
DORA
What is DORA?
The Digital Operational Resilience Act (DORA) is legislation by the European Commission to strengthen the operational resilience of the European Union’s financial sector. DORA aims to ensure that the financial industry can withstand and recover from cyber threats, IT disruptions, and other operational risks.
The inception of DORA wasn’t an act of foresight but a necessary reaction to the growing dependence on digital technologies in the financial realm and the need to address the potential risks associated with them. Risk management in this area becomes crucial at a time when the finance sector is heavily targeted by hackers. The latest hack of the Danish Central Bank and seven other private banks is just one example of the multiple business disruptions, significant economic implications, and potential legal consequences that cyber threats are causing on the European financial sector.
Although the cyberthreat situation is a pressing matter for the financial sector, the European Commission has allowed a two-year implementation period starting January 16, 2023. While that may seem like a long time, organisations should start preparing for its implementation to comply with the complete package of measures when the due date arrives.

Current situation of the financial sector – why DORA?
As the financial sector becomes increasingly interconnected and reliant on digital technology, it becomes more vulnerable to a variety of cyberattacks. In fact, according to Statista, the finance and insurance sector was the second most targeted by cybercriminals in 2022.
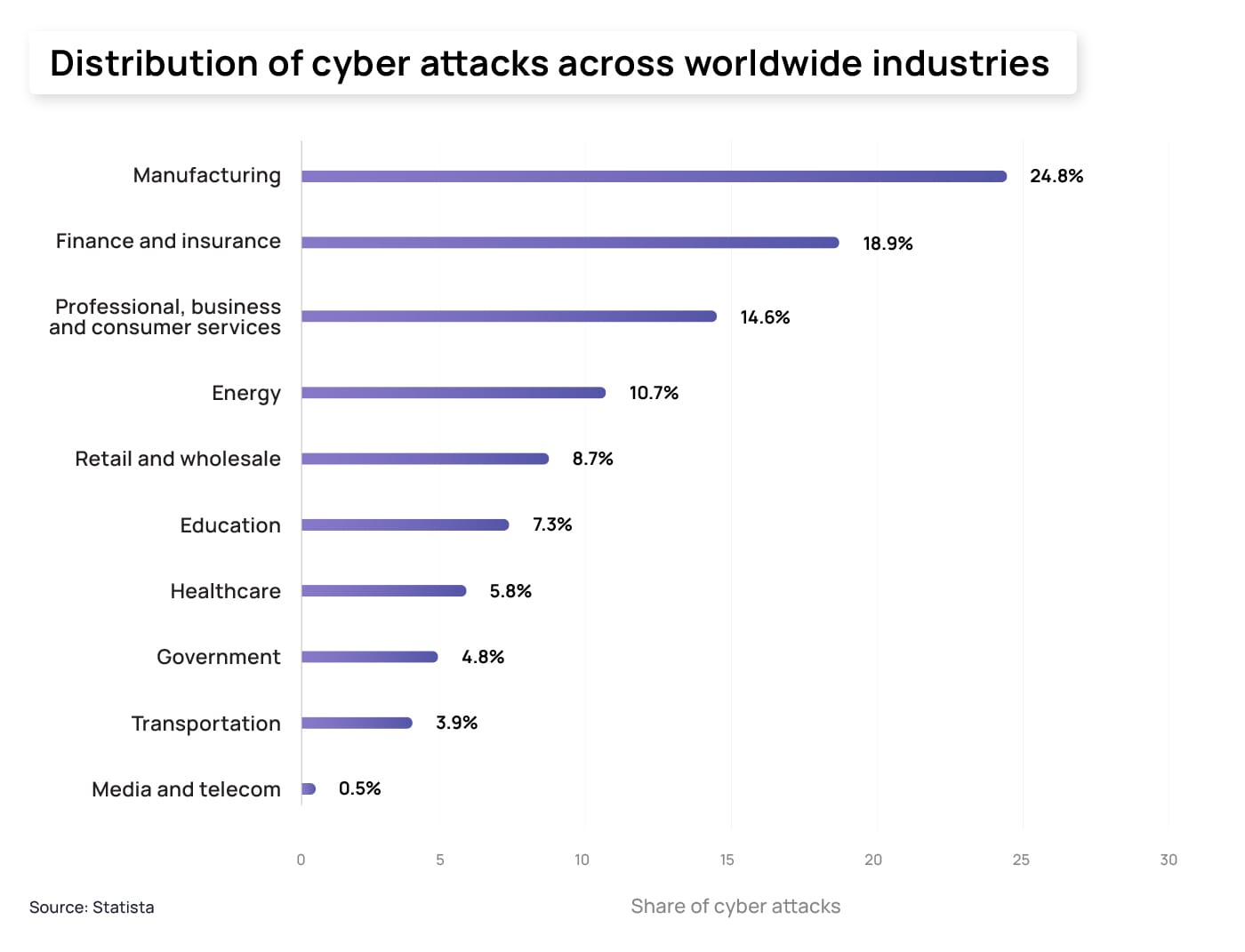
Financial entities deal with vast amounts of sensitive and confidential data, including personal financial information, account details, social security numbers, and a lot more, making them a valuable target for hackers. That’s why this sector has long known how appealing a target it was for cybercriminals. And while some organisations already have different cyber security measures in place, not all these entities are as well protected as they should be. A survey conducted by the International Monetary Fund (IMF) revealed:
- 56% of the central banks or supervisory don’t have a national cyber strategy for the financial sector at all.
