
Quishing
What is quishing?
QR codes have had a great run in the past few years, diffusing into almost every aspect of our lives, from looking at restaurant menus and paying for products or services online and offline to accessing websites with greater ease. While the positives of QR codes are clearly visible, both from a business and user perspective, their usage has some pitfalls.
During the 2022 Super Bowl, crypto company Coinbase developed a highly innovative advertisement that showed a QR code bouncing around the screen. Users who scanned this ad were led to download the app and, in turn, received $15 in Bitcoin. While the ad certainly worked well for Coinbase, boosting their app installations by 309 percent, it caused a stir in the cyber security community, where once more, experts expressed concern over the ease with which unknown QR codes were being scanned. The concern was certainly warranted as a few weeks prior, news of Crypto QR scams was making the rounds. Scammers used codes to force victims into withdrawing money from retirement or investment accounts by using physical cryptocurrency ATMs coupled with QR codes.
This relatively new method is called quishing – which comes from combining QR and phishing – and it’s bound to become more popular among cybercriminals as the use of QR codes becomes even more widespread. To better understand what quishing is, let’s first look at its two main components: QR codes and phishing.

What are QR codes?
QR codes or Quick Response codes are two-dimensional barcodes that a smartphone or barcode scanner can scan. These enhanced barcodes have many advantages over the traditional one-dimensional versions that we are used to seeing on supermarket products – some of them being the large volume of data they can store, the possibility to read them even if partially damaged, and the convenience and speed of data transmission. These were the main drivers of the Japanese automobile manufacturing company that invented QR codes in 1994. Their implementation allowed them to combat the impending effects of a recession by making their manufacturing process more efficient.
In recent years, there has been a tremendous rise in the usage of these codes. During the pandemic, service providers grew to rely on them to safely ensure business continuity while maintaining the social distancing rules. Because of this, users have become used to scanning QR codes and show greater willingness to do it. A recent study confirms that 99.5 million users in the US will use their phones to scan QR codes by 2025. Another study suggests that 59 percent think that QR code scanning will be a permanent part of using their phone in the future.
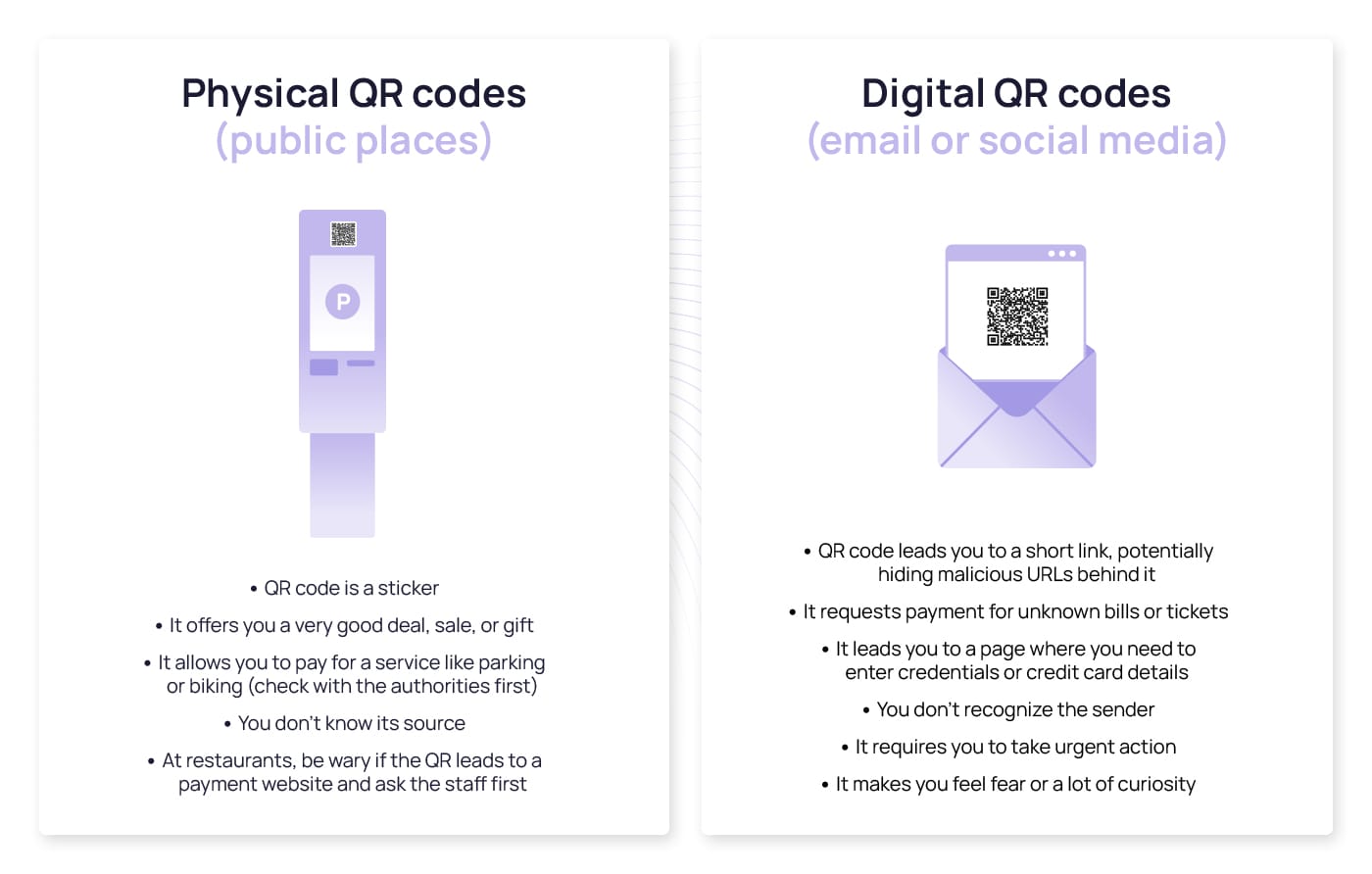
The many benefits of QR codes, including the amount of data they can contain and the possibility of scanning them both on screens and on paper – which was not possible with traditional barcodes – have made multiple industries explore its use, especially for payment processing, marketing, and advertising purposes. We now find QR codes in public places, such as billboards, restaurants, flyers and stickers, and in our phone and inbox through text messages, social media, and emails.
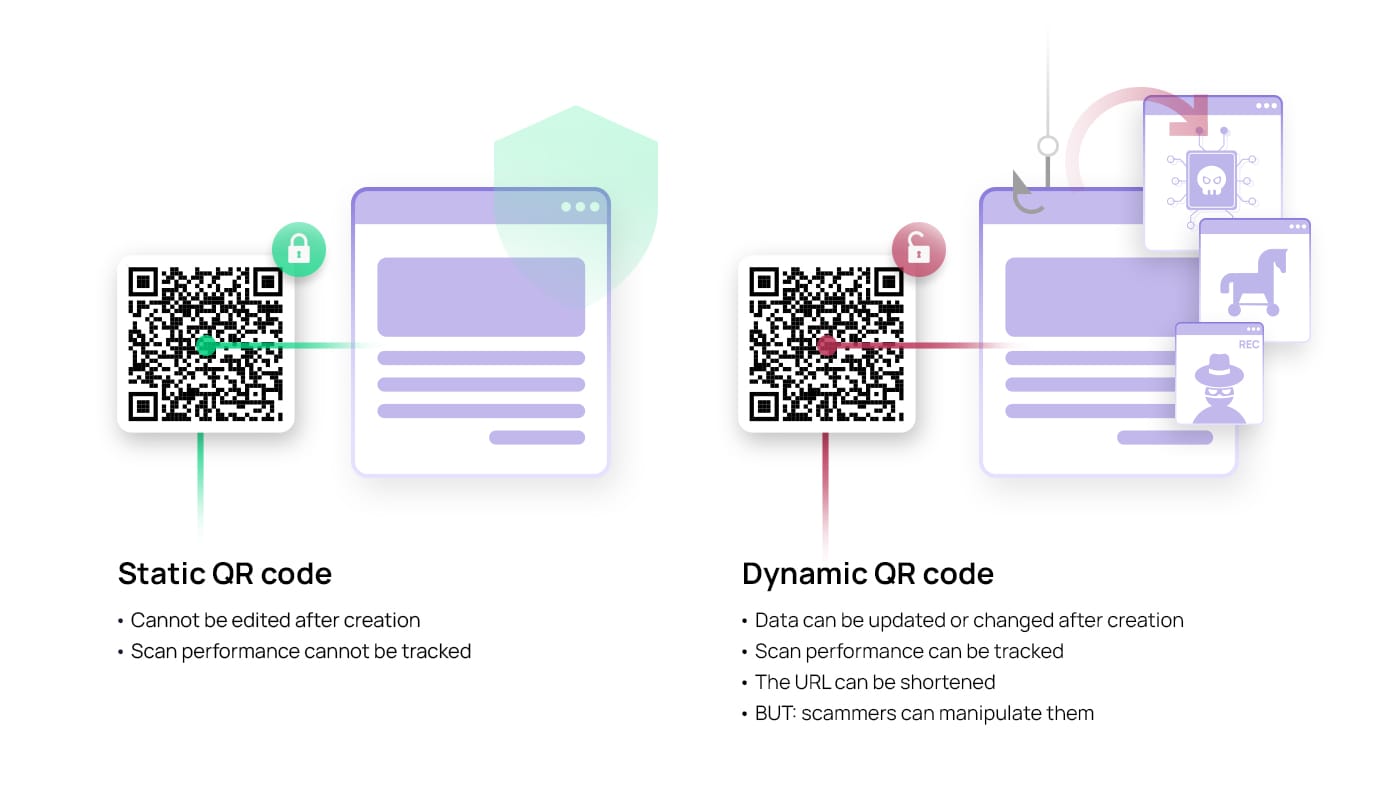
Dynamic vs. static QR codes
It’s important to realise that there are two main types of QR codes, depending on the possibility of changing the data they hold: static and dynamic.
