
Adware
What is adware?
Adware, like an uninvited party guest, muscles its way into your digital world, dishing out unsolicited ads. While it plays a part in keeping some of our favorite software free, it exacts a price on your privacy, system performance, and overall user experience. Think of it as a persistent, shadowy figure constantly observing your browsing habits to serve up tailor-made ads that can manifest as pop-up ads, “unclosable windows,” or even advertisements insidiously injected into web pages.
But adware is not just a nosy intruder; it can also masquerade as a Trojan Horse, introducing harmful software or crafting openings for hackers into thousands of users’ devices. This scenario played out when half a billion users unsuspectingly downloaded free software with a hidden malicious code called Fireball, which took over browsers and altered their default search engine. In a parallel incident, cybercriminals slipped rogue adware named SimBad into the reputable Play Store, compromising over 200 apps that accumulated over 150 million downloads.
As the expansive wave of malicious adware crashes over the digital landscape, the urgency to erect strong defensive walls and cultivate the ability to sift through harmless and ill-intentioned ads becomes ever more critical to protect our technological environment.
Types of adware
At a glance, all adware types might seem similar, but they diverge in intentions: some are benign, others malicious. Recognizing the difference is crucial for a hassle-free and safe online experience.
Legitimate adware
Legitimate adware, often labeled as “ad-supported software,” serves ads as you browse the web or engage with specific apps. While some adware can be intrusive, the genuine variety is usually harmless and only comes into play when users knowingly consent to its terms during software installation. Well-known freemium services, such as Spotify and Skype, employ this model, delivering ads to their non-subscribing users.
As bothersome as they can be, legitimate ads play a crucial role when using free or inexpensive software. These ads not only generate revenue for websites and apps, but they can also offer users valuable information or promotional deals. By tailoring content to users’ preferences and browsing habits, legitimate adware helps users discover content that aligns with their interests. But showing tailored content requires knowing the user and perhaps even tracking their activity, which may sometimes teeter on the edge of illegality and privacy concerns.
Malicious adware
While legitimate adware is a tolerable bother, its malicious twin is the uninvited guest, always up to no good. Malicious software doesn’t play by the rules, displaying unasked-for and invasive ads without your consent or knowledge. The popular file-sharing app 4shared was found to do exactly this. Contrary to ethical behaviour and fair competition practices, the app with more than 100 million downloads secretly displayed ads to its users, racking up millions of dollars in profit for themselves without the knowledge or consent of its users.
But how does it find its way into your system? It could sneak in via unsafe websites or email attachments, bundle itself with other software downloads, or even pose as a legitimate app. Once installed, pop-ups spring up uninvited, banner ads appear, and sometimes, ads claim the entire screen, turning your simple browsing journey into a maze of distractions, complicating what should be a straightforward browsing experience.
Malicious adware does more than just inconvenience users; it acts like a covert detective, constantly monitoring online activities, collecting personal information, and potentially extracting sensitive data. This amassed data might be shared with third parties or used to serve tailored ads. Its secretive actions can hamper your system’s performance and, more worryingly, act as an entry point for further malware, amplifying risks to your device’s security and privacy.

How does adware work?
Regardless of the adware type, its main purpose is to generate income. But the way this revenue lands in the pockets of the orchestrators depends significantly on the adware’s intentions – whether they are legitimate or malicious. In cases where the adware operates with harmless intentions, those behind them craftily guide their earnings through an array of streamlined and clear pathways:
- Pay-per-click (PPC): This model operates on a simple principle. The adware developers receive payment each time you click on an ad. It’s a digital version of commission sales.
- Pay-per-view (PPV): The adware creators earn money each time an ad is displayed to you, regardless of whether you interact with it. They are essentially paid for ad impressions.
- Pay-per-install (PPI): This method involves bundling adware with other software. Each time the bundled software is installed on a device, the adware developers earn a payout. It’s like sneaking an ad into your software package.