- 42% of countries lack dedicated cyber security or technology risk-management regulations.
- In 64% of countries, testing is not mandatory.
- 54% do not have a dedicated cyber incident reporting regime.
- And a striking 48% don’t have cybercrime regulations.
This situation is the perfect breeding ground for cybercriminals: They take advantage of a lack of harmony and uniformity regarding security regulations in this industry to become more aggressive against the finance sector. In February 2022, the Moscow Stock Exchange and SberBank, Russia’s greatest lenders, were hit by a DDoS attack that took their website offline for three consecutive days. As a result of this and other global sanctions and events, the London-listed shares of SberBank plunged almost 80%, and the bank lost a major portion of its value. Less than a month before, one of the biggest financial institutions in Finland, OP Financial Group, was also a victim of a phishing attack that disrupted its services.
In light of these events, the importance of the Digital Operational Resilience Act (DORA) becomes undeniably clear. DORA aims to safeguard, harmonize, and unify security standards, providing a protective shield against cybercriminals for financial entities. Through its comprehensive and unified approach to digital security, DORA provides a necessary shield against the evolving cyber threats, protecting not only individual financial institutions but also the global financial ecosystem at large.
Which entities come under DORA?
DORA applies to almost all types of financial entities in the European Union. Although the first institutions that may come to mind are banks and insurance companies, many other organisations are covered by DORA as per Article 2:
- credit institutions;
- payment institutions;
- account information service providers;
- electronic money institutions;
- investment firms;
- central securities depositories;
- central counterparties;
- trading venues;
- trade repositories;
- managers of alternative investment funds;
- management companies;
- data reporting service providers;
- insurance and reinsurance undertakings;
- insurance intermediaries, reinsurance intermediaries, and ancillary insurance intermediaries;
- institutions for occupational retirement provision;
- credit rating agencies;
- administrators of critical benchmarks;
- crowdfunding service providers;
- securitization repositories;
- ICT third-party service providers; and
- crypto-asset service providers as authorized under a Regulation of the European Parliament and of the Council on markets in crypto-assets, and issuers of asset-referenced tokens.
It’s important to note that member states may opt to exclude the DORA responsibilities for some of these entities. However, if a state does so, it is responsible for reporting it to the European Commission, which will publish the information about the exceptions on its website and other publicly available sites.
DORA also requires financial entities to monitor and control the risk of third-party suppliers. This means that individuals and organisations providing services to financial entities would have to comply with DORA as well.
However, DORA is not all-encompassing, meaning some financial entities are exempt from this regulation. This includes institutions for occupational retirement provision which operate pension schemes that together do not have more than 15 members in total, natural or legal persons, insurance intermediaries, reinsurance intermediaries, and ancillary insurance intermediaries which are microenterprises or small or medium-sized enterprises, and post office giro institutions, among others. The full list can be found in Article 2.3.
Understanding DORA compliance requirements for financial entities
The DORA regulations can be split into five categories, each aimed at helping organisations improve different aspects of their cyber security system. The main components are ICT risk management; ICT-related incidents management, classification and reporting; Digital Operational Resilience testing; managing ICT third-party risk; and information and intelligence sharing. We dive into detail about each category below.
