
MFA Fatigue Attack
What are MFA fatigue attacks?
MFA (Multi-Factor Authentication) fatigue attacks occur when an attacker manipulates the multi-factor authentication process, often by repeatedly prompting the target with authentication requests until they become fatigued or confused. Eventually, the target may comply, just as a persistent knock at the door might finally coax even the most cautious homeowner to open it, allowing an intruder to slip inside.
This cunning tactic was showcased in the recent massive breach at Uber, carried out by the notorious Lapsus$ hacking group. By obtaining the VPN credentials of an external contractor and continually attempting to log in, the attacker triggered a barrage of two-factor login approval requests. After the contractor initially resisted, the attacker cleverly posed as tech support, persuading the contractor to accept the MFA prompt and grant unauthorized access.
The Uber incident serves as a stark and sobering lesson. While MFA is an essential component of cyber security, it’s not a foolproof shield. The ever-evolving hackers’ tactics can target even the mightiest companies, emphasizing the need for continuous vigilance and a multi-layered approach to security. In the fast-paced world of digital defence, complacency can lead to a chink in the armor, a vulnerability that cybercriminals are all too ready to exploit.
How does an MFA bombing attack work?
MFA is designed to protect the system from unwanted access by requiring the user to provide several verification types. One is something you know, such as a password, another one is something you have like your phone, and the other one is something you are, such as fingerprints. It’s like having two or more keys to open the treasure chest – you need them all to unlock it.
An MFA fatigue attack aims to find a way to bypass the MFA requirements and access an account. It’s a strategic assault where the attacker bombards the user with unending requests for authentication, wearing down the user’s alertness.
But how does it work? The twist lies in psychology, not technology. The attacker exploits the human factor – fatigue – to create a vulnerability. These are the intricate stages of an MFA fatigue attack:
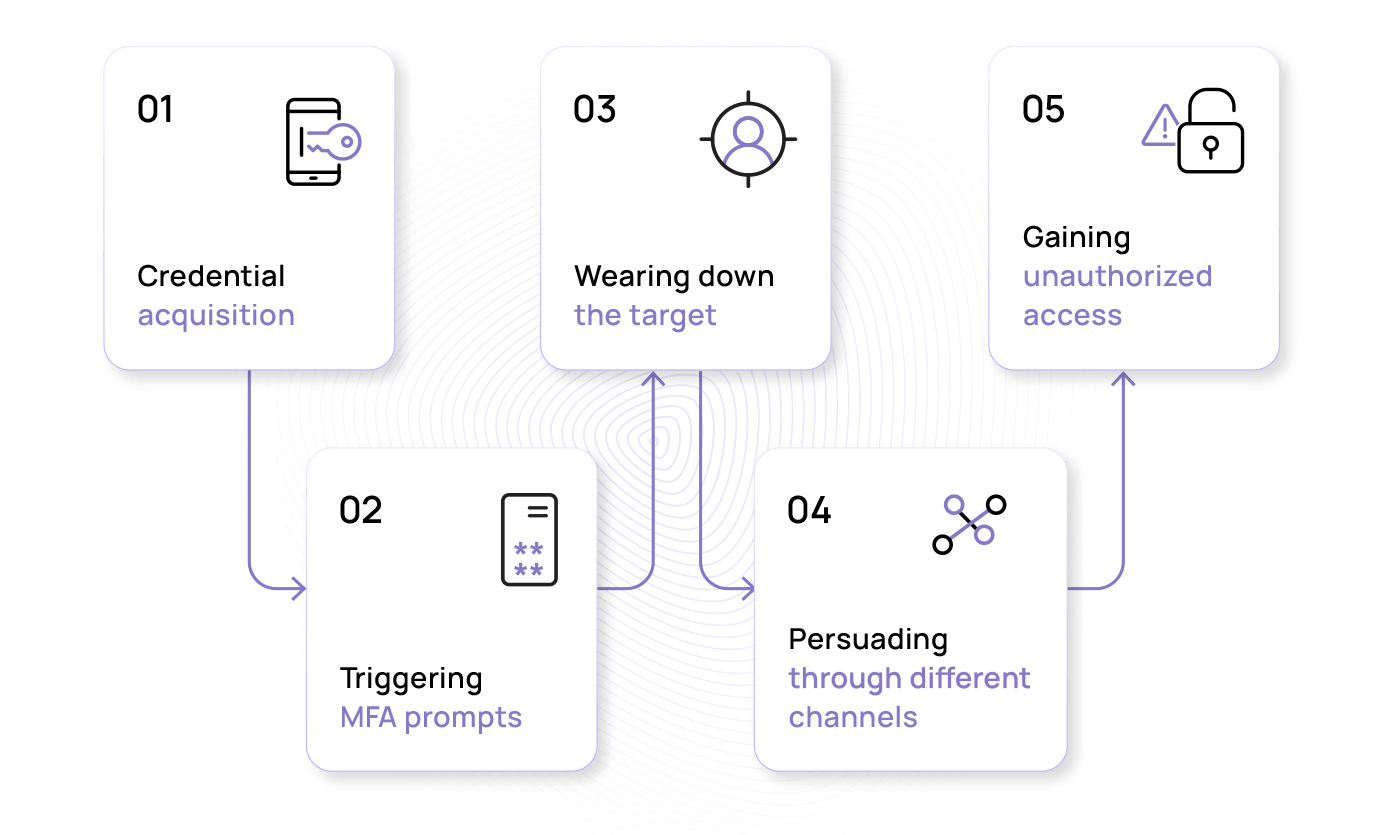
- Credential acquisition: For the MFA fatigue attack to work and enable the attackers to access an account, the account’s credentials have to be compromised. Attackers may use various methods, such as phishing, where they deceive the target into divulging their login details, or they may buy stolen credentials from the dark web. The acquired credentials provide the initial foothold needed to launch the MFA fatigue attack.
- Triggering MFA prompts: Once the attackers manage to bypass the first line of defence, they unleash a flurry of MFA push notifications. These secondary security requests usually prompt the user to input a code dispatched to their phone or email or approve an authentication request via a designated app.