In stark contrast to legitimate adware you consciously install, malicious adware typically uses trickery to invade a user’s device. This invasion usually occurs behind the scenes, bypassing the user’s consent, and through various channels:
- Bundling: This happens when you download a freeware or shareware programme, oblivious to the additional hidden software (the adware).
- Exploiting vulnerabilities: If your software or operating system has security gaps, malicious hackers can exploit these to insert malware, including certain types of adware, into your system.
- Disguised downloads: Adware can masquerade as genuine downloads on websites, deceiving users into installing it. Malicious distributors often replicate popular games, such as Minecraft, embedding adware that silently operates without the user’s knowledge.
- Drive-by downloads: This method involves the unintentional download and installation of malicious software onto a user’s device merely by visiting a compromised or malicious website, without requiring any direct action like clicking.
Once the malicious software finds its way into your device, its effects can range from simple disruptions to more serious ones, such as exposing system weaknesses that may result in hacks.
What can malicious adware do?
While the digital chaos that malicious adware causes is a noticeable fallout, it’s only the tip of the iceberg. Beneath the surface, annoyance hides a darker threat. This troublesome software can trigger a cascade of problems, from privacy breaches and data theft to the introduction of additional malware:
- Intrusive advertising: The most immediate and noticeable disturbance caused by adware is the constant display of unsolicited ads. These can take the form of pop-ups, banners, or even full-screen ads that can interrupt your browsing or use of software.
- Slow system performance: Adware uses system resources to display ads and track user behaviour, which can slow down your device. This can result in sluggish internet browsing, reduced software performance, and system instability.
- Browser hijacking: Some adware types can modify the settings in your browser, change its appearance and default search engine, open random tabs, and add unwanted browser extensions or toolbars.
- Data theft: By collecting user data and browsing habits for targeted ads, adware can facilitate cybercrimes like blackmail, phishing, or fraud. User preferences can be exploited for deceptive purposes.
- Malicious software: Malicious adware is often a delivery mechanism for a variety of malware, including viruses, ransomware, spyware, and keyloggers. This can compromise your device’s security and make it susceptible to data breaches, unauthorized access, and financial loss.
- Man-in-the-middle attacks: These attacks redirect user traffic through the adware vendor’s system, even over secure or encrypted connections. The communicating parties believe they are exchanging information over a secure connection, while the attacker can collect and manipulate sensitive information as the conversation takes place.
- Privacy concerns: Malicious software usually runs in the background and collects your data without you being aware of or consenting to it. This may include browsing habits, personal information, and sensitive data, which can be used for targeted advertising or even sold to third parties.
- Compliance concerns: Privacy concerns also sprout compliance issues. Many regulatory bodies require organisations to uphold certain safety standards to safeguard their data. So, by allowing adware into their devices that can track and analyse private user data, they are breaching those basic requirements.
- Ad blindness: Malicious adware bombards devices with irrelevant ads, leading users to overlook genuine ones and diminishing the impact of legitimate advertising campaigns.
Is adware the same as a virus?
