
Smishing
What is smishing?
Smishing is a modern form of scamming that uses text messages to gain access to sensitive information or infect devices with malware. Its name is composed of the words “SMS” (short message service) and “phishing.” Even if the term is less known, these attacks are a larger part of our daily lives than you might expect: According to EarthWeb research, in just one week in April 2022, criminals sent over 2.6 billion smishing messages globally.
Smishing, however, doesn’t only affect individuals but also organisations. Employees are also constantly targeted by cybercriminals, and successful attacks have disastrous consequences, as the Uber attack in 2022 demonstrated. In this case, a smishing attack led to a wide range of Uber’s internal systems being breached. With this evolving threat landscape, it is essential to look into what exactly smishing attacks are and how individuals and organisations can protect against them.

What are the main characteristics of smishing?
Some specific characteristics make smishing attacks particularly dangerous. For example, smishers often disguise themselves as legitimate businesses or organisations, such as banks, online stores, or government agencies, to gain their victims’ trust. This social engineering tactic entices victims into clicking on malicious links or disclosing sensitive information. But sadly, it’s not the only one. Other ways of manipulating our emotions to fulfill their goals are:

- Fear tactics: Attackers often send messages that inform the victim their account has been compromised and needs to be verified immediately. By creating this sense of loss, it’s more likely that the victim ends up acting under pressure.
- Urgency: They may also use urgency-based tactics by offering limited-time offers or discounts in the message. This also speaks to the victims’ fear of missing out, so they don’t properly reflect if the offer is trustworthy.
- Readiness to help: Scammers also impersonate close relatives or family members to trick their victims into committing a harmful act. In this way, they try to exploit their deep affection for their loved ones or the need to help them.
- Context: By looking at the victim’s social media profiles and other online information, the attackers try to use situations that could be relevant to the victim. The more targeted messages are, the bigger the chances of overriding any suspicion from the victim that it might be spam or even phishing.
Uncovering the history of smishing
Since smishing has many similarities to phishing, it is worth looking at the first phishing scams and their origin to dig into the history of smishing. The word “phishing” was coined around 1996 by hackers stealing AOL accounts and passwords. It refers to using bait, such as fake emails or websites, to “fish” for sensitive information in the sea of internet users. Replacing the “f” with a “ph” is a tribute to phone phreaking, which was used to hack telephone systems in the early 1970s and is broadly known as the first hacking attempt.
Since the smartphone became a constant companion of modern society, scammers increasingly used text messages for their schemes, especially after realizing their effectiveness: People use their smartphones on the go, increasing the chances of letting their guard down and acting spontaneously when receiving a message from a delivery service or bank institution.
With mobile service providers also struggling to find effective solutions to filter out suspicious text messages, and text messages having higher open and click-through rates than other channels, the chances are that smishing attacks will continue to rise in the upcoming years.
What is the difference between smishing and vishing?
Smishing and vishing are techniques used by cybercriminals to either gain access to sensitive information or infect our mobile devices with malware. The main difference between the two is the delivery method: While smishing involves sending malicious text messages, vishing uses voice calls to trick victims.

Smishing typically involves texts that appear to come from a legitimate source, such as a bank or government agency. The text will urge the recipient to click on a link that directs them to a fake website or download an app that contains malware.
Vishing is often a bit more sophisticated, and it can also start with a text message containing a phone number and asks users to call, although it’s more likely that the attacker calls in the first place. Once the victim is on the phone, their next move is to appeal to emotions like trust, fear, greed, or the desire to help. The danger of vishing attacks is that they can be more effective than other methods because individuals usually let their guard down when they think they are talking to a real person.
Get to know them: How cybercriminals target their victims
Due to internet-based messengers like WhatsApp, classic text messaging via SMS is becoming less popular. However, for communication between companies and customers, MFA processes, and official reminders from postal or public services, the popularity of SMS remains unbroken – and this is where the scammers come in. Since they can fake the identity of almost any reputable organisation, the fraudsters’ target audience is very broad.
Employees are often just the gateway into their employer’s company and are attacked to obtain sensitive data and damage the company. In July 2022, criminals sent hundreds of text messages to Twilio employees and former employees posing as IT or other administrators. The messages contained links that led to fake login pages hosted on domains created by the hackers. Some Twilio employees entered their credentials into these pages, which allowed the malicious actors to gain access to internal Twilio administrative tools and applications, exposing certain customer information.
Finding lists of phone numbers to send fake messages to has also become increasingly easier. Besides accessing companies’ main databases, cybercriminals also use lists sold online on the Darknet, lists made by third-party number aggregators, and social media and website crawlers.