- Wearing down the target: Sending one MFA notification will likely fail, so the attacker continually prompts the target with authentication requests to confuse and irritate the user with repeated notifications. This is the “fatigue” part of the attack, where the target is worn down until they eventually comply with the request. All the while, the attacker is orchestrating this sophisticated play in the background.
- Persuading through different channels: In some cases, the attacker may escalate the tactic by posing as tech support or using other social engineering methods to convince the target to accept the MFA prompt. The recent Uber incident is a prime example, where the attacker contacted the target via WhatsApp, persuading them to accept the prompt and thereby gaining access to Uber’s systems.
- Gaining unauthorized access: When the user finally submits the required validation, the gates open, and access is granted, bypassing what is often considered one of the strongest security layers. From here, they may carry out malicious activities, such as stealing sensitive information, conducting fraud, or further infiltrating the network.
When attackers gain access to the account, they can roam into different corners of your network and cause a myriad of negative side effects. They can range from data breaches to severe financial impacts and legal repercussions for both individuals and businesses.
The impact of MFA fatigue attacks: Effects on businesses
The negative effects of MFA fatigue attacks extend beyond the immediate breach. Every business has sensitive information like customer data, trade secrets, or financial records stored inside its systems. If an attacker manages to sneak through the cracks, they could snatch this information and wreak chaos within your digital realm. Let’s examine the potential outcomes of a successful MFA fatigue attack on an organisation:
- Financial loss: MFA fatigue attacks can hit your business where it hurts – the wallet. These attacks can lead to unauthorized transactions and fraudulent activities, operational disruptions, and extend to legal costs and fines. Recovering from these setbacks often demands diverting resources from growth initiatives to mere plugging gaps left by the breach.
- Operational disruption: An MFA fatigue attack can throw a wrench in your company’s gears, leading to disruptions, downtime, and confusion. Your team may struggle to navigate the aftermath, which could result in missed deadlines, stressed employees, and lost connections.
- Reputation damage: Your clients, employees, and stakeholders have entrusted you with their personal information. If your defences falter, that trust could crumble and tarnish your reputation. According to a Forbes Insights Report, data breaches have the potential to cause the most damage to a company’s reputation, highlighting the importance of protecting your data from MFA fatigue attacks.
