
CEO Fraud
What is CEO fraud?
Imagine receiving an email from your boss with instructions to fill out a form, provide credentials, or pay an invoice. Most people wouldn’t think anything of it, especially if their name, signature, and email appear legitimate at first glance. That’s what CEO fraudsters are counting on – that you won’t notice they are pretending to be a business executive to take advantage of your good intentions.
Unfortunately for many organisations around the world, CEO fraud attempts are often successful. According to the FBI, this is one of the most popular forms of business email compromise (BEC) attacks, a $43 billion scam with over 240,000 incidents worldwide from 2016 to 2021. This deceptive practice is increasingly challenging due to its reliance on social engineering and the ever-expanding digital footprint of organisations.
The data mentioned exemplifies the skill with which modern cybercriminals exploit trust and authority, capitalizing on the fact that most employees won’t question requests from their superiors. It’s a tale of deception, trust, and the importance of staying one step ahead in a world where even the most familiar email might contain a hidden agenda. It’s a reminder to us all: In the digital age, vigilance and education can make all the difference between a successful day at the office and falling prey to a well-executed cyber scam.
The main targets in CEO fraud schemes
One of the reasons CEO fraud schemes are so concerning is that they can target any employee in any department. No one is immune to these attacks, and unfortunately, spam filters don’t always catch them. However, some departments are especially appealing to cybercriminals, such as:

Finance department
Given their access to private business information, finance departments are an attractive target for CEO fraud attackers. Organizations that make large wire transfers or have numerous accounts are particularly vulnerable, especially if their internal policies aren’t updated to the latest security standards.
Cybercriminals do their research to come up with the best phishing techniques to resemble financial transaction protocols as closely as possible. After obtaining a relevant or similar email account, they will send a transfer authorization to the financial department, whether that be the CFO or another employee. Anyone who is authorized to submit payments is susceptible to these cyber threats.
Human resources
Human resource departments are also under fire by CEO fraudsters. Because this department has access to the entire organisation, including the employee database, it’s an easy target for cybercriminals who want to gain sensitive information. For example, HR employees at medium or large businesses open emails and resumes from hundreds, if not thousands, of applicants. If cybercriminals send a phishing email claiming to be an applicant with a malicious attachment, the HR department – and even the entire company – could suffer serious consequences.
Once inside their systems, cybercriminals could access the great variety of personal details and valuable contact information of employees and candidates the HR department collects, causing a major headache for organisations and the wider community.
IT department
While IT employees might have a greater awareness of cyber risks, the enticing rewards associated with infiltrating IT department systems make it worthwhile for cybercriminals to attempt to lure them into their tactics. All it takes is one phishing email pretending to be a trusted executive for hackers to gain access to email accounts or password management platforms. Once credentials are compromised, cybercriminals have easy access into the organisation’s digital world, leaving the entire business at risk of financial and reputational damage.
Executive team