ICT risk management
DORA implies that companies have a comprehensive ICT (information and communication technology) risk management framework with clearly documented strategies, policies, procedures, and protocols for handling ICT risks. This framework should be based on recognised international standards and in accordance with supervisory guidance. Moreover, the framework should include a digital resilience implementation strategy that will, among other things, set up key performance indicators and risk metrics for the information security objectives, evaluate the current digital operational resilience situation based on prior ICT incidents and the effectiveness of current measures, and outline the communication strategy in the event of an incident.
Financial entities should also ensure that ICT risk management, control, and internal audit functions are independent. To ensure it keeps up with the latest trends, the risk management framework should be revised and audited yearly and subject to internal audits.
The Act puts the responsibility for defining, approving, and overseeing the implementation of the framework on the management body of the financial entity.
These requirements highlight the importance of having management staff with the proper cyber security awareness training: Article 13.6 of DORA stipulates that all members of the organisation, including management staff, should receive appropriate cyber security training fitted to the functions of the staff. The aim is to equip the staff with the knowledge and skills to understand and assess ICT risks and their impact on the operations of the financial entity.

This category dives deeper into the subject by requiring financial entities to use the latest ICT technology and processes that will guarantee the safety of information and put in place mechanisms to detect anomalous activities promptly. To ensure the continuity of business operations, financial entities should also have a dedicated and comprehensive ICT Business Continuity Policy that will oversee, analyse, and perform reconciliations after ICT-related incidents.
At the same time, entities should implement a system for data backup and recovery and ensure their ICT third-party providers maintain at least one secondary processing site with all the necessary features and tools to meet the entity’s business needs. Financial entities should also disclose all detected ICT incidents and vulnerabilities to help organisations learn and grow from these events.
ICT-related incidents management, classification, and reporting
The second category covers how financial entities detect, manage, and notify ICT-related incidents. Chapter III of this regulation highlights the importance of a unified system for monitoring, handling, and reporting ICT-related incidents to ensure that the root causes of these events are identified, documented, and addressed in a way that will help organisations prevent them.
To unify the detection and reporting system, DORA requires entities to classify the threat of the ICT risk and submit several reports to the appropriate authority:
- An initial notification.
- An intermediate report whenever there is a significant change in the status of the original incident or the management of the incident based on new information.
- A final report once the analysis of the root cause is finished and when there is definitive knowledge of impact figures, regardless of whether mitigation measures have already been put in place.
These reports will cover all the information necessary to determine the significance of the major ICT-related incident and assess possible cross-border impacts. Once the European authorities receive the report, they will provide guidance to minimize adverse impacts across sectors within the financial institution. The authorities will release a yearly report containing information about the number of major ICT-related incidents.
Digital Operational Resilience (DOR) testing
One of the requirements of DORA is for entities to have digital operational resilience and vulnerability DOR testing conducted by independent experts, whether internal or external, at least yearly. The purpose is to assess the preparedness of dealing with ICT-related incidents, and identifying weaknesses in the system. The testing should include a range of assessments and scans, open-source analyses, network security assessments, gap analyses, physical security reviews, questionnaires and scanning software solutions, source code reviews, scenario-based tests, compatibility testing, performance testing, end-to-end testing, or penetration testing. A risk-based approach should also be considered when conducting the testing programme. Additionally, financial entities should perform vulnerability assessments before any deployment or redeployment of new or existing services supporting the entity’s critical functions.
Managing ICT third-party risk
DORA requires financial entities that use third-party ICT services to adopt a strategy for ICT third-party risk to ensure they don’t have any vulnerabilities that may affect the entity itself. This means that financial entities should independently identify and assess all relevant risks in relation to their contractual arrangement with third parties. If there is any risk of hacks through ICT third-party service providers, inability to supervise their systems, or actual breaches, financial entities should terminate the contract with the service providers at risk. Moreover, financial entities should provide an annual report of contractual agreements for ICT services, the categories of ICT third-party service providers, the type of contractual arrangements, and the services and functions provided.
DORA also establishes the elements that must be included in contractual agreements with both non-critical and critical service providers. But to apply them, the European authorities (the European Supervisory Authorities (ESAs), Joint Committee and Oversight Forum) need to determine which third-party service providers are critical for financial entities. The critical service providers would be those who would affect the stability, continuity, or quality of the provision of financial services. Afterward, the Lead Overseer, who is appointed by the ESAs, will determine whether this third-party service provider has adequate rules, procedures, mechanisms, and arrangements to manage the ICT risks. Based on the assessment and findings, the ESAs will provide a unified reporting process and recommendations on improving the third-party providers’ cyber security measures.
