
Malware
What is malware?
Malware, or malicious software, is any type of software used by cybercriminals to disrupt a computer’s normal functioning. It includes various types, such as Trojans, ransomware, viruses, and spyware, which hackers use to access sensitive information, disrupt businesses, lock out users, or spread harmful software across networks.
Malware can be introduced into a computer from several sources, including emails, downloads, websites, and external storage devices. The possibilities are endless. No matter the source of the attack, the end results can be disruptive to both individuals and companies, making it important to learn how to protect yourself and your company from the potential for malware attacks.
Some types of malware, such as ransomware, have caused much damage to individuals and companies worldwide, with specific ransomware groups like Conti attacking numerous organizations such as Parker-Hannifin, whose data breach in 2022 exposed the personal information of employees and members of the company’s health plan. The same group was also responsible for the ransomware attack on the Costa Rican government, leading to a state of emergency in May 2022.

Is malware a virus?
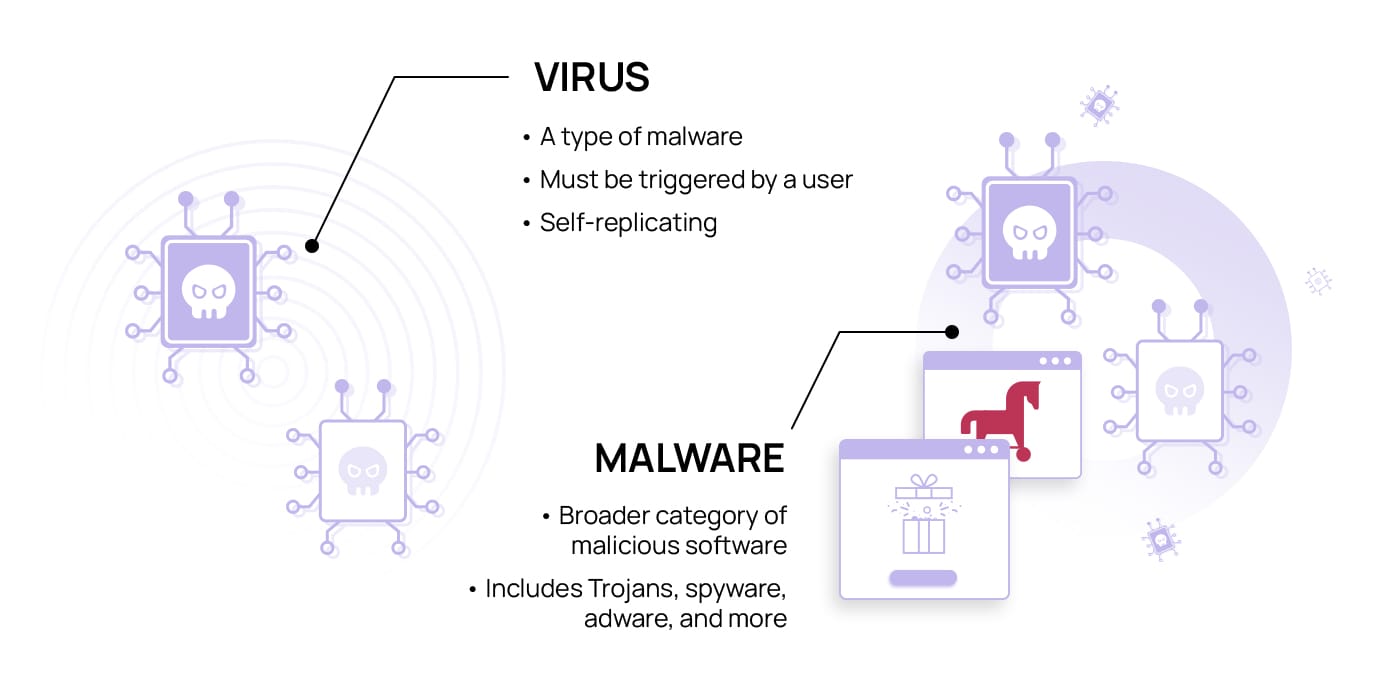
Many people use the terms malware and virus interchangeably, which can lead to confusion between the two. While viruses are a type of malware, not all malware is a virus.