Even though cybercriminals use different approaches to obtain sensitive data via short messages, the perpetrators’ procedure is usually similar: When people are on their phones, they are less wary. Many assume that their smartphones are more secure than computers. But smartphone security has limitations and cannot always directly protect against smishing. Here are the two most common ways to approach their victims:
Victim gives away data
- The scammer sends a text message or SMS to the victim, claiming to be from a legitimate organisation.
- The text message entices the victim to click on a link or call a number to verify their information or account details.
- The victim is asked to provide personal and financial data, such as bank account numbers, passwords, social security numbers, and credit card numbers.
- The scammer stores this data and uses it for fraudulent activities.
Malware installed
- The scammer sends a text message or SMS to the victim, claiming to be from a legitimate organisation.
- The text message entices the victim to click on a link and download an app or software update.
- The app or update contains malicious software that installs malware on the victim’s mobile device.
- The malware can track keystrokes and collect personal and financial data without the victim’s knowledge or consent.
- The scammer then stores this data and uses it for fraudulent activities.
Stay alert: The most common smishing examples
From adding a malicious link into the SMS to asking the victim to call a specific number to continue with a vishing scam: There are different ways cybercriminals use text messages to phish for sensitive information. It’s also important to realise that many cybercriminals use a combination of automated tools to send hundreds of users their text messages to avoid detection. Usually, the phone number on their victims’ phones points to an online VoIP (Voice over Internet Protocol) service, meaning it’s difficult for the average user to track the number’s location.
In combination with their advanced tools, they have perfected their techniques and have good knowledge of the most successful tactics. Below are some of the most common examples of smishing so that you can stay alert and protect yourself from falling victim to these scams:
Delivery scam
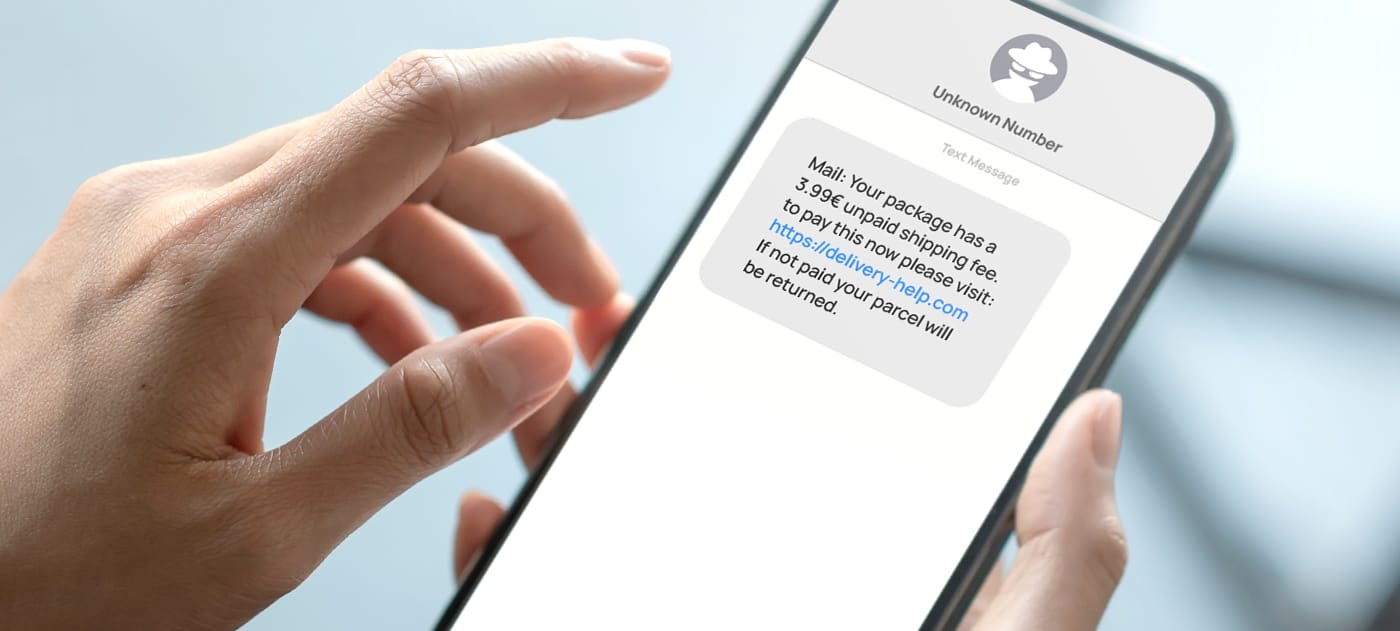
In delivery scams, attackers impersonate local postal services, Amazon, FedEx, Royal Mail, and any other delivery company to trick their victims. This is one of the most prominent text scams, accounting for over 26 percent of all SMS scams in 2021. These text scams contain links that supposedly track packages or adjust user preferences – but they either lead to spoofed websites where the recipient divulges their sensitive information or trigger the download of malware onto their devices.