Information and intelligence sharing
DORA allows and encourages financial entities to communicate among themselves and share any relevant information about ICT-related risks with trusted communities of financial entities. This open communication system aims to help financial entities enhance their digital operational resilience and minimize ICT-related threats. To ensure the protection of potentially sensitive information, financial entities should inform authorities of their participation in the information-sharing arrangements.
How does DORA relate to NIS2?
DORA and NIS2 are the two new cyber security frameworks designed to strengthen and align the cyber safety of entities across Europe. NIS2, or Network and Information System Directive for Essential Services, was introduced in December 2022, entered into force in January 2023 and must be adopted by Member States by October 2024. NIS2 is fairly similar to DORA in that it’s designed to improve the resilience of entities across Europe, but their targets are different. The goal of this directive is to improve the resilience of the public and private sectors, mainly the providers of essential and important services like telecoms, cloud computing, managed services, data centres, banking, transport, public administration, social media platforms and search engines, postal and courier services, etc. Moreover, NIS2 aims to standardize the requirements for cyber strategy and governance, detection and management of security incidents, and infrastructural and application security. On the other hand, DORA focuses on improving the resilience of the financial sector and harmonizing the way financial entities detect, handle, and report ICT-related risks.
While the scope of these two legislations is different, both are designed to harmonize legislation, protect the integrity of information, and mitigate the increasing risk of breaches due to the digitalization of everyday operations.
Timeline for meeting DORA requirements
Initially, the European Commission came forward with the DORA proposal on September 24, 2020. It was part of a larger package of measures aimed at improving the cyber security resilience of financial institutions across Europe while ensuring financial stability and consumer protection.
The final version of DORA was agreed upon on January 16, 2023, and it will have a 24-month implementation period, meaning financial entities should implement the DORA requirements by January 17, 2025. Now that the law has been passed, the relevant ESAs can develop Regulatory Technical Standards (RTS). While this may seem like plenty of time, financial entities shouldn’t wait to start implementing the framework. Instead, they can start taking specific steps toward compliance.
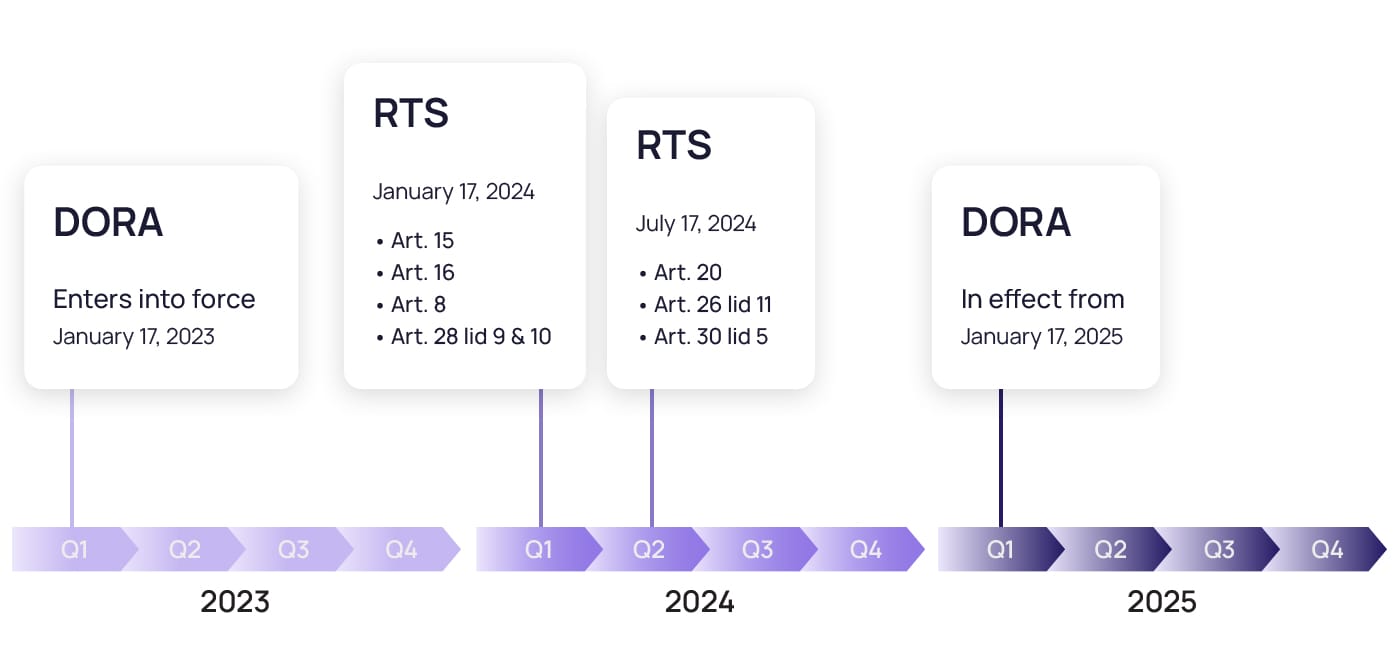
Considering this regulation and implementation period applies to both financial entities and their ICT third-party service providers, the 24-month implementation period is a good time to discuss your strategy with all involved partners, especially the critical service providers we mentioned earlier.