- Customer churn: When clients experience breaches due to MFA fatigue or similar attacks, customers might feel safer taking their business elsewhere. Moreover, clients who perceive competitors as offering better security might switch loyalties, giving your rivals an advantage.
- Legal and regulatory consequences: Many sectors must comply with data protection, privacy, and other regulations like the EU Cybersecurity Act, General Data Protection Regulation (GDPR), and the Digital Operational Resilience Act (DORA). A successful MFA fatigue attack might lead to a breach of these regulations and cause legal fines and penalties.
- Lack of innovation: The fear of breaches might make you and your employees hesitant to embrace new technologies, hampering your growth and adaptability.
- Long-term impact: MFA fatigue attacks can cause an unexpected detour from your organisation’s endeavors and require significant efforts to rebuild trust, implement stronger security measures, and recalibrate your direction. This journey can be a long one, demanding patience and dedication.
Real-life MFA fatigue attack examples
Uber is not the only organisation that has fallen into the claws of MFA fatigue. Despite having cutting-edge safeguards in place, these attacks have materialized in recent times in many other organisations, showing the importance of constantly being vigilant and watching for potential threats.
The dangerous combination of vishing and MFA bombing in Cisco’s breach
In a recent cyber security incident, the renowned technology company Cisco Systems fell victim to a cyberattack, leading to a breach of its security systems. The attackers targeted an employee and, through a string of calls where they pretended to be part of a support organisation, tricked them into handing over authentication information to log into their Google account. Once the attackers received the information they needed, they enrolled new devices for MFA and managed to gain unauthorized access to Cisco’s VPN networks and escalate their privileges. By creating backdoors, they gained deeper access into the company’s servers and network, stealing their data.
The attacker UNC2447, associated with a Russia-linked group, claimed to have stolen 3,000 files with 2.8 GB of data. If true, these files may include confidential information related to the company’s operations, clients, and partners, raising concerns about potential reputational damage and a loss of trust among stakeholders. Furthermore, there’s the risk that the stolen data might be exploited for malicious purposes, such as identity theft or launching targeted cyberattacks on other entities.
Deceptive MFA prompts exploited in targeted attack on the University of Queensland
Reflecting a similar occurrence at the University of Queensland Australia, a staff member at the university became the focus of attention in an MFA bombing attack. The employee experienced an abrupt MFA notification within their staff account. Lacking any suspicion, they proceeded to approve the request. Little did they know that this seemingly inconsequential choice would set off a cascade of severe repercussions. The hacker capitalized on this access to manipulate the compromised account, dispatching deceitful emails across UQ’s staff and student body. The MFA prompt skillfully guided recipients to a fabricated Microsoft sign-in page where they stole the input credentials, heightening the complexity of the attack’s deception.
These cases hit closer to home than we may think. It’s not just companies that are targeted – MFA fatigue attacks can reach innocent bystanders as well. Imagine all the personal information we have stored across companies whose services we frequently use. If any of those companies are hacked, our personal data could potentially be compromised. To avoid this, organisations and individuals can adopt several measures to protect themselves against MFA fatigue attacks.
How to mitigate MFA fatigue attacks
Multi-factor authentication stands at the forefront of safeguarding our digital identities and organisational resources. Yet, as technology evolves, so do the tactics of attackers. Their intent is clear – to chip away the user’s focus and wear down their guard, creating a moment of vulnerability for the attacker to exploit. It’s not about cracking a code or penetrating a firewall. It’s about the psychology of exhaustion.