Keep in mind that CEO fraud can extend to any higher-ups in the business. It’s no secret to cybercriminals that executives have greater authority to make financial or IT decisions. Cyber attackers also take advantage of the busy lifestyle of executives, knowing that they have so much on their plate they may not notice a fake email until it’s too late.
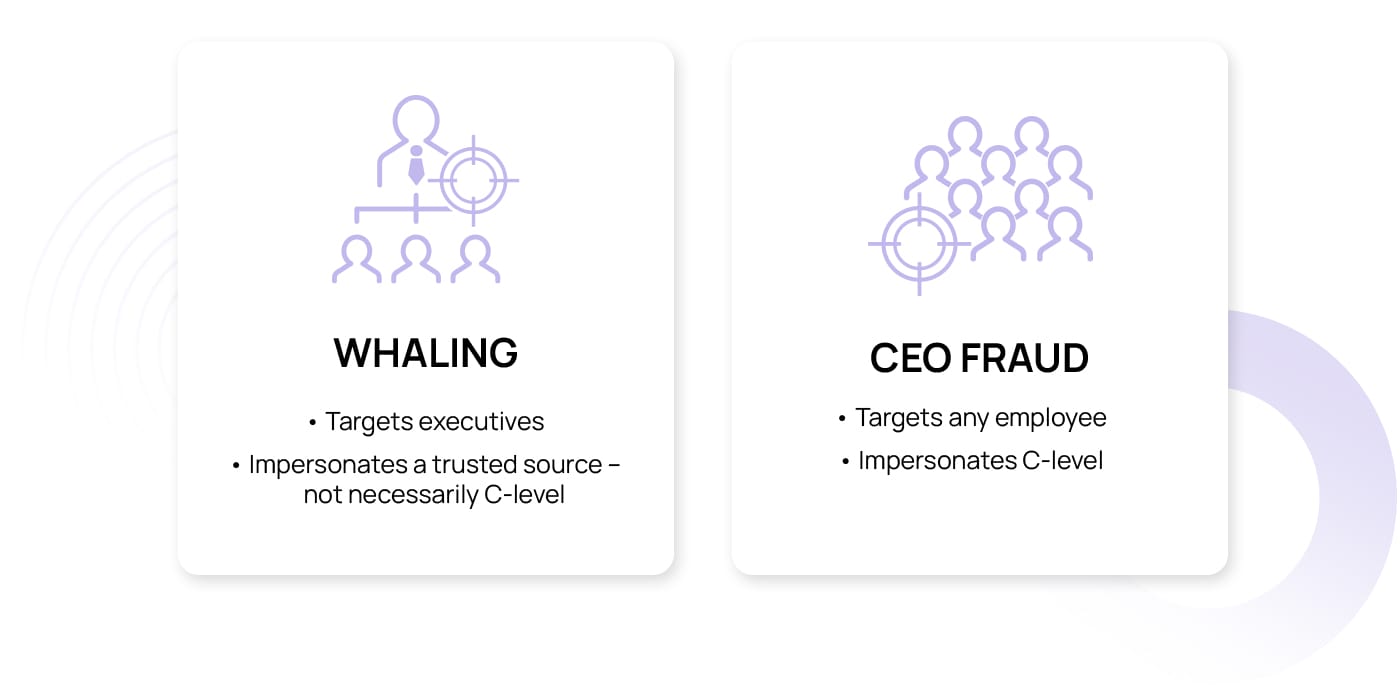
CEO fraud vs. whaling: What are the differences?
While whaling and CEO fraud are sometimes used interchangeably in the cyber security world, they refer to different hacking methods. Think of whaling as hunting the “big fish” in an organisation, such as executives or senior managers. Attackers craft sly, convincing emails that seem to be from trusted sources, attempting to lure these high-profile targets into revealing sensitive information or making unauthorized transactions.
CEO fraud takes a different angle, where the attacker plays the role of a high-ranking executive, such as the CEO, directing deceptive requests to employees within the company. While both strategies involve targeted manipulation, the confusion lies in the details: Whaling focuses on hooking the executive, no matter who the message appears to be from, while CEO fraud is all about impersonating the top ranks of the organisation. It’s a subtle but critical difference in the shadowy realm of cyber security.
Main tactics used in CEO fraud attacks
CEO fraud can take many shapes and forms, including phishing, voice cloning, and pretexting. This diversity of tactics reflects the creativity and sophistication of cybercriminals, who continually find new ways to impersonate top executives and manipulate employees. Understanding these varied approaches is essential in the ever-challenging field of cyber security, as organisations must remain vigilant against an evolving array of threats.
Phishing
Phishing stands as one of the most widespread cybercrimes, with cybercriminals using various methods like deceptive emails and social media messages to trick victims into revealing sensitive details. The latter half of 2022 witnessed a staggering 61% surge in phishing attacks, while a constant stream of scam emails, posing as CEOs, inundates inboxes daily. In the arena of CEO fraud phishing, scammers adopt the CEO’s guise, sending emails, texts, or social media messages that issue seemingly innocent instructions. Regrettably, many employees comply, failing to discern the deception and inadvertently exposing their organisation.
Voice cloning
Developments in artificial intelligence have led to a rise in CEO fraud voice cloning attacks, where cybercriminals use technology to copy a CEO’s voice and make phone calls instructing employees to provide login credentials or make a transaction. AI software makes it easier than ever to mimic someone’s voice with just a three-second sample, so employees at all levels are at risk of falling for a sophisticated scam, thinking they are on the phone with their boss.
Spoofing
Often confused with phishing, spoofing is more like a digital disguise. In spoofing, cybercriminals manipulate information to make it seem like their messages, websites, or even devices are from legitimate sources. They fake the origin of their communication to gain trust. For example, they might send an email that appears to be from a well-known company leader but actually isn’t.
Spoofing is a tactic that can be used in phishing but can also be employed in other cyberattack types. Phishing, on the other hand, is a broader strategy that can encompass various methods, including but not limited to spoofing.
Pretexting
Pretexting falls under the umbrella of social engineering, and it involves trying to trick people into sharing personal info or unknowingly getting malware by spinning a story that fits the victim’s situation. They might act like they’re stuck in a meeting or tied up in an important company project, which seems reasonable for someone in a CEO position. This makes the victim feel safe, and then the threat actors use this trust to get them to divulge private information or share account access.
