this tool uses a combination of methods like dictionaries, rainbow tables, scheduling, network monitoring, hash extraction from 64-bit versions, network monitoring, and multiprocessor algorithms to access an account.
- Hashcat: An advanced brute-force hacking tool relying on advanced algorithms to crack passwords through traditional brute-force, dictionary, and hybrid attacks. It supports several hashing algorithms, including LM Hashes, SHA-family, Unix Crypt formats, MySQL, MD4, MD5, and Cisco PIX.
- Ncrack: A high-speed cracking tool for testing networking devices and hosts that hackers use to access the network and hack weak passwords. It uses a list of username and password combinations to try, which can be generated manually or obtained through password databases or leaks. The tool then runs each combination against the targeted network until it finds a match. It supports many protocols, including SSH, RDP, FTP, Telnet, HTTP(S), WordPress, POP3(S), IMAP, and more.
- THC Hydra: One of the most popular brute-force attack tools hackers use to attack login pages and credentials. It relies on dictionaries or wordlists and systematically tries each username and password combination against the target page. The tool distinguishes successful and unsuccessful attacks based on the response codes and messages it receives from the system. It can crack passwords from multiple protocols, including FTP, HTTP, HTTPS, IMAP, MS-SQL, MySQL, PostgreSQL, and more.
- John the Ripper: This is a tool security professionals use to test the strength of a password. It relies on lists of commonly used passwords, dictionary words, and variations. It can also add numbers or special characters to create variations and increase the chances of finding a matching password. John the Ripper can also hack passwords by detecting the hashing algorithm type used to encrypt passwords and using rainbow tables to match the hashes to the correct password.
- Ophcrack: Another effective method for brute-forcing passwords of Windows systems. It uses rainbow tables to crack passwords with less than 14 characters and only alphanumeric characters.
How fast can a hacker crack a password?
The time needed to crack a password varies from a few seconds to billions of years, depending on factors like the length and complexity of the password, encryption algorithm used to store the password, and resources and tools available for the attacker.
Password complexity
Passwords that are simple, short, and contain only numerical or alphabetical characters are the easiest to crack. In contrast, passwords containing a mix of characters like numbers, upper and lowercase letters, and symbols can take months or years to crack. It’s also important to note that using passwords that have already been hacked can make you an easy target and help hackers access your accounts instantly.
As technology advances, hackers gain access to advanced tools that drastically shorten the time required to crack a password. A password with 10 characters comprised of numbers, lowercase and uppercase letters, and symbols would take five months to hack in 2022. The same password in 2023 can be hacked in two weeks. This shows how fast hacking tools evolve and the need for companies and individuals to keep up with the latest cybersecurity trends to protect their accounts and systems.

Password encryption algorithm
The next factor determining how easy or difficult it is for hackers to access a system is the password encryption algorithm. Password encryption converts password characters into hash values and stores them in a database, so when attackers try to view it, they only see a random string of letters and numbers.
The complexity of that string of letters and numbers depends on the encryption algorithm used and, thus, the difficulty of accessing it. For example, more recent and strong encryption algorithms like bcrypt and scrypt might take far longer to decrypt than older and weaker algorithms like MD5 and SHA1.
Attackers’ arsenal
Finally, the resources at the attacker’s disposal also affect how quickly they can crack a password. Passwords can be cracked significantly quicker by attackers with access to strong computers and GPUs than those without. However, recent technological advancements and a stronger presence of AI tools in the cyberthreat landscape have significantly cut the time and resources needed to crack a password.
ChatGPT, as the leader in AI, has been regarded as an efficient tool attackers used to perform brute-force attacks. Attackers can rely on ChatGPT’s language generation capabilities to generate potential username and password combinations and launch brute-force attacks. The use of this tool has proven to drastically shorten the time needed to crack a password, with many passwords being hacked instantly or within seconds. For example, the same password with 10 characters comprised of numbers, lowercase and uppercase letters, and symbols of the previous section would take 1 hour with chatGPT.
Most commonly used passwords
Considering hackers are relying on more sophisticated password-hacking methods that are capable of cracking complex passwords, choosing a simple and easy-to-guess password enables them to get into a system easily. Hence, individuals and organisations need to understand the importance of using unique and complex passwords and avoid using simple and common passwords.
Studies show that the most common passwords are “123456,” “123456789,” and “qwerty.” These simple passwords are easy to come up with and memorize but even easier to guess, enabling brute-force attackers to access accounts in only seconds, as we showed in the previous section. Moreover, many individuals use easily attainable information as part of their passwords, including their birthdays, pet names, anniversaries, and addresses. This information is not only predictable and easy to crack using dictionary-based brute-force methods, but it is also relatively easy to find on social media, so hackers can try fewer combinations using these numbers and words and hack an account faster and easier.

How to prevent brute-force attacks
Brute-force hacking can be a time and resource-intensive process. However, the consequences can be detrimental to both individuals and organisations, highlighting the importance of having the correct cyber security protocols in place. Strong security practices are the best way to prevent brute-force attacks. This includes creating complex and unique passwords, using two-factor authentication, limiting login attempts, monitoring, logging, using CAPTCHA, and using an IT denylist.
Use strong passwords
The following practices apply to both individuals and companies and help you create strong and reliable passwords. By implementing them, users and organisations can significantly lower the chance of a successful brute-force attack and protect confidential data and assets:
- Avoid using the same password for multiple accounts: Using the same or even similar passwords weakens the security of both accounts. If hackers can access one of your accounts, they can use the already hacked password to access other accounts, further compromising your data and systems. You should also avoid using passwords derived from other passwords.