To prevent this from happening, organisations and individuals must keep up with both sides of the coin: the latest cyber security trends and the latest methods attackers use to bypass them. Below are some efficient tactics for battling against MFA fatigue attacks:
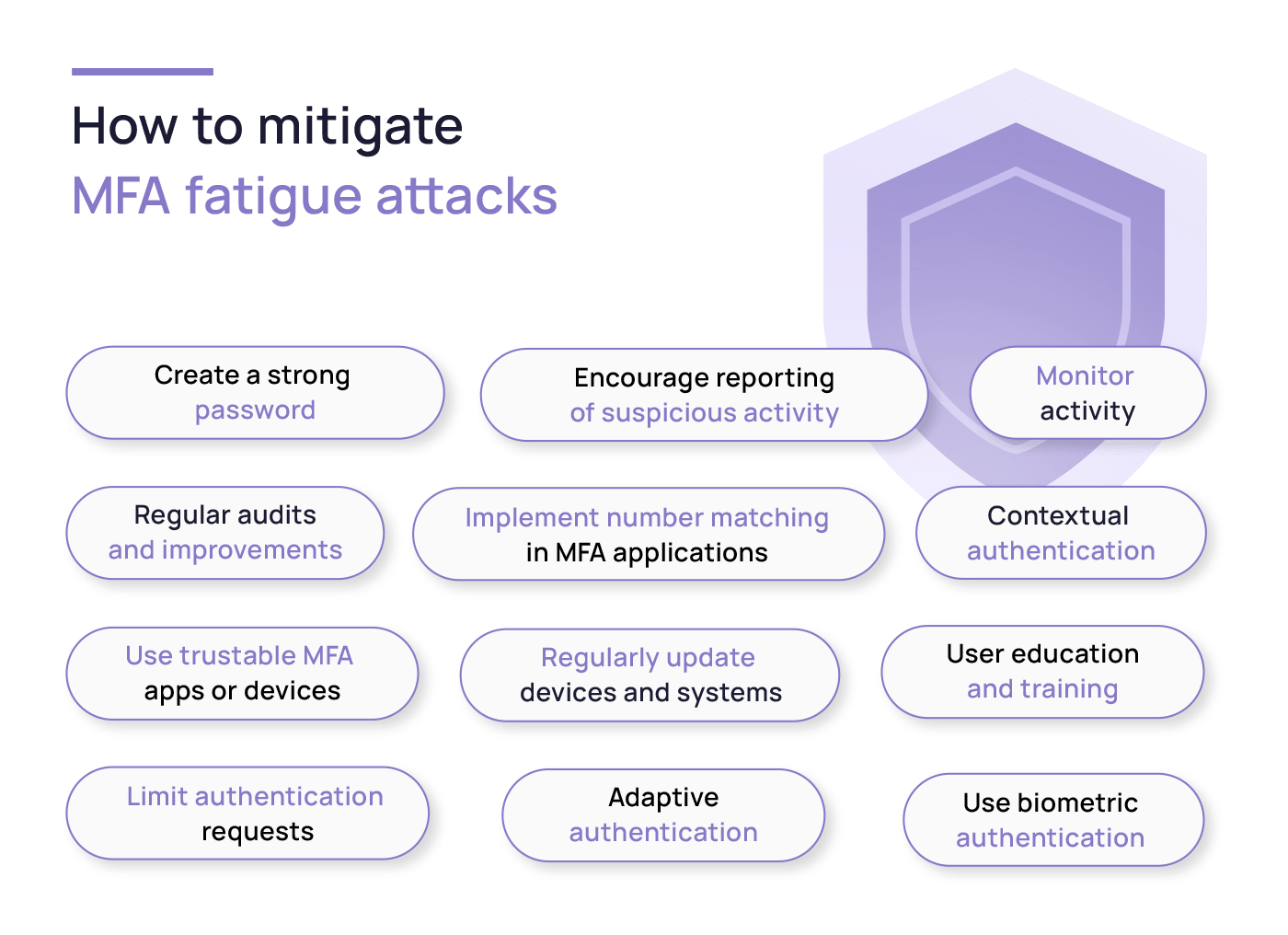
- Create a strong password: The first line of defence against hacks is a robust password. Create one that’s strong and unique for each account. Steer clear of recycling passwords – if one falls, the dominos could tumble for your other accounts.
- Use trustable MFA apps or devices: Opt for reputable MFA apps or devices from trusted providers like Google Authenticator, Microsoft Authenticator, or hardware tokens like YubiKey. They can generate one-time codes you’ll need to provide along with your password when logging in.
- Use biometric authentication: Integrating biometric authentication methods, such as fingerprints or facial recognition, adds an extra layer of defence that’s hard to crack, elevating the security of your authentication process to a whole new level.
- Limit authentication requests: Limiting the authentication requests locks out the attackers after a series of unsuccessful login attempts. By setting a cap on the number of prompts, it prevents attackers from bombarding you with requests, reducing their chances of gaining access.