Virtual conference impersonation
As the COVID-19 pandemic pushed the world toward remote work, video conferencing platforms like Zoom and Microsoft Teams didn’t just become virtual meeting rooms. They transformed into new arenas for CEO fraud. These platforms have witnessed a surge in virtual conference impersonation attempts, catching the attention of the FBI, who have noted growing complaints.
Here’s how the scheme unfolds: Cybercriminals craft phishing emails that seem to be from the CEO, complete with instructions to join an urgent video conference. Once inside the call, the scammer assumes the CEO’s identity, even using their headshot as a profile picture, and conveniently blames technical glitches for the lack of live video or audio. Under this convincing disguise, they press employees to execute an immediate wire transfer or comply with other malicious requests.
Smishing
Smishing plays a crafty role in CEO fraud, turning the everyday text message into a digital Trojan horse. Masked as the CEO, the smisher sends urgent requests, such as “Transfer funds now!” or “Click this link immediately!” Thinking that they are talking to their boss, victims will mistakenly respond to these texts and act on the requests, not realizing the scam until it’s too late.
Real-life examples of CEO fraud attacks
In the world of CEO fraud attacks, no organisation is spared. From the largest corporations to the smallest community groups, the threat is universal. Whether it’s a tech-savvy enterprise or modest local store, CEO fraud sees no distinction, making the threat all the more potent.

French companies targeted by a criminal network
In December 2021, €38 million was lost in just a few days due to a complex CEO fraud campaign. A French and Israeli criminal network impersonated the CEO of a company specializing in metallurgy. Fraudsters sent an urgent request to the company’s accountant, asking for a confidential transfer of €300,000 to a Hungary bank. The scam wasn’t discovered for a few days, and an investigation revealed where the call from the “CEO” originated from. Unfortunately, the cybercriminals struck again, convincing a real estate developer to transfer €38 million abroad, thinking it was going to a reputable French accounting firm. More impersonation attacks followed, with authorities eventually arresting eight suspects.
Japanese company tricked in deep fake CEO fraud attack
CEO fraud attacks are happening all around the globe, with money being a prime motive in many cases. A Japanese company learned the hard way in 2020 when a call from the company director instructing the manager to authorize a $35 million funds transfer for an acquisition that turned out to be fake. This elabourate scheme used pretexting to set the stage, with the cybercriminals setting up emails from a lawyer named Martin Zelner, who had been appointed to coordinate the acquisition, along with the branch manager. In reality, the fraudsters took advantage of deep voice technology to effectively clone the director’s voice. What seemed like a legitimate business move was, in fact, a carefully orchestrated heist. The realization came too late, and the money was gone.
British energy company fooled by fake CEO call
Global energy companies are an attractive target for cybercriminals, given their expansive financial portfolio and industry dominance. And with the rise of AI voice-mimicking technology, energy CEOs have become a much easier target for scammers. In 2019, a British energy company executive received a call from his boss authorizing a $243,000 transfer. Only after the transfer was made did the company discover their leader’s voice was imitated on the call, and the money had actually been deposited directly into the cybercriminals’ bank account.
How to detect a CEO fraud attack
Business email compromise (BEC) like CEO fraud puts organisations’ reputations and finances at risk, so identifying and stopping these attacks is a top priority. Here are some of the top tips for detecting a CEO fraud attack.