Customer support smishing
Customer support smishing attacks attempt to extract confidential customer data by sending fake messages that appear to be from a legitimate customer service representative. They frequently use tech and e-commerce companies like Apple, Google, or Amazon to trick customers, and their texts warn about “issues” with billing, account access, or unusual activity.

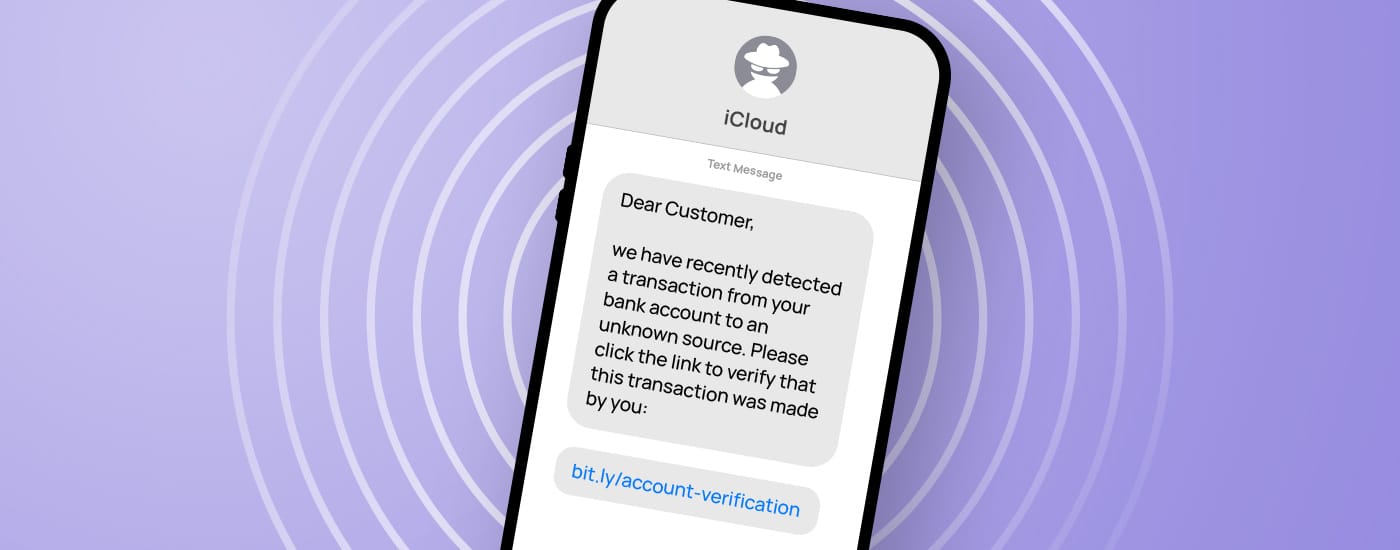
Financial services smishing
As most people use the services of banking and other financial services, attackers mask their text messages as notifications coming from these institutions. By raising fear of losing money – or even curiosity about winning a considerable amount of it – attackers know that these scams are very likely to trigger their wanted reactions from their victims.