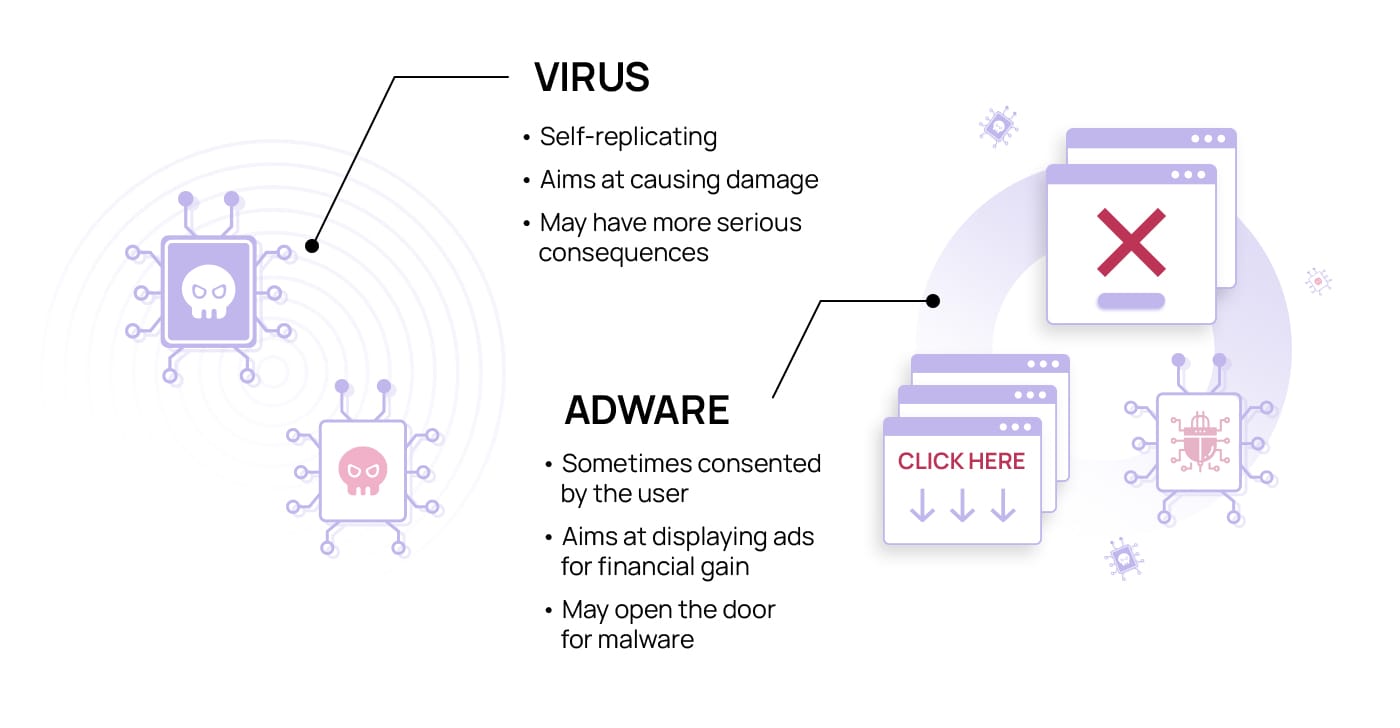
Both malicious adware and viruses are a type of malware, which is software used by cybercriminals to disrupt a computer’s normal functioning. Viruses replicate themselves, while adware is malware inconspicuously installed on a device and doesn’t self-replicate.
The distribution of both adware and viruses is done secretly, typically through bundling with legitimate software, fake ads, spam emails, or compromised websites. Some legitimate software, however, informs users about the bundled adware in their terms and conditions, which is never the case for viruses. Once installed, adware has a primary goal of displaying intrusive ads and collecting data for financial gain or data collection, while viruses are more focused on infecting and damaging computer systems and files.
As dangerous as both adware and viruses may be, malicious adware may cause intrusive ads, browser hijacking, data collection, and privacy violations, while viruses can often trigger even more serious consequences. These include data loss, encrypted data, system crashes, slow performance, unauthorized access, or even complete system failure.
Is adware illegal?
The creation and distribution of malicious software with the intent to cause harm or commit cybercrimes is illegal in most jurisdictions. On the other hand, free software that displays advertisements can be a nuisance, yet it’s perfectly legal as long as the user consents to them.
When a third-party programme secretively installs malicious adware onto your device without your consent, it becomes a matter of legal concern. Recognizing this, international organisations have integrated this into their regulations. For example, the EU’s Directive on attacks against information systems requires member states to institute penalties for distributors of such malicious software. Similarly, USA’s Computer Fraud and Abuse Act criminalizes the transmission of a programme, information, code, or command that intentionally causes damage without authorization to a protected computer.
And although regulations are already in place to protect users, hackers have become increasingly ingenious and come up with new tactics, which call for further legal measures. In March 2023, the PEGA Committee of the European Parliament pushed for stricter regulations on malicious software, specifically spyware. The increased focus on this topic highlights the importance of early detection and prevention, which is the most secure and efficient way of fighting malicious adware.