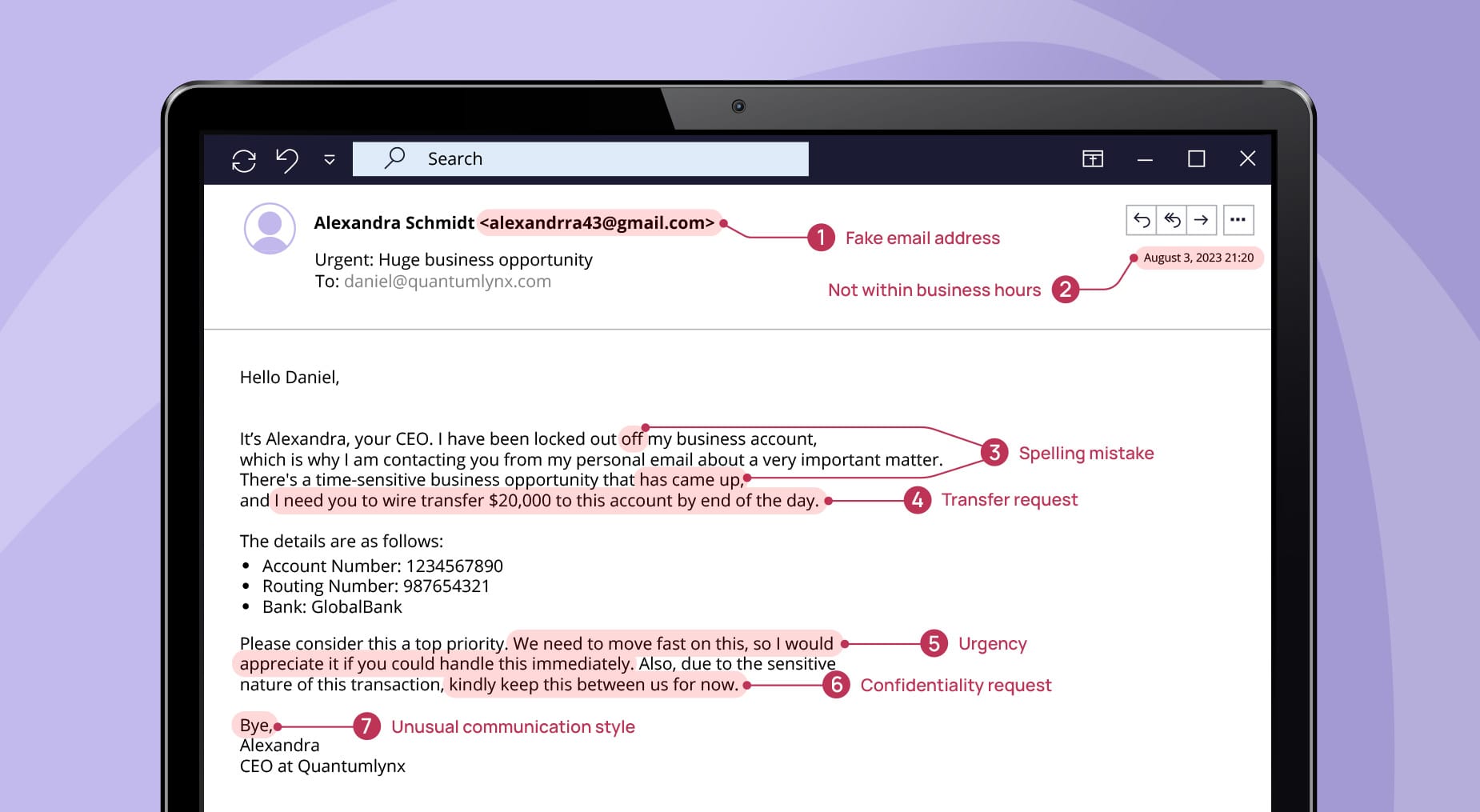
- Urgent request. CEO fraud emails often create a sense of urgency and make an unusual request, which may go against company policy. If you receive such a message, even if it appears to be from your CEO or another executive, be skeptical. It’s better to double–check in person or over the phone if you can.
- Private address. If the CEO or another executive sends a request from a personal or private email address that’s out of the norm, it’s a red flag. They would usually use their official company email for business matters.
- Unusual communication style. Pay attention to how your CEO typically communicates, as any deviation from that could be a sign of CEO fraud. This includes tone, language, specific phrases they usually use, or their email signature.
- Transfer requests. CEO fraud often involves requests for money to be transferred quickly via wire transfer. If you receive an email request like this, always verify it personally before proceeding.
- Messages after business hours. Many scams occur outside of normal business hours to reduce the chance of immediate verification. If you receive a late email or text message, verify its authenticity through another form of communication before acting on any requests.
- Request for confidentiality. Be on the lookout for emails or text messages instructing you to keep the transaction a secret, especially from specific people or departments.
- Spelling mistakes. Poor spelling and grammar can indicate a scam, although some sophisticated attacks may not have these errors, especially with the rise of generative AI.
- Domain changes. Many CEO fraud attacks use an email address with one or two letters off or a different ending like “.net” instead of “.com.” Look at the sender’s name and the full email address the message came from.
What to do if you are a victim of CEO fraud
With cybercriminals growing increasingly skilled in their attack methods, it’s not always possible to identify a CEO fraud campaign until the damage is already done. That’s why it’s important for the entire organisation – from executives down to entry-level employees – to be aware of the risks and the measures to take if they encounter CEO fraud.
For employees
If you suspect you’ve fallen victim to a CEO fraud attack, it’s important to report it to the security team as soon as possible. Remember that it’s okay to make mistakes, and the sooner the situation is addressed, the better any potential consequences can be mitigated. Once you report the incident, disconnect your computer from the network to help contain the issue. Follow your company’s specific reporting procedures, which may include filling out an incident report.