Viruses are specific types of malware that are designed to replicate themselves. It may use this replication to insert itself into other programs within one system or spread between systems, moving between different computers. Viruses are generally attached to or originate in one specific program, such as a document you downloaded. Once in the computer, the virus can be activated to spread between applications or systems. Malware is a larger, broader category of malicious software that can include viruses and other things, such as ransomware, spyware, bots, and adware.
Why is malware dangerous?
Malware poses significant risks and can lead to severe repercussions for anyone using computers or internet-connected devices. This includes not only major corporations and governments but also individual users and small companies.
Malware varies in its impact on individuals, ranging from mere nuisances, such as adware flooding their screens with popups or causing system slowdowns, to devastating consequences when personal account information or sensitive data is compromised. Moreover, hackers can exploit malware to collect personal information, enabling them to craft more targeted and effective social engineering attacks.
Major businesses and corporations are often the targets of serious malware attacks. The consequences vary from the slowing of a system compromised with a botnet to serious ransomware attacks that can cost the company millions of dollars in lost productivity and in the ransom itself. According to a report by IBM, ransomware attacks cost companies an average of $4.54 million in 2022, not including the ransom cost. If a company pays the ransom, losses could be even higher, particularly as some hackers will not release the files on receipt of the funds as promised. Corporate espionage can also be a major concern for some companies, particularly those attempting to keep details about an upcoming product or release quiet until a public revealing. A hacker gaining access to this information could sell it to a competitor that may try to beat the original company to a release.
Small businesses may also be targets of hackers, with even more devastating results. In fact, one in four British small and medium enterprises was targeted by ransomware in 2022, according to a study by Avast. While a large corporation may have the funds to meet a ransom demand or cover the cost of the lost productivity that can come with a malware attack, small businesses often do not. If a malware attack were to leak or compromise sensitive data or cause a small business to be unable to meet its responsibilities, the business’ reputation might suffer, which can be devastating for some companies, even if funds are not lost. A malware attack could prove fatal for many small businesses, causing the company to shut its doors.
Different types of malware
Each type of malware generally has a specific purpose, so the types you encounter vary, depending on the hacker’s goals. Below are the most common types:
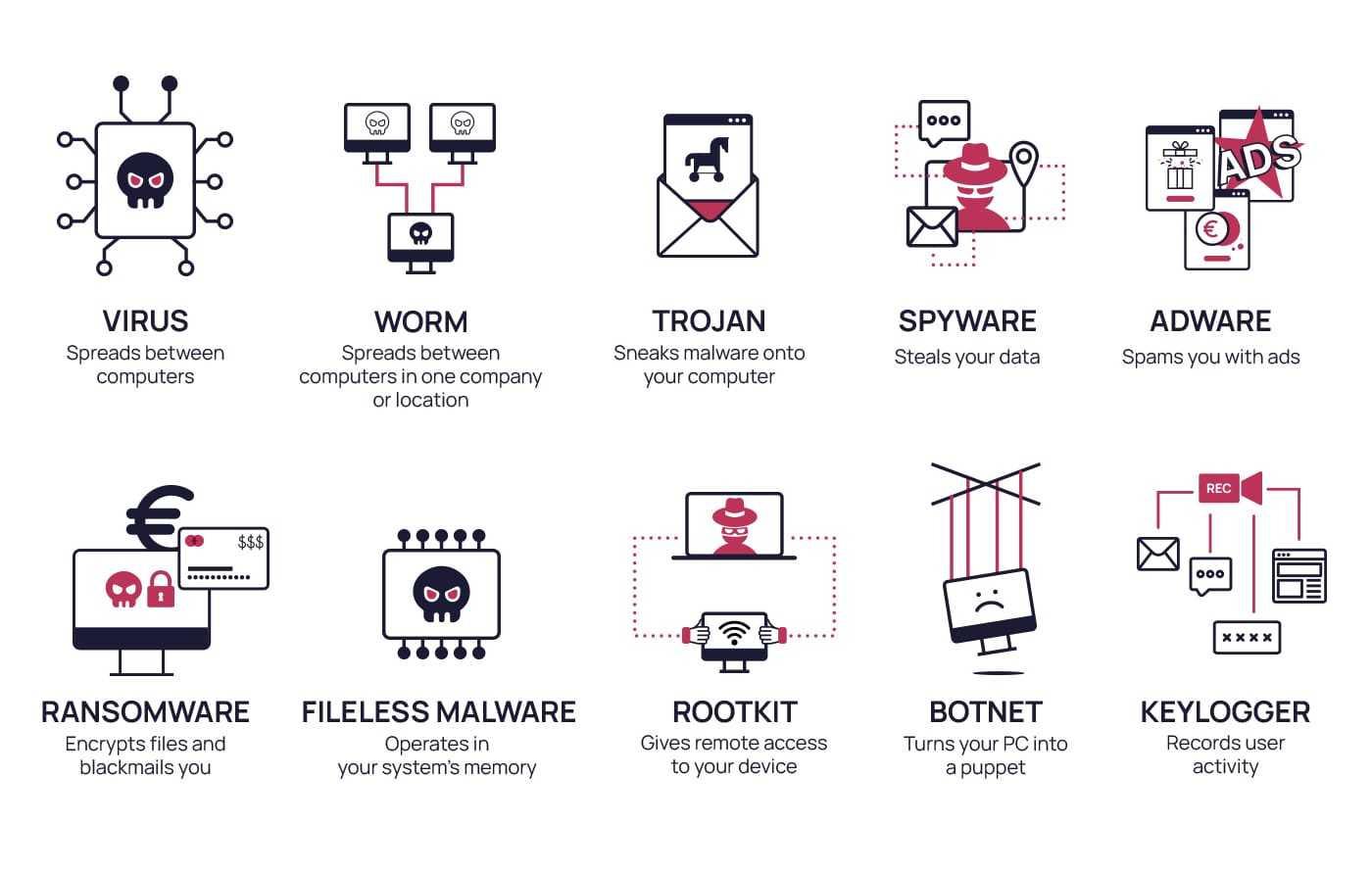
- Viruses: Malware that uses replication to insert itself into different applications in a computer or to spread between computers. Viruses can infect computers for different purposes, such as deleting or corrupting your data and apps, or hijacking your emails to spread themselves to other programs.