How to detect an adware infection
An unrelenting wave of intruders can throw off your online rhythm. If every click seems to spawn more ads, adware might be the cause. A few telltale signs can show if malicious adware has found its way into your device:
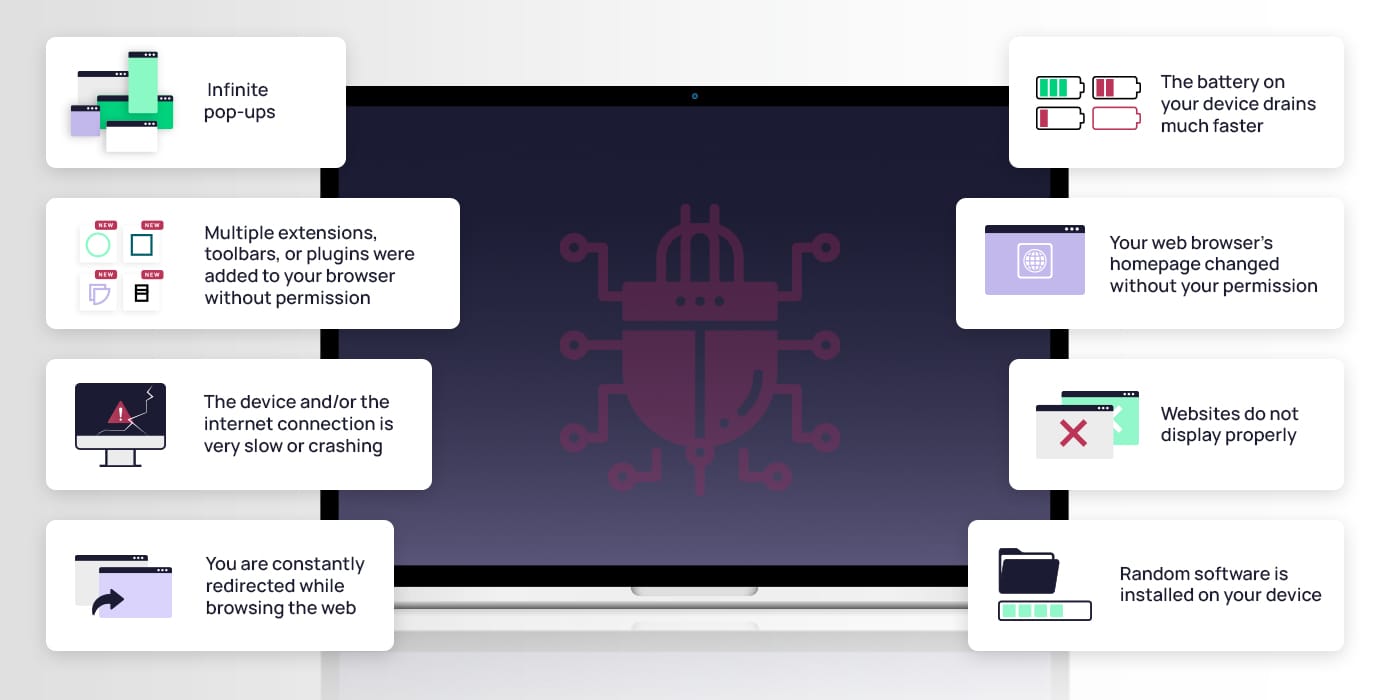
- Infinite pop-ups
- Multiple extensions, toolbars, or plugins were added to your browser without permission
- The device is very slow or crashing
- You are constantly redirected while browsing the web
- The battery on your device drains much faster
- Your web browser’s homepage mysteriously changed without your permission
- Websites do not display properly
- Random software is installed on your device
- Slow or crashing internet connection
Mobile-device-specific signs of adware include a spike in data usage, higher-than-expected data usage bills, quick battery depletion, slow functioning, longer load times for apps, unknown apps appearing without you downloading them, and numerous ad pop-ups appearing during use.
How to remove adware
Navigating the digital landscape often means contending with unwanted adware. But there’s a solution. Clearing your computer and mobile devices of such nuisances involves a balance of manual intervention and specialized software.