- User education and training: Continuous awareness training equips your team with the knowledge to identify suspicious MFA prompts and promote proper cyber hygiene through awareness and proactive vigilance.
- Encourage reporting of suspicious activity: A straightforward reporting process for suspicious MFA prompts allows quick investigation and response. Even if you receive and don’t click an MFA request, this likely means your account is being targeted. It’s a good idea to report this to the IT team so that they can react and prevent further MFA bombing attempts against your account.
- Implement number matching in MFA applications: By incorporating number matching, users can be prompted to match a displayed number with a number sent to their authentication device. This added layer of confirmation can reduce the chance of MFA fatigue attacks by introducing an additional step that’s challenging for attackers to manipulate. The effectiveness of number matching has been supported by CISA, which recently recommended it as an MFA fatigue mitigation method. Additionally, it’s been implemented by big tech corporations like Microsoft, which incorporated number matching as a default feature in its Authentication app.
- Monitor activity: Keep a watchful eye on your account activity. Set up push notifications for any suspicious login attempts or account changes. If something seems off, take immediate action, such as changing your password or reporting the incident. Employ robust monitoring systems that keep tabs on authentication events in real time.
- Contextual authentication: Implement access controls that consider user context – factors like location, device, and access time. This smart approach ensures authentication prompts kick in only when necessary, easing unnecessary fatigue.
- Adaptive authentication: This means adjusting authentication requirements based on a user’s risk profile. Routine tasks get fewer prompts, while suspicious activities trigger more scrutiny.
- Regular audits and improvements: Routine audits of your authentication system are a must. Analyze failed attempts, successful logins, and any patterns that could hint at breaches. Keep the momentum by constantly fine-tuning your defence strategy.
- Regularly update devices and systems: Don’t forget to keep your devices, MFA apps, and operating systems updated to ensure you have the latest security patches and protections. Older versions may have vulnerabilities known to attackers, making them vulnerable to MFA fatigue attacks.
Is passwordless the solution?
Passwordless authentication emerges as a promising solution in the battle against MFA fatigue attacks, offering a pragmatic approach to enhancing security without adding complexity. This method directly tackles the factors that lead to fatigue – the constant influx of prompts and the need to manage multiple passwords.
Passwordless authentication relies on biometrics like fingerprints or facial recognition, along with hardware tokens and mobile-based methods. These personalized identifiers are unique to each individual, making it substantially harder for attackers to breach accounts. When integrated into the multi-factor framework, passwordless authentication streamlines the process. Authentication becomes smoother, involving fewer steps and less confusion. This streamlined process not only bolsters security but also promotes a more harmonious interaction between users and security measures.
As technologies like biometrics become increasingly prevalent, passwordless methods offer an adaptable and scalable security approach, catering to both individuals and businesses. However, it’s important to note that while passwordless authentication addresses MFA fatigue, it’s not devoid of challenges. Biometric data privacy concerns and the need for robust device security are the focal points in this discussion. As with any security strategy, a well-balanced approach that weighs user experience, privacy, and effectiveness is essential.

Defending against MFA bombing: How companies can enhance their security
MFA is a strong shield against cyber threats, but its effectiveness can be enhanced by addressing the human factor. Rather than relying solely on technology, organisations should understand that employees often form the primary line of defence. Organizations can bolster their security against a range of threats by prioritizing human awareness, education, and training. SoSafe’s gamified e-learning modules transform complex cyber security concepts into bite-sized, engaging lessons that are easy to digest. With its interactive quizzes and real-world content, it breaks down complex topics into digestible pieces of information without overwhelming employees or causing major interruptions in their workday.
Swift action in response to potential breaches is equally crucial during MFA fatigue attacks. Through SoSafe’s Phishing Reporting Button, your employees can send alerts to the IT department with a click of a button. For rapid incident responses, our Rapid Awareness Sofie chatbot also plays an important role since it allows managers to instantaneously send alerts to the entire company via MS Teams, rallying everyone against imminent threats.
As adversaries continue to evolve in their tactics, organisations must continuously evaluate and fortify their security strategies, ensuring they can adeptly counteract the potential repercussions of cyber intrusions. A holistic approach that combines robust technology with a keen focus on the human element holds the key to a more resilient cyber security landscape.



