- Worms: Similar to viruses, worms replicate themselves and spread, but while a virus may spread through email to different households and companies, worms tend to target computers that are linked in one company or location. They may be used to transport another type of malware.
- Ransomware: A form of blackmail that cybercriminals use to try and extort money from people and corporations. Generally, ransomware encrypts the files in a system, making them inaccessible. The hacker will promise to release the encryption upon receiving a sum of money (or cryptocurrency).
- Adware: A type of malware designed to show you ads that do not belong to the websites you are visiting. These ads are generally considered spam and may include popups and other disruptive or invasive tactics. By using adware, hackers collect data from your browsing habits, which they may sell to third parties.
- Spyware: An unobtrusive malware that is difficult to detect. It runs in the background of your computer and collects information about the user, including passwords and account, banking, and credit card information.
- Fileless malware: This malware is almost undetectable. Instead of being stored in a file on your hard drive like most types of malware, it operates directly in your system’s memory, allowing hackers to access your files without raising suspicion.
- Rootkit: Rootkits give the attacker remote access to your device. Once inside, they can access and control files, spy on the user, steal personal data, or install malware, among other things.
- Keylogger: Keyloggers record user keystrokes, device activities, and track actions. They capture sensitive information, including passwords, and send it to the controlling hacker.
- Trojans: Trojans or Trojan horses are often used to get other types of malware onto a computer. They are typically disguised as a trustworthy source to manipulate the user into downloading the malware. They can affect your devices in many ways, depending on the type of malware it hides. For example, backdoor Trojans allow hackers to access and control your device, resulting in the ability to steal your data or infect your computer with more malware.
- Botnet: When a group of computers is infected with the same malware, a botnet can make them work together without the users’ knowledge. This gives hackers more resources to carry out other attacks, such as distributing more malware.
While these are some of the more common types of malware, others may also be used. These can include variations like malicious cryptomining, also called drive-by mining or cryptojacking, which steals cryptocurrency from a user’s wallet, and exploits and zero-day exploits, which attack vulnerabilities in a system that the user may not be aware of. Other types of malware are scareware, which convinces the user to download antivirus software, making them believe they have been hacked, and wiper malware, which erases your system’s memory.
Main points of access for malware
Malware can enter your system through a wide range of access points. Email phishing and fraudulent websites are two of the preferred methods by hackers. However, texts, chats, fraudulent apps, and social media are also potentially targeted channels that we should protect against threats.