Static QR codes are used when the encoded information is not expected to change. Once generated, the information cannot be updated or modified. This type of QR code is often used for simple tasks like sharing a website address, contact information, or a Wi-Fi password.
Dynamic QR codes, on the other hand, offer more flexibility as the data they store can be updated or changed without altering the code’s appearance. These codes contain a unique URL, which points to a server where the information is stored. When scanned, the dynamic QR code redirects the user to the URL, allowing them to access the most current information. This makes dynamic QR codes ideal for situations where the content needs to be updated frequently, such as event details, promotional offers, or real-time inventory tracking, but it also provides a ripe opportunity for scammers to manipulate legitimate QR codes by changing their source to a malicious one.
What is phishing?
Phishing is an especially popular tool for cybercriminals to gain access to valuable data. This type of social engineering attack is mostly carried out through emails. A phishing mail will usually contain a link or attachment, expecting the user to click or download either, in the hopes of stealing sensitive data, such as financial information or company login credentials. However, attackers are always looking for new, more effective ways of carrying out their attacks, resulting in new phishing tactics like vishing, smishing, and quishing – also called QR phishing.
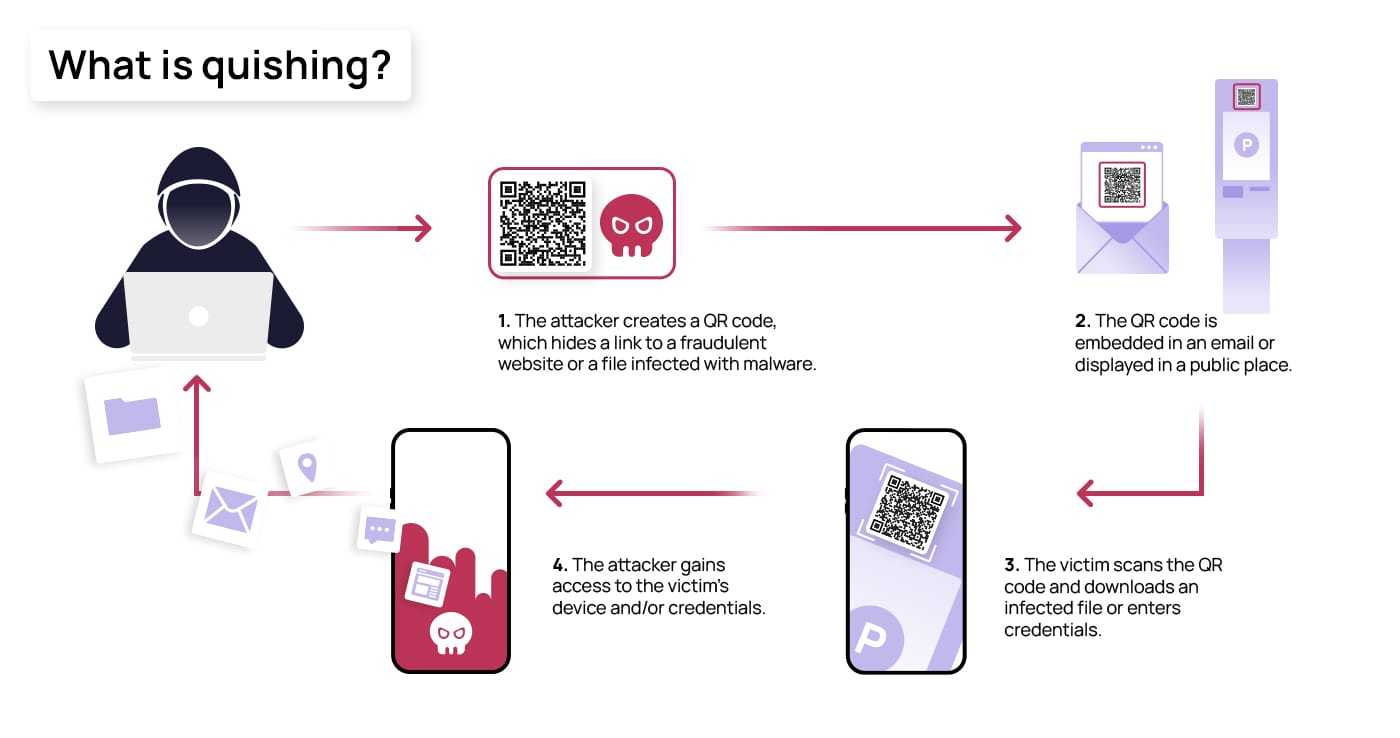
Connecting the dots: How does quishing work?