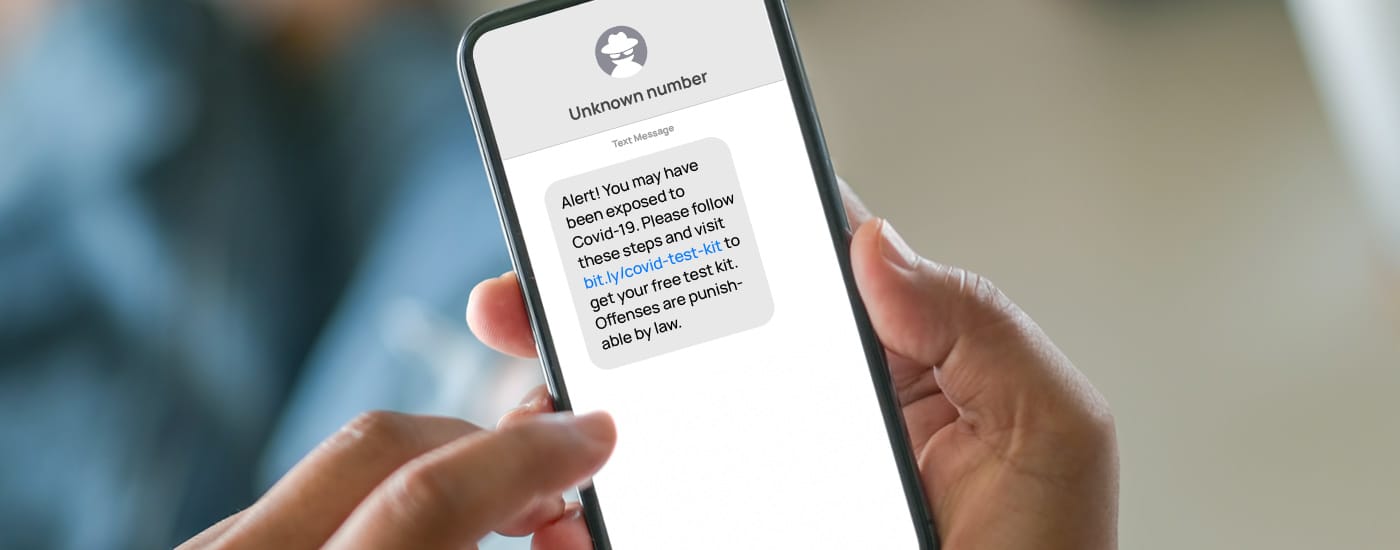
COVID smishing
Attackers are unscrupulous in their emotional manipulation tactics, and they particularly like using events that affect society as hooks for their smishing attacks. The coronavirus pandemic is one of them. COVID smishing attacks often appear to be from official sources, such as the World Health Organization (WHO) or Centers for Disease Control and Prevention (CDC), and they try to exploit people’s fear of the outbreak. In 2021, just a few weeks after the COVID-19 Omicron variant became global news, residents throughout Great Britain were contacted via text message, where they were offered free PCR tests. A spoofed screen for ordering the tests asked the victims to provide their names, addresses, and bank accounts and answer highly sensitive security questions. Even if people are less concerned about the pandemic today, new COVID scams still appear. One example is texts that claim the victim has been recently exposed to it.
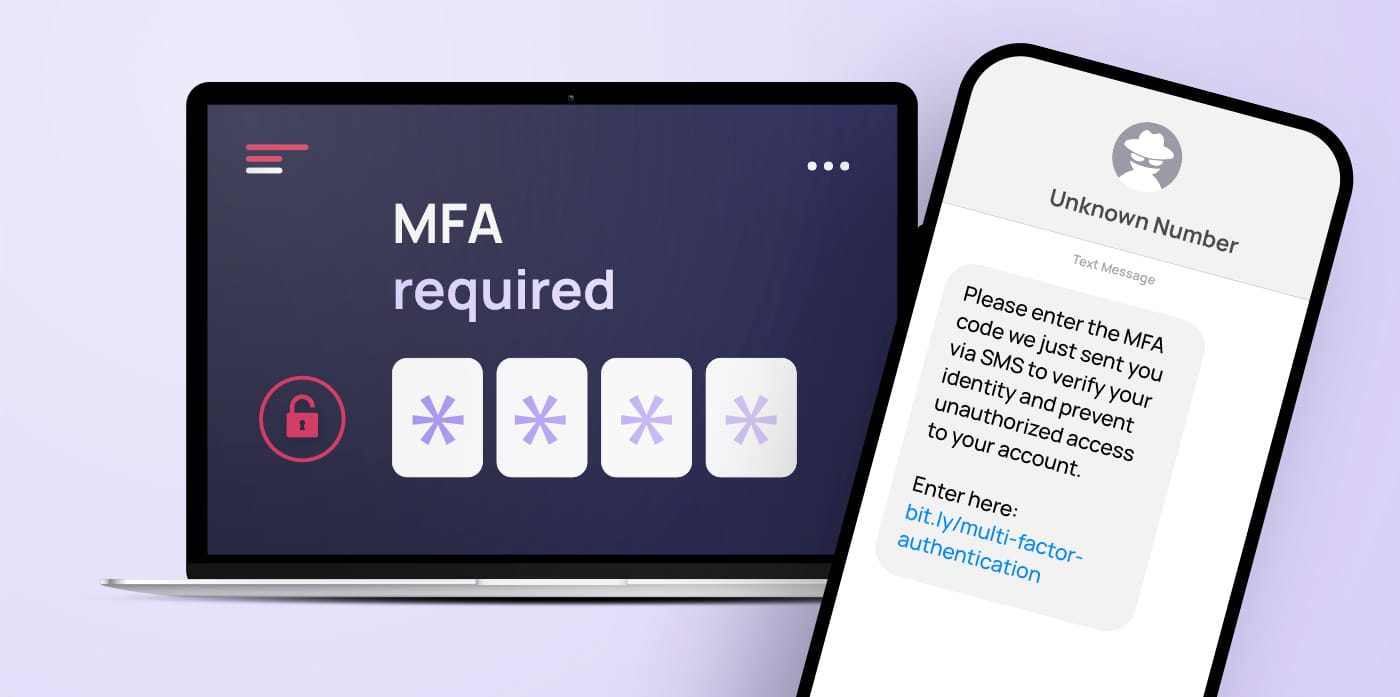
MFA codes
Since SMS is one of the most common methods used for multi-factor authentication (MFA), some smishing attacks are designed to steal these codes. The phisher may tell the recipient they need to verify their identity by telling the attacker the MFA code texted to them. The attacker triggers this code by attempting to log in as the user and then gains access once the recipient provides them with the correct code.