Email phishing is one of the most popular methods for hackers to gain access to a user’s computer. Today, phishing looks like well-crafted emails that inspire urgency in the user, who usually clicks on a link or downloads a file containing malware. These emails can be highly personalized and hard to detect, which is called spear-phishing. Emotet is one of the most sophisticated and harmful malwares ever distributed by hackers via email. Since its creation in 2014, it has affected thousands of systems and continues to be a major threat for individuals and companies. Since it is continually evolving, adopting features that make it more challenging to detect, it can often bypass anti-malware software.
But hackers can also make their way into your computer through the internet. Malicious websites that look legitimate may encourage users to download files or unknowingly give them access to your device. Social media sites are also a frequently used access point because some users may relax more in these areas, making it easier for them to be tricked. SMS and messages sent through messaging apps like Telegram or WhatsApp can also contain malicious links or attachments. Messages sent through these channels usually seem legitimate and may even come from a trusted source like a friend’s email or account.
You may also encounter malware through apps that ask for too many permissions when being downloaded onto your device. This could indicate that the app is not legitimate or wants to collect additional information from your device for other purposes. It’s important to only download apps from trusted sites – like the Apple Store or Play Store – and to avoid third parties, as they may be more likely to contain malware.
External storage devices may also be a source of malware that replicates itself and spreads from one source to another. Some types of malware that a storage device can host may not require the user to do anything but plug the device into their computer, which is why it can be so successful at spreading. Hackers well versed in social engineering may leave infected storage devices in areas where people are likely to take them, hoping that the person may plug them into their computer.
What is malware used for?
Just as there are various types of malware, there are also many different reasons cybercriminals use it. Generally, a cybercriminal has an intent when they launch an attack. This intent may be focused, such as to gather specific information, or it may be multifocal, where a hacker wants to gain information before damaging a system or extorting money from their victim. In general, there are several broad uses of malware:
Data theft
One of the most common uses for malware is the theft of data or sensitive information. The end goal of the attack is often the sale of this information to third parties. Other times, this data theft may be used as part of a larger scam.
Many types of social engineering attacks rely on information about the target to be successful. Using things like spyware or keylogging can tell the hacker a lot about a target, such as their passwords or daily habits, which they can later use to perpetuate future attacks. In other cases, data theft may be used to gain access to contacts, allowing the hacker to use this information to cast a wider net. These types of attacks can occur through multiple types of malware, including viruses, fileless malware, and even adware.
Corporate espionage
Many types of malware can run undetected in the background of a system, and some of these can also spread between computers within a company’s network. This makes them useful for things like corporate espionage, where a rival company may pay a hacker to obtain sensitive information that they can use for financial or commercial gain. The hacker can use the malware to gain access to sensitive information about the corporation.
International espionage
Like corporate espionage, international espionage is designed to gather data about a specific target. In this case, however, it involves different countries and may involve governments or official agencies as well. It’s often a single country attempting to get information from a sector of another country. For example, in January 2023, officials from Latvia claimed that hackers from or with ties to Russia were attempting an espionage campaign against their Ministry of Defense using a phishing email campaign.
Vandalism
Sometimes, the hacker’s intent is not to obtain information but to destroy it or disrupt normal activities within a company. Some types of malware, like wiper malware, are designed solely to cause damage and erase or encrypt files, which can disrupt the daily operation of a company. They may also be used after a hacker has gathered the information they need, and in some cases, they may even be used to cover the tracks of the cybercriminal.
Wiper malware has also been recently used as a political weapon. In 2022, Ukraine was hit with several wiper malware attacks. The first occurred in January 2022 and focused on several government agencies’ websites. Over the next 12 months, 15 additional attacks were carried out – each with a different type of wiper malware. While most appeared rushed, they were still destructive, with an attack that knocked out military communications being the most disabling.

Illicit use of resources
Many types of malware, including viruses and botnets, can spread from one system to another. And in the case of a botnet, they can also group those systems together for the hacker to use. By hijacking a system and letting it run the scam remotely, it makes it harder to link it back to the hacker and provides the hacker access to far more resources than they may currently have. Hackers may use this type of malware to spread new attacks or for cryptomining purposes. Because many types of attacks may only be successful by targeting large numbers of people or, in the case of cryptomining, by targeting the wallets of multiple victims to amass a larger amount of funds, hackers may use hijacking to hit up more targets quickly without using their own resources.