- Don’t use a password that is easy to guess: Avoid using common words or phrases, personal information, sequential or repetitive characters, and short passwords that make them easy to guess by brute-force attackers. It’s advisable to use passwords that are at least 12 characters long and include a combination of letters, numbers, and symbols. Avoid words that appear in the dictionary, as they are likely to be targeted by dictionary attacks.
- Develop personalized password guidelines to craft complex passphrases: The strongest passwords are ones the user can easily remember but make no sense to anyone else. For example, you can replace “wood” with “wd” to create a unique string, omit vowels, or incorporate only some letters of each word. Additionally, you can use memorable phrases like quotes, song lyrics, and traditional sayings that only you know, use only the initial letter of each word, and then make the password even more complex by adding numbers and special characters.
- Use a password manager: A password manager helps you create long and complex passwords for each account you own and store them safely on your phone, tablet, or computer. You only need to remember one “master” password to access the stored information or use biometric access.
Regarding business password policies, it is important to remember that different levels of security are required for different access types. The following table provides a representation of the different password requirements collected in a business password policy depending on the access type the password gives access to:
Standard passwords
| length: | minimum of 12 characters |
| complexity: | 1 upper case letter, 1 lower case letter, 1 special character, 1 number |
| max. age | does not expire |
Passwords for privileged access
| length: | minimum of 16 characters |
| complexity: | minimum: 1 upper case letter, 1 lower case letter, 1 special character, 1 number |
| max. age | does not expire |
Passwords managed by a password manager
| length: | minimum of 24 characters |
| complexity: | minimum: 1 upper case letter, 1 lower case letter, 1 special character, 1 number |
| max. age | does not expire |
Use multi-factor authentication (MFA)
Multi-factor authentication is an extra security measure that requires an individual to provide two forms of identification. It’s usually something the user knows like a password or pin code, and something the user has, such as a mobile phone, security token, or biometric identifier like a fingerprint or Face ID. Users can access the account only once they verify both identifiers. This adds an extra security layer, preventing attackers from accessing the account even if they crack the password.
However, while many organisations rely on MFA to safeguard against brute-force attacks, and it has proven to be an effective method to minimize risks, hackers have also found ways to bypass it. They can do this by requesting a password change, using an authentication token from a third-party site, using a previously generated token, sending phishing emails to the account owner, or even using brute-force attacks against the authentication code. Additionally, attackers can use multi-factor authentication (MFA) fatigue attacks to coerce them into confirming their identity. MFA fatigue involves spamming the target’s email, phone, or registered devices with MFA requests until they complete the verification. Being aware of all these tactics can prevent you from eventually falling for them.
Limit login attempts
Limiting login attempts effectively prevents brute-force attacks because it limits the number of unsuccessful attempts that can be made during account authentication. The system automatically locks out the user if they fail to provide the right credentials after several attempts. The user remains locked out for a certain period, which increases after each subsequent failed attempt. This prevents attackers from cracking your password by trial and error, as they will be unable to try every combination of characters in a reasonable time.
Monitoring and logging
By monitoring, individuals and organisations can detect unusual activity like failed login attempts within a short period. It can also help identify employees trying to access sensitive information without authorization.
Logging can help track the user’s ID, IP address, date, time, and when and how many failed login attempts occurred. Organizations can later use this information to analyse patterns and detect potential threats. Even if a security breach happens, logs can provide valuable information for forensic analysis.
Many security information and event management (SIEM) systems can automate the monitoring and logging process, making it easy for organisations to keep track of suspicious activities and anomalies.
Use CAPTCHA
You can make it more difficult for automated brute-force attacks to succeed by requiring users to complete a CAPTCHA before logging in. A CAPTCHA is a visual or audio challenge designed to verify whether the user is a human or a computer. Most brute-force attacks rely on automated software that cannot pass CAPTCHA challenges. Organizations can ensure that only legitimate users can access their systems by requesting users to complete one before logging in.
Use an IP denylist
Also known as a blacklist, an IP denylist is a list of IP addresses identified as a source of malicious traffic or unwanted activity. When an IP address is added to a denylist, all traffic from it is blocked.
Organizations can implement IP denylists through various methods, including firewall rules, intrusion detection and prevention systems (IDPS), or web application firewalls (WAF). However, these IP denylists have limitations, as attackers can use proxy servers and botnets to cover up their IP address and avoid being detected by the IP denylist. If your organisation uses one, ensure it is regularly updated by those who manage it, manually or automatically.
Update software and firmware
Outdated software and firmware often expose vulnerabilities hackers can use to perform brute-force attacks against a system. Keeping software and firmware updated can help ensure these security vulnerabilities are patched and new security features are implemented. Regularly updating your software and firmware will also keep away attackers relying on outdated and unsupported protocols or algorithms.
Brute-force attack prevention: How companies can enhance their security
In today’s increasingly digital landscape, the threat of brute-force attacks looms large for companies of all sizes and industries. This is why it’s important to know what a brute-force attack is, its importance, the factors that contribute to it happening, and how to prevent it from happening.
As cybercriminals continuously evolve their tactics, technology alone is not enough to protect an organisation from a brute-force attack. Organizations must take further proactive measures to prevent and mitigate the risks of brute-force attacks, including implementing strong security policies, regularly updating cyber security procedures, and employee training and awareness. Employees must have the right tools to create strong passwords and adhere to security measures to protect the organisation’s accounts, information, and systems.
SoSafe focuses extensively on providing comprehensive training to organisations and individuals looking to improve their practical skills to safeguard their accounts and systems. We use hands-on exercises, targeted and behaviour-based simulations, and personalized interactive e-learning to provide employees with tools and techniques they can later apply in the workplace – as well as in their private lives – to keep your business’ important information safe.


