Quishing is a type of phishing attack that uses QR codes to trick people into visiting a malicious website or downloading a virus-filled document. With the option to host a variety of sources, such as links, documents, and payment portals, QR codes can be manipulated to hold malicious links, documents containing viruses, and false payment portals. As the source behind QR codes is undetectable when pasted as a plain image, they provide the perfect opportunity for scammers to bypass security filters by including them in emails. A quishing attack begins with a cybercriminal creating QR codes that lead to either a fake login page, where they collect the credentials of their victims, or to a downloadable virus or malware, which begins downloading immediately after the code is scanned. These codes can then be planted into emails as images or within attachments, but they can also be displayed in public places where victims are likely to scan them. After scanning the QR code, they are asked to provide sensitive information like login credentials or bank details or to download malicious software or apps – the download can also happen automatically right after scanning the code, further infecting their device.
A recent example of quishing involved using legitimate employee accounts, which were previously compromised, to gain access to Microsoft credentials. Attackers sent emails claiming to contain a voicemail from the account holder, which could only be heard by scanning the QR code. Upon scanning this code, employees were then directed to a realistic-looking Microsoft login page, where they unknowingly provided their credentials to the attackers. In a similar type of attack, posing as a bank, attackers sent emails to customers asking them to consent to the new data policy or review new security processes by scanning the QR code. Once the code had been scanned, customers were directed to a landing page that looked like the bank’s login page.
What is QRLJacking?
Quick Response Login (QRL) is a user-friendly authentication method that uses QR codes for logging into websites, applications, or digital services. Instead of manually entering a username and password, users simply scan a QR code displayed on the login screen of the app or website with their smartphone. This action either logs them in directly or prompts them to confirm their identity using a secondary authentication method if multiple-factor authentication is active.
Although QRL emerged as a convenient and secure authentication method that avoided having to remember long passwords, hackers found a way to use it to their advantage:
- They first initiate a client-side QR session on the website or app that they want the user to log in.
- After that, they clone the legitimate QR code and manipulate it by redirecting it to the attacker’s server.
- They then embed the QR in a fake login page mimicking the original one.
- Once the QR code is ready, they distribute the link to the fake login page through email or any other channel and make the user click the link and scan the QR to log in.
- If multi-factor authentication is not activated, as soon as the victim scans the QR code, the attacker gains access to the victim’s account.
This is exactly what happened to ING Bank, whose app allows customers to log into a second device by scanning a QR code shown in their mobile app. Cybercriminals identified this feature as an opportunity to hijack ING clients’ accounts by tampering with legitimate QR codes within the app. After falling victim to the scam, unsuspecting users quickly discovered that thousands of euros had vanished from their accounts.
QR phishing real-life examples
Resourceful cybercriminals continue to develop new strategies for leveraging QR codes in their phishing schemes. Whether it’s acquiring login credentials or obtaining your credit card details when paying for parking, they use sophisticated social engineering tactics to deceive their victims and seize their sensitive data.
Pay-to-park kiosks and parking ticket scams
Quishing poses a greater threat when focused on extracting banking and payment details. In a case from Texas, cybercriminals attached fake QR code stickers to pay-to-park kiosks, making drivers believe that they could use them to pay for parking. By scanning the codes, drivers were directed to a site where they would enter their credit card information, unintentionally providing their confidential data to hackers. Something similar happened in February 2022 in Atlanta, as drivers discovered fake parking tickets featuring QR codes on their vehicles, supposedly for fine payment. After becoming aware of the situation, local authorities warned that Atlanta does not use QR codes on their parking tickets.