Extortion
One of the fastest-growing uses of malware worldwide is extortion. Hackers use ransomware to take control of a computer or system, usually encrypting the files so that they cannot be used. The hacker then holds the files for ransom, usually demanding a large payment – often through cryptocurrency – in exchange for the key that will release the encrypted files. Ransomware attacks are on the rise, targeting many different sectors, including healthcare, with sensitive information they don’t want to risk losing.
A recent case of extortion to the British newspaper the Guardian was reported in December 2022, when the personal details of all UK staff members, including names, addresses, insurance numbers, and salary details, were breached in a ransomware attack. As a result, it took several weeks for the Guardian’s systems to be up and running again.
How to know if you have malware
Malware comes in so many different types with various uses that it can be challenging to determine whether your computer has been compromised. Sometimes, the signs that malware is on your computer can be subtle, making some users not immediately realize their computer has been affected. There are several signs, however, that alone or together may indicate the presence of malware:
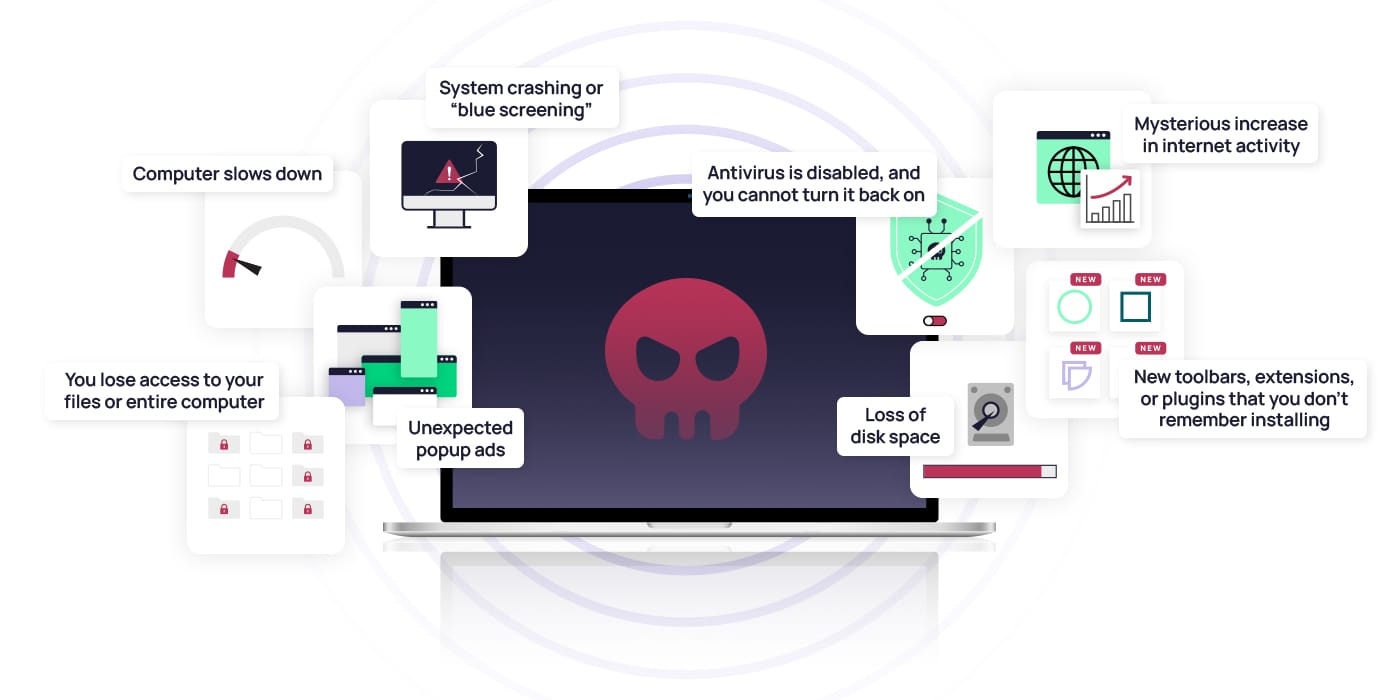
- Computer slows down: While older computers may get slower with time, if your computer experiences a sudden slow
- Unexpected popup ads: Adware is designed to flood the victim’s computer with ads. If you suddenly notice an increase in popup ads that do not look like they belong to the website you are visiting or see ads that look like spam, meaning they offer you to win prizes or money, malware may be the cause.