How to spot smishing attacks
Be on the lookout for messages containing urgent requests for personal information or suspicious links. If you receive an unexpected message, verify the sender’s identity before clicking on any links or responding with personal information. Here are some indicators that are typical for a smishing SMS:
- The message contains a link you did not expect.
- The message contains a download file you were not expecting.
- You are desperately asked for help, usually money.
- You are congratulated on winning a contest you did not enter.
- The message contains the name of your bank or a brand you are familiar with.
- You are urged to confirm your personal details via a link or phone number.
You can protect yourself from these dangerous scams by being aware of the signs of smishing attacks and taking appropriate steps to ensure your personal information is secure.
How to prevent falling victim to a smishing attack
Staying alert, being proactive, never giving out your personal or financial details via SMS, and having a healthy distrust of unusual messages are effective ways to make life difficult for scammers. Here are a few ways to reduce the risk of a smishing attack:
- Don’t respond. Other than potentially triggering malware to install onto your device, you could verify a working number for the hacker. They could then use it for other scams or include it in a list to sell on the dark web for a profit.
- Take a close look at the sender. Call the related company if you are unsure whether the sender is truly who he or she claims to be. Never call the number disclosed in the text message. Find the official one on their website.
- Be skeptical. Did you supposedly win a contest? Do you get a delivery notification for an order you didn’t place? Learn to recognise words like “immediately” and “urgent” as alarm signs, and don’t click on links if you suspect the message might be a scam.
- Silence is golden. No financial institution or reputable merchant will send you a text message asking for account information or a PIN. Sometimes, fraudsters even impersonate people in your immediate circle, such as family members, friends, or colleagues. Therefore, do not react until you are sure that the sender’s identity is genuine.
- Don’t install any app from a link. Reputable companies and organisations will never ask you for remote access to your device, such as by asking you to install an app. Don’t trust any text message that urges you to do so.
- Protect your smartphone. Software to keep your devices safe is not just for your laptop or tablet. Ensure your phone’s operating system is up to date and has the latest security features. Be careful and do not store banking information on your smartphone because what is not stored cannot be hacked.
- Raise awareness. Remember that technology is not perfect, and almost every successful scam is based on human errors. That is why cyber security awareness is so important.
For companies, e-learning and awareness training are useful ways to empower employees and make them aware of the dangers of phishing attacks via SMS. In addition to phishing and vishing, companies are well-advised to include smishing tactics in their security awareness initiatives – even if only to test which users are particularly vulnerable to this type of attack.
The threat of smishing is growing: How can companies defend themselves?
As the threat of smishing continues to grow, companies must take proactive steps to protect their employees, customers, and data. Security measures, such as multi-factor authentication and strong password policies can go a long way in helping organisations stay secure against smishing attacks. Additionally, companies should review their systems regularly to ensure they are up-to-date and equipped with the latest security technologies.
However, technology is not enough to prevent smishing attacks. We also need to secure our first and last line of defence: employees. Continuous user education and cyber security training are the best ways to reduce human risk as much as possible and prevent substantial damage. By taking these measures, organisations help protect themselves from the growing threat of smishing.
SoSafe delivers engaging learning experiences tailored to your employees’ roles and knowledge level and personalized phishing simulations that help employees become active defenders against online threats – all powered by behavioural science to make the learning journey fun and effective. Schedule a demo to see how behavioural metrics and automation work together to strengthen cyber security awareness.



