Email quishing scams designed to empty your bank account
As seen in the previous sections, QR phishing emails represent another form of scamming aimed at acquiring sensitive banking information. In 2022, a QR phishing campaign in China impersonated the Chinese Ministry of Finance in an email that tricked users into thinking they could apply for a new government grant. To do so, they were prompted to scan a QR code embedded in an attached document using a mobile messaging and payment app (WeChat). Hackers often use QR codes not only because they are hard to detect by technical security measures but also because it makes the user scan it from a mobile device, which is usually less protected than computers. After scanning the code, users were led to a page to fill out the application, including very detailed information about their credit cards and bank accounts.
Fake QR code generators involved in cryptocurrency scams
Cryptocurrency addresses can be easily shared through QR codes, offering a convenient method for transferring digital assets. Crypto wallets often have built-in functionality to create these QR codes, but numerous online QR code generators are also available. In a large scam, hackers created at least nine fraudulent pages that, when prompted by the user to create their QR code address, generated a QR code leading to different crypto wallets owned by hackers. This way, every time a user shared their QR code to receive a payment, the funds would be transferred to the hacker’s crypto wallet, scamming thousands of euros’ worth of cryptocurrency from users.
How to detect a quishing attack
QR phishing is often used by hackers when regular phishing is unsuccessful, meaning it is considered a more effective method. This is because malware detectors and email filters only flag an email if they can detect suspicious URLs or attachments. Quishing emails include QR codes as plain images embedded in the email or within an attached document with a non-suspicious extension. This way, they can bypass email filters and not land in the spam folder, leaving the victim unprotected against social engineering tactics.
The enigmatic nature of QR codes makes them an attractive tool for scammers who aim to incite curiosity, primarily because their contents remain hidden at first glance. This obscurity, coupled with manipulating emotions like fear and urgency, can lead unsuspecting victims to scan malicious QR codes designed for fraudulent purposes. Scammers often capitalize on these emotions to persuade individuals into paying fake bills or fines, exploiting the very convenience and speed that QR codes offer. But emotional manipulation is not the only tactic used. Look for these signs of quishing before scanning a QR code:
Ways to protect yourself against quishing
QR phishing attacks have a lot in common with traditional phishing attacks, which is why most of the general recommendations to avoid phishing will also help you detect quishing, from carefully checking the sender’s address and detecting any spelling mistakes or impersonal salutations to previewing links before clicking them and avoid downloading any suspicious attachments. However, QR phishing exploits specific vulnerabilities that you can protect yourself against by following these recommendations:
- Verify the QR source: Avoid scanning QR codes from strangers, especially if they offer irresistible deals or discounts. If the message or email comes from an official source or a colleague, check with them as to the authenticity of the mail or visit their official website.
- Use a reliable QR code reader: Most smartphones allow you to scan QR codes with their built-in scan in their camera or with Google Lens, but if you decide to download a third-party app, ensure it is reliable. Cybercriminals have used fraudulent updates for QR scanning apps to infect users with malware in the past.
- Preview the destination URL: If your scanning app has that feature, check the link where the QR code leads you before accessing it. This will protect you against QR codes that automatically download malware on your device upon scanning them.
- Be cautious of the information you provide after scanning a QR: When prompted to a link asking for personal information or data, cross-check the logo and the full URL of the page you are on before entering anything. If possible, type the original URL in your browser instead of entering sensitive information through a link or QR code.
- Enable two-factor authentication: This extra layer of protection works exactly as it does with traditional phishing. On the off chance your information is in the hands of a cybercriminal, they will not be able to access your accounts unless you accept the second form of authentication. This also means you should avoid accepting notifications on your phone if you have not attempted to access your account, even if you get hundreds of them. This is a clear sign that hackers obtained your credentials and are trying to access your account
- Keep yourself updated with regular security awareness training: Staying two steps ahead of a cybercriminal means learning how they act and what to do when presented with a potential attack situation.
The escalating threat of QR code phishing: How can companies respond?
As cyberattacks continue to surge, QR code phishing emerges as a potent and relatively novel tactic. This phenomenon takes advantage of the fact that many individuals are unaccustomed to using QR codes, while those who do often scan them without a second thought, oblivious to the potential risks. Companies whose employees are not well-versed in the nuances of QR code phishing may risk falling for these attacks, highlighting the need for comprehensive training in this area.
SoSafe’s training programme provides an optimal solution, offering snackable, effective, and targeted content specific to QR code phishing. By equipping employees with the necessary awareness and skills, they can better identify and avoid these types of attacks, boosting their digital self-defence.



