- System crashing or “blue screening”: If your computer is crashing or giving a blue screen frequently, this can also indicate malware. Many types of malware use a lot of data and may overwhelm your computer. Other types of malware are designed to corrupt your system, causing crashes and blue screens as well.
- Loss of disk space: If your computer suddenly loses a lot of disk space, this could indicate the presence of bundleware. This type of software bundles several types of software into one download, which may also include malware. So, you may think you’re only installing a single program when you may have inadvertently installed several.
- Mysterious increase in internet activity: If you notice your internet history is populated with sites you don’t remember visiting or find your computer uses much more bandwidth than before, it could be due to malware operating in the background.
- New toolbars, extensions, or plugins that you don’t remember installing: Malware can include programs that make changes to your computer without your permission. These are then used to better track your activity.
- Antivirus is disabled, and you cannot turn it back on: Because antivirus software may alert you to the presence of some types of malware, malware’s first job may be to disable or even erase the antivirus software from your computer so that you are unable to easily remove the malware.
- You lose access to your files or entire computer: While this is more extreme, some types of malware completely lock out the user. This may be to later try and extort money for its return or simply disrupt your usage or destroy files.
However, the absence of these signs does not always mean there is no malware on your computer. Some programs are designed to be invisible or mask themselves to avoid detection.
Malware attacks are striking hard – real-life cases
Malware remains a persistent and significant issue, with attacks affecting a broad range of targets daily. These attacks range from government agencies to corporations and have caused severe business disruptions and monetary losses. Below are just a few striking examples of various attacks:
A ransomware attack shakes the UK Postal Service
In January 2023, Russian-linked hackers executed a ransomware attack on the UK’s postal service, the Royal Mail. The attack was aimed at systems that the mail service used to track and distribute international mail. The ransomware attack was claimed by LockBit and disrupted the service of international mail for more than 20 days. While the postal service found workarounds for many of the encrypted files, it took nearly a month for full service to resume.
Crypto heist covered by a rootkit
In June 2022, a Korean-linked hacker group stole more than $100 million from the American Cryptofirm Harmony’s Horizon Bridge. In early 2023, the group managed to launder $60 million of the stolen cryptocurrency through the system. To help avoid detection, the hackers used a rootkit application on the firm’s blockchain to hide their activity and prevent detection during the initial heist. The malware entered the system through a spear phishing campaign that began a few months before the initial attack. While they were identified when they returned to launder the cryptocurrency, their attack was largely successful.
Android Users in South Korea fall prey to voice phishing attacks
Android phones in South Korea are seeing an uptick of malware known as FakeCalls. This malware masquerades as several different banking institutions and is designed to fool people into giving away details to bank accounts and credit cards. The malware is disguised as a trusted banking app on the phone and triggers vishing attacks to the user, who assumes they are speaking to a trusted bank representative. The attackers may also use the fake apps to offer loans to the victim. When the victim expresses interest in the loan, it triggers a phone call.
Russian spyware targeting Ukraine
The war between Russia and Ukraine isn’t limited to physical space. In early February 2023, Russian-linked spyware was found targeting Ukraine authorities. This is a persistent attack that dates back several years, with the more recent war also being plagued by multiple cyberattacks from Russia on Ukrainian authorities. The hackers target different Ukrainian authorities each time, usually with malware that uploads to a remote server to help cover the hackers’ tracks. The most current campaign uses spyware that takes screenshots of the computers to capture sensitive information.
5 Common myths about malware
Malware is very common and has been around nearly as long as the internet. As a result, many myths have surfaced over the years. Stay up to date on your knowledge so that you don’t fall for one:

Myth 1: iPhones and Macs do not get malware
Apple devices can absolutely be infected with malware, but they can’t be infected with malware written for a Windows machine. For a long time, people believed that because Mac users were less common than Windows users, hackers wouldn’t try to design malware for them. However, malware can infect these machines, and with the rise of Apple devices, including iPhones and iPads, more users may find that they are being impacted than before. Malware designed for Apple computers or Macs can be just as devastating if it infects your machine.