For MacOS or Windows platforms, you’ll need to go into your device’s system settings. The objective is to root out and remove any unknown or suspicious programmes. For mobile devices, the task is to identify and delete any suspicious apps that seem unfamiliar. Inspect your device’s permissions as well. Revoke any that appear unnecessary or excessive. And if you encounter user profiles you didn’t create, remove them as soon as possible.
Also check your browser because it can be a haven for adware on a computer or mobile device. Take the time to remove unfamiliar ad-serving extensions you didn’t install and purge your browsing data, including cookies, cache, and history.
When you complete these steps, restart your device to allow your new settings to take effect. If the adware proves stubborn or you’re uncertain about managing this process alone, specialized anti-malware tools are readily available, and professional support is always an option. Banish adware and reclaim the digital experience you deserve.
10 tips to protect yourself from adware
Navigating the sly maneuvers of adware might seem daunting, but there’s hope. Equip yourself with proactive strategies and preventative steps to maintain a smooth, ad-free journey in the digital realm. Here are some pointers:
- Regularly update your operating system and applications: Updates often contain security patches that close vulnerabilities that adware could potentially exploit.
- Download software from trusted sources: Avoid downloading software from unknown or unverified sources because these can sometimes bundle adware with their programmes. Stick to official sources like Google Play, App Store, Chrome Web Store, and others that have been verified.
- Read reviews: Everything from browser extensions to computer programmes should have reviews somewhere online. Search for user feedback and take note of the negatives because some may reveal unwanted bundles or warnings about malicious software.
- Carefully read the terms and conditions: When installing new software, always read the terms and conditions to ensure you’re not inadvertently agreeing to install adware. Be cautious if the permissions seem unrelated to its functionality or contain bundled software. If you notice anything suspicious, opt out when possible or look for an alternative.
- Be cautious with emails and attachments: Be wary of clicking on links or downloading attachments in unsolicited emails because they can contain adware. Open email attachments only from trusted and verified sources.
- Use a pop-up blocker: Many browsers offer a pop-up blocking feature, or you can install a third-party pop-up blocker. This will prevent adware that’s embedded in pop-up ads.
- Enable your browser’s privacy settings: Open your browser’s settings and check if you can block third-party and tracking activities. Most browsers have settings that can block tracking cookies and other potential adware threats.
- Anti-malware tools: While they aren’t capable of discovering every adware type and determining the impact of each like an IT professional would, anti-malware tools can effectively detect and remove some types of unwanted software. Once you install it, enable regular scans and security recommendations to ensure your device is protected.
- Back up your data: Regularly back up any important data to a secure cloud service or external storage to ensure you can recover it if a severe adware infection causes data loss or introduces other malware that can harm your systems and data.
- Stay informed: Education and prevention are the best methods of fighting any type of malware. Make sure you, your employees, or close ones are familiar with adware, common adware infection tactics, and online safety practices to avoid adware infections.
Workplace defence against adware: Training employees effectively
Advertising is a vital part of the digital ecosystem. While on opposite sides of advertising efforts, both individuals and organisations need ads, one to promote their products and services and the other to find out about them. But as long as there is profit to be made from malicious activities, evil-doers will find a way to take advantage of it, threatening the well-being of the entire marketing industry.
This is why it’s important to combat adware with proper education and training. Equipping employees with the knowledge and skills to identify and prevent adware becomes a critical line of defence in an ever-evolving digital world. Through comprehensive training programmes and continuous education, employees can recognise common adware tactics, best practices to avoid infection, and the importance of reporting anything suspicious. SoSafe’s personalized Cyber Security Awareness Training can step in and help equip your employees with the knowledge and tools to deter hackers’ attempts to gain unauthorized access through common attack methods, including malicious adware.
By fostering a security-conscious workforce, you can minimize the risk of adware-related incidents, safeguard sensitive data, and maintain a secure work environment. As the first line of defence against all malicious activities, employees contribute immeasurably to a robust and cohesive defence against the ever-evolving adware menace.


