After the immediate threats are handled, review the event with your IT department to understand what happened, ensure your security software and systems are updated, and stay extra vigilant for any suspicious activity moving forward. Consider taking any available cyber security training to better protect yourself and the company in the future.
For companies
If a company falls victim to a cyberattack, immediate and coordinated action is essential. The first steps are to isolate affected systems to prevent the spread of the attack and notify the IT team for an emergency response. Contact external experts if needed and follow your incident response plan, which should include informing upper management and legal advisors.
Communication is key: Notify affected partners and staff about the breach without revealing sensitive details that could exacerbate the situation. Once the threat is contained, conduct a thorough investigation to understand the scope and origin of the attack. Use the findings to improve your cyber security measures, update software, and patch vulnerabilities.
Staff should be re-trained on the latest cyber security best practices to prevent future incidents. Finally, a detailed post-incident report should be created to evaluate the response and make recommendations for future actions. If required by your local legislation, consider reporting the incident to the authorities.
How to prevent CEO fraud
As CEO fraud surges, painting a troubling picture with cybercrime losses rocketing past $10.2 billion in 2022, the call for prevention and mediation resounds across organisations of all sizes. CEO fraud doesn’t merely dent the bank account. It shakes the very foundation of trust between employer and employee. For those businesses determined to halt these attackers in their tracks, the journey begins with a commitment to vigilance and a pursuit of robust measures. Here are some key strategies that can act as shields in the ongoing battle against CEO attacks.
For employees
Employees serve as a critical line of defence for any organisation. To enhance the overall security, it’s important for them to follow specific guidelines that contribute to keeping the company safe.
- Always check the full email address of the sender, not just the display name. Scammers can spoof the display name to look like someone you know.
- Always verify requests for payments, purchases, and sensitive information in person or via a phone call to the person supposedly making the request. Do not use the contact information provided in the suspicious email. This is especially important for large or unusual transfer requests.
- If something in an email or communication seems off, even if you can’t pinpoint what it is, report it to your security team or supervisor.
- Know your company’s procedures for payment requests, particularly those from the CEO or other executives. Unusual requests outside these procedures, especially those with large lump sums, are a red flag.
- Knowledge is your best defence. Follow any security awareness training your company offers to understand the latest threats and tactics used by scammers, including CEO fraud.
For companies
Developing a security plan against CEO fraud will reduce the possibility for companies to crumble after an attack and help mitigate its consequences. Some of the measures that organisations can take are:
- Invest in company-wide awareness training. Train all staff, especially those in finance or who have the authority to transfer funds or share sensitive data, on the existence and methods of CEO fraud.
- Confirm requests for transfers. A policy should be established where all requests for fund transfers are confirmed by another method of communication. A phone call to a trusted number or a face-to-face conversation can make a difference.
- Regularly monitor and audit transactions and financial operations to identify any irregularities or suspicious activities.
- Implement multi-factor authentication so that there are at least two forms of verification to access accounts, systems, and private information.
- Keep systems updated. Regularly update all systems, including email and financial systems, to protect against vulnerabilities scammers could exploit.
CEO fraud in the age of technological innovation: How companies can safeguard their interests
CEO fraud takes advantage of the trust employees have in their business leaders, with cyberattackers impersonating company executives and asking staff to fulfill fraudulent requests. These attacks have evolved to exploit a range of communication channels, from emails and text messages to advanced voice-cloning technologies. Given the complexities and high stakes involved, a strong focus on prevention strategies and employee education is not merely advisable but essential for safeguarding an organisation’s assets and reputation. SoSafe’s e-learning platform offers personalized awareness training to ensure your team is on the same page about CEO fraud and similar phishing and social engineering attacks. But we know practice makes perfect, so our phishing simulations allow you to put your knowledge into practice and test response protocols.
With comprehensive cyber security solutions and support, your organisation can safeguard against these attacks from the ground up. Ensure your entire team is protected with SoSafe’s Phishing Report Button, allowing you to boost employee awareness and knowledge even further by giving them the tools to report suspicious emails and CEO fraud attempts with one click. After reporting the attack, our new Sofie Rapid Awareness chatbot will timely inform the rest of the company via Teams to avoid anyone else falling into the trap. Together, these resources can take your cyber security game to the next level, ensuring you have the right tools to combat CEO fraud attacks in an ever-evolving threat landscape.


