Myth 2: Phones and tablets cannot be infected by malware, only computers
Unfortunately, these devices are not safe from malware either. Mobile malware is the term to describe malware designed solely for devices, including phones, tablets, and smartwatches. Mobile malware is on the rise, with Android devices seeing some of the biggest increases each year. Adware, spyware, and banking malware are all potential issues you may encounter on a smart device. In fact, banking malware aimed at Android phones has increased 80% in recent years.
Myth 3: Malware is created by antivirus companies
Some people mistakenly believe that malware is created by the companies that make antivirus programs to trick people into purchasing the solution. This is an old myth, dating back to the first antivirus software. However, it has never been proven, and there is no evidence of it ever taking place. Malware groups are regularly watched by government agencies worldwide, and none have been linked to an antivirus software company.
Myth 4: You’ll easily be able to tell if your computer has malware
While some types of malware, like botnets, slow down your computer considerably or otherwise make themselves known if you’re looking for them, others are designed to hide their presence, such as fileless malware and some types of rootkits. Cybercriminals are constantly changing the way they operate to go unnoticed. Never depend on being able to detect malware easily because some of it may be designed to hide even from anti-malware software.
Myth 5: Malware is only dangerous if you store sensitive data on your computer
This is not true and may lead some people into a false sense of security, believing their computer is protected. However, not all attacks are aimed at stealing files. Some types of malware, such as keyloggers, can hack into your webcam or microphone or take screenshots of what you are displaying on your screen. This information can be sold to third parties or used to gain access to bank accounts or other sensitive areas. In some cases, things like screenshots may even be used to blackmail the target into complying with the hacker’s demands. Malware can be dangerous on many different levels, regardless of what you keep on your computer or what you use it for.
How to avoid malware
Malware may be prevalent, but by staying alert and taking some precautions, it is possible to protect yourself from most malware attacks. Take the following steps to protect yourself:
- Read the installation screens carefully when installing new software to avoid downloading bundleware. Bundleware is a group of software you can sometimes download unwillingly and may contain undesired software or malware. If possible, decline the additional programs. Otherwise, stop the installation process.
- Download software only from trusted sources. Always choose the original company website or download it from official app stores, such as the Microsoft or Apple Store. Websites that offer many different programs for download may be a source of malware.
- Pay attention to security warnings. If your browser warns you that a site you are about to visit is not to be trusted, it probably isn’t. Most browsers have built-in security settings that can help you avoid websites that may be a source of malware.
- Don’t click on links in emails or text messages and don’t download suspicious attachments. Even if a message or email seems legitimate, malicious software could be hidden behind it. If something makes you suspicious, contact the sender in a different way to ensure it’s legitimate.
- Avoid clicking on ads about your computer’s performance. If you notice popups or other ads warning you that your computer might be compromised and telling you to click for more information or remove the threat, these may be sources of malware. Avoid them if you don’t know where they are coming from.
- Scan external devices before using. Thumb drives, external storage, and other things you connect through USB ports can become infected with malware, particularly if you use them in public or shared areas. Scan them each time you use them to ensure you aren’t introducing something onto your system. In addition, never plug in a USB or other external storage device that you don’t know the origins of, such as those found in public places, because they may contain malware.
- Install antivirus and anti-malware programs and keep them up to date. Antivirus and anti-malware programs can help block many programs from being accidentally downloaded or scan your system and help remove any malicious software they encounter. However, they are not perfect, so always use good practices and behaviors that will help prevent malware.
- Back your data up frequently. Whenever possible, back up your system to help avoid losing access to important things if malware does sneak through.
- Use multi-factor authentication. Two-step verification and other multi-factor authentications may be time-consuming, but they make it harder for cybercriminals to gain access to your equipment.
- Stay up to date. Ensure you know the latest threat trends and stay aware so that you don’t accidentally fall victim to them.
Preventing major damage: How can companies protect themselves from malware?
Malware is a serious threat to companies of all sizes and in all countries and industries. Cyberattacks are on the rise and are expected to grow by 15% each year for the next five years, costing as much as $10.5 trillion in damages by 2025. Trends show that ransomware, in particular, is a rapidly growing global threat. Ensuring that your company can protect itself is crucial given this increase and the massive amounts of time, money, and resources that malware can steal.
As malware is constantly evolving, having a good security protocol and running anti-malware software regularly is a good start. However, as many as 82% of cyberattacks start with the human factor, training your employees can make a difference when protecting your organization against cyberthreats. SoSafe offers highly customized learning modules that are designed to turn your workers into your organization’s best firewall.