However, if you still feel like there are some parts of the legislation that are too unspecific and hard to grasp, Article 15 states that the European Supervisory Authorities (ESAs) and the European Union Agency for Cyber Security (ENISA) must propose common draft regulatory technical standards by January 17, 2024. These drafts will specify different parts of the legislation, from the components of the ICT response and recovery plans to the testing of ICT business continuity plans.
Next steps: How to become DORA compliant
The measures needed to comply with DORA will vary from organisation to organisation. While some financial entities will only need quick tweaks, others will need to establish a well-thought plan with multiple steps. Here are some initial steps to guide you:
- Discuss how DORA applies to your organisation with a legal advisor who fully understands the Act and its implications for your entity.
- Evaluate the current ICT risk, reporting procedure, and ability to recognise threats, for example, performing resilience testing on critical functions and systems. As a part of this step, also gauge the effectiveness of your current security awareness training programmes, if any, in addressing these risks.
- Determine which are your critical ICT third-party service providers and assess their vulnerabilities.
- Allocate the necessary budget for implementing technical changes and developing and delivering robust security awareness training programmes.
- Meet with the corresponding stakeholders in your organisation to decide on the specific measures that need to be taken internally or, if necessary, hire external providers to satisfy those needs.
- Meet with your third-party service providers to agree on the specific measures they must take or change your provider, if necessary.
- When all the measures are implemented, perform another gap assessment to ensure you have achieved full compliance.
How SoSafe can help with DORA compliance
The DORA regulation is a powerful step toward safeguarding the stability and integrity of the financial system in the face of evolving digital threats. Evaluating your needs and implementing a holistic approach that combines technical measures, operational practices, and security awareness initiatives is key to achieving compliance and reducing the cyber risk of your organisation.
One of the keys of risk management is being aware of potential threats and risks through continuous awareness training. As one of the main requirements for ICT risk management that DORA establishes, awareness training is crucial to give users the knowledge and tools to handle the broad range of cyber threats that menace today’s financial sector. SoSafe’s gamified awareness training, fueled by behavioural science, provides you with detailed – but snackable – learning modules on a great variety of threats, as well as the best security practices to stay away from threats. We also ensure that our platform breaks the language barrier with content in over 30 languages. This multi-lingual approach respects diverse linguistic backgrounds and meets the legal requirements of countries requiring native language training.
As per DORA, companies are required to put in place policies that ensure the maintenance of high standards of availability, authenticity, integrity, and confidentiality of data. The Content Management feature of our platform provides an integrated solution for consolidating your organisation’s security policies and training materials under one roof, offering the perfect blend of accessibility and efficiency. Additionally, our platform takes the heavy lifting out of tracking policy acceptance and requirements fulfillment. With SoSafe, you have a real-time snapshot of your compliance landscape, making it easier to identify gaps, monitor progress, and ensure every employee is on board.
As important as awareness and prevention is, some of the costliest mistakes are related to incident detection and reporting. A long, cumbersome internal reporting process can postpone external reporting, potentially endangering compliance with DORA requirements. SoSafe’s Reporting Button includes a feature called Phish Assist that allows any employee to quickly report security incidents, contributing to a faster detection and reporting process that will also speed up external reporting to third parties and the appropriate authorities.
Additionally, measuring the success of new risk management measures might be daunting without the proper tools. Besides, the DORA regulation requires entities to implement risk management strategies that include key performance indicators and risk metrics. By using SoSafe’s ISO 27001-compliant Human Risk OS you can track the progress of your awareness programmes and see detailed analyses, metrics and KPIs concerning human risk in your company. This way, not only will you have implemented the necessary measures to comply with DORA, but you will also see how they impact the cyber resilience of your business.



















